Day 12 Challenge Writeups



Vulnbydefault Day 12 Writeup
Reversing - Writeups
Gatekeeper
open the binary in IDA
main
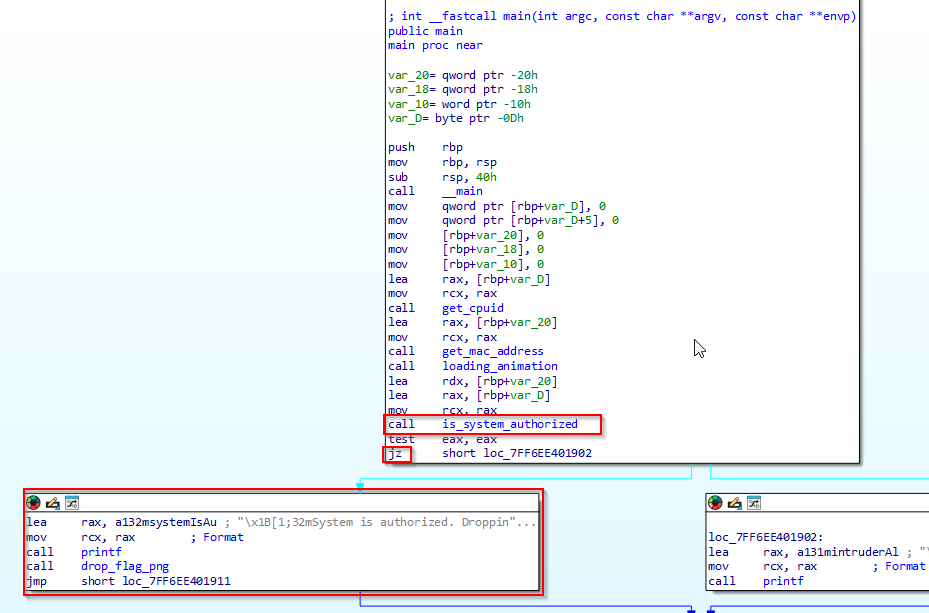
in the main function we can see that, a is_system_authorized function is called, if the the system is authorized it will drop the flag png on the system, we just need to make sure it follows the left tree,
Patching the binary:
You can do this by clicking the Edit tab->Patch program.
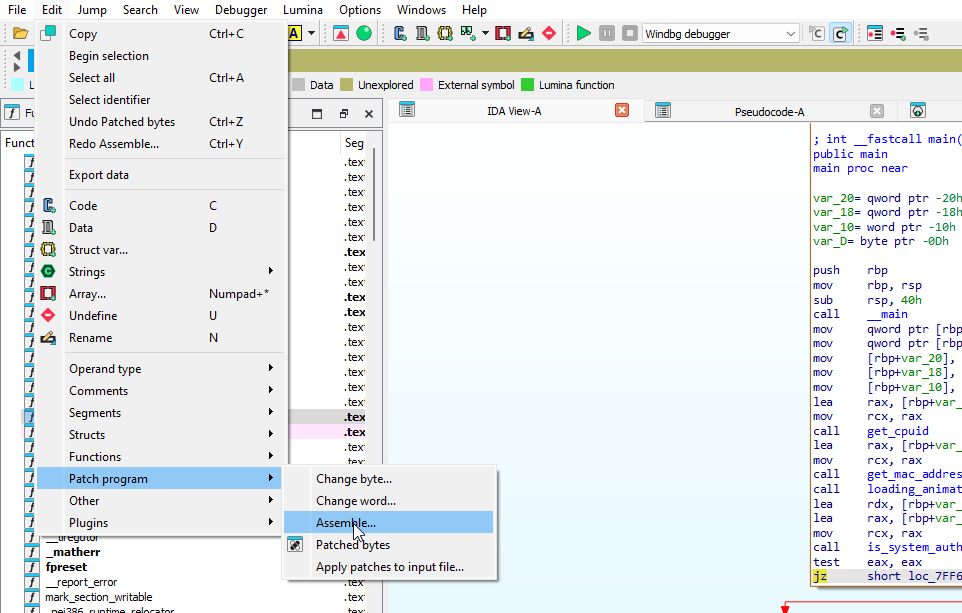
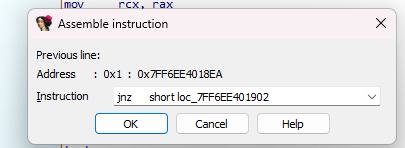
change the jz to jnz and press ok
now again go to Edit tab->Patch program→Apply patches to input file
analyzing the drop_flag_png
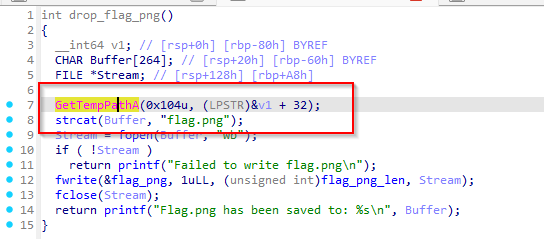
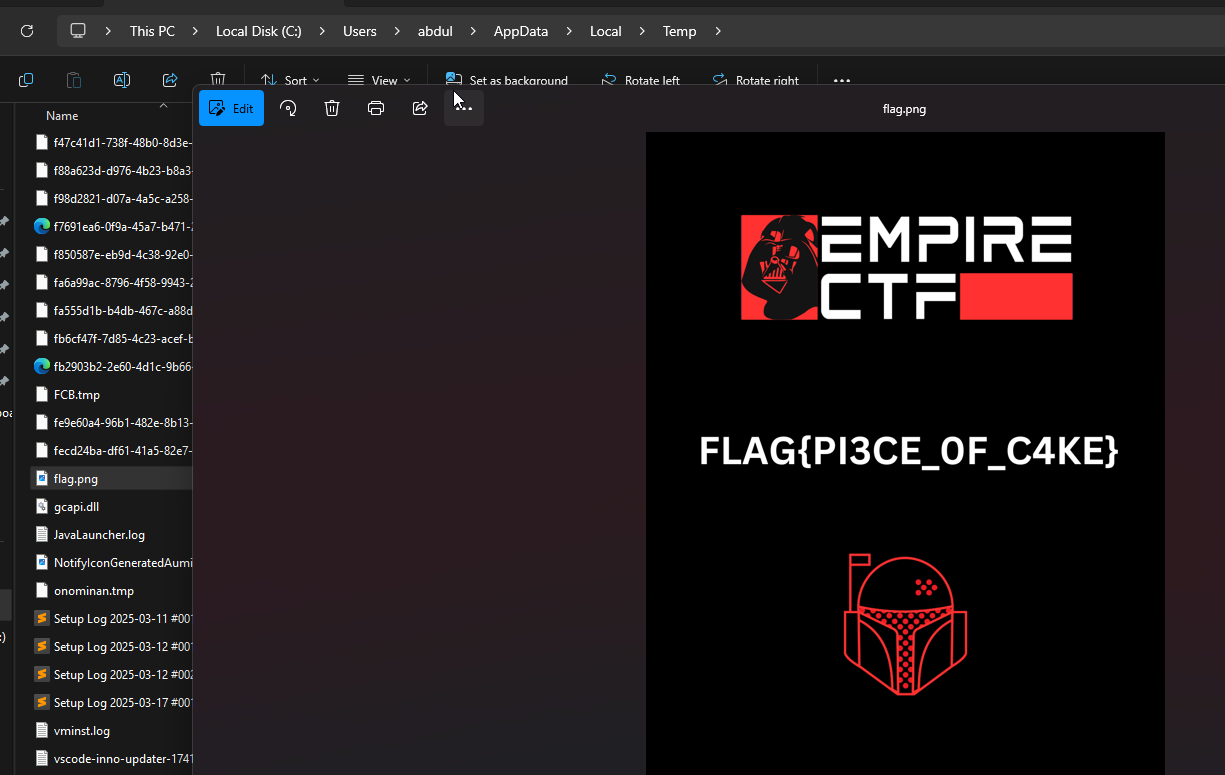
it gets temp path of the user and saves the flag to it
ADI
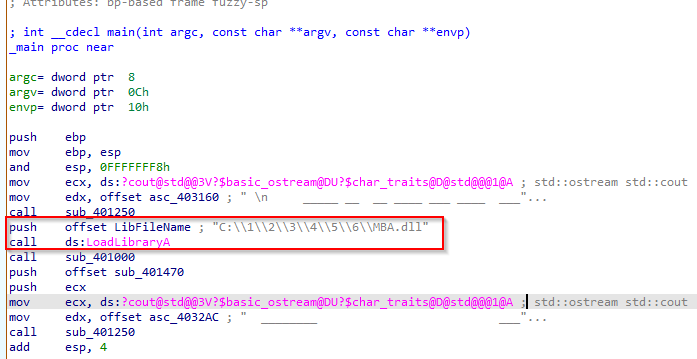
open the challenge executable in ida, here in the main you can see it is loading a dll, and its path is
C:\\1\\2\\3\\4\\5\\6\\MBA.dll
we are also given the dll, first we need to place the dll in C:\\1\\2\\3\\4\\5\\6 and rename the bcrypt.dll to MBA.dll
as it is a dll maybe it is loading some function from it or hooking a function
there is function being called right below LoadLibrary
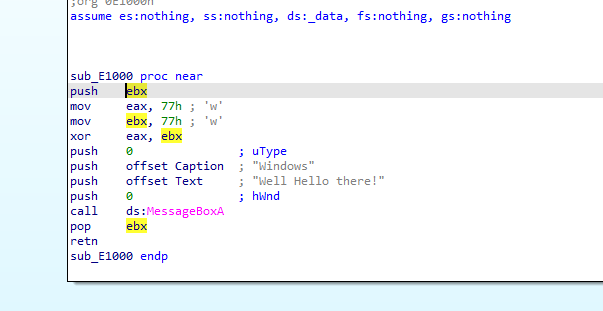
as a MessageBox was popping when we ran the exe, set a breakpoint on MessageBoxA and run through ida
follow the messagebox calls
it takes us to MBA where some xor operation is being performed
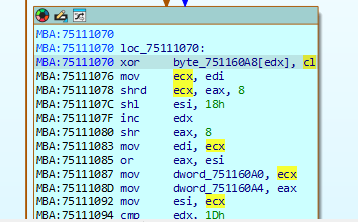
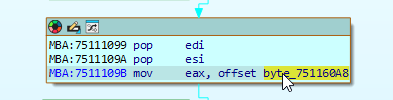
double click on byte_751160A8
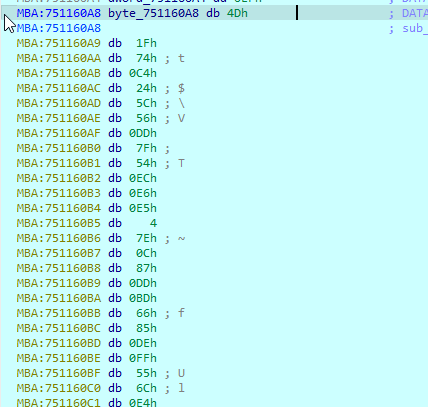
this is the data on which xor is being performed, extract this data
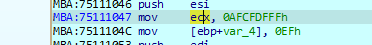
and key is in the ecx register
next when we further move down the function we can see ror
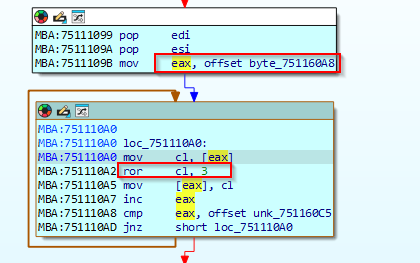
here it is performing ror with key 3 on the xor’ed data
so if we reverse the process we will get the unencrypted data
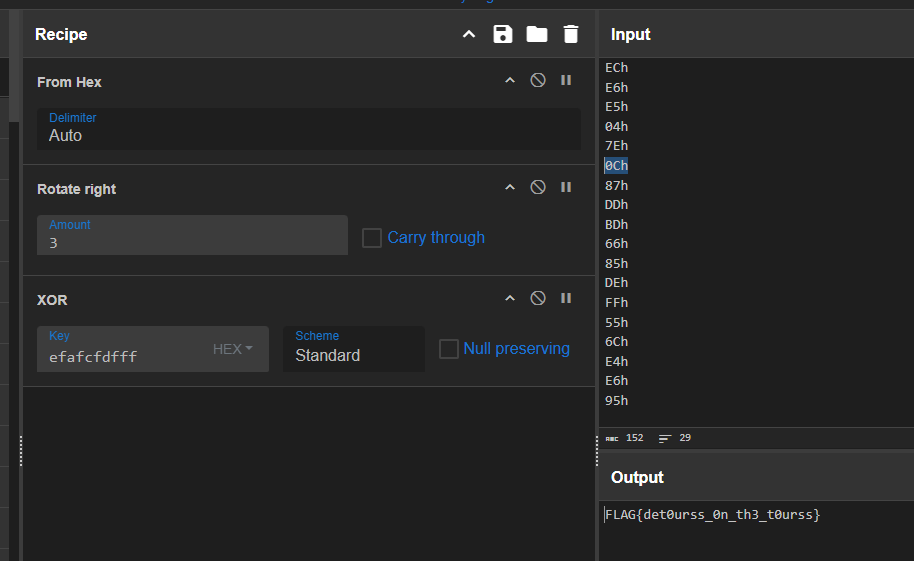
yoda
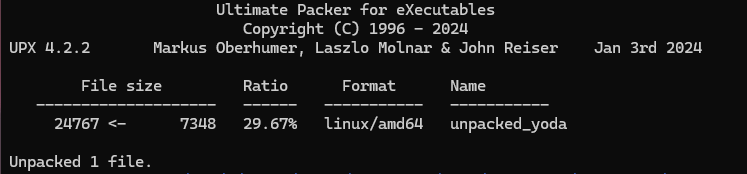
as there are no section header, it could be packed using upx, we need to unpack it using upx
upx -d -o unpacked_yoda yoda
now open the executable in ghidra
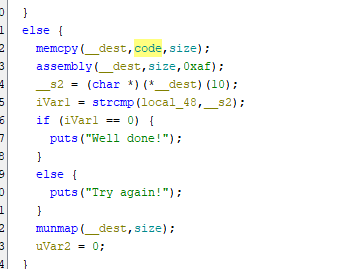
here you can see it is copying some code into memory, lets look at assembly function
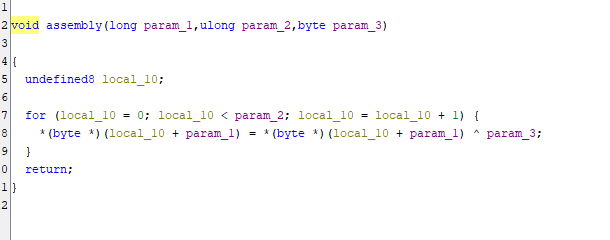
a the simple xor is being performed on the code which was copied to the memory using the key 0xaf
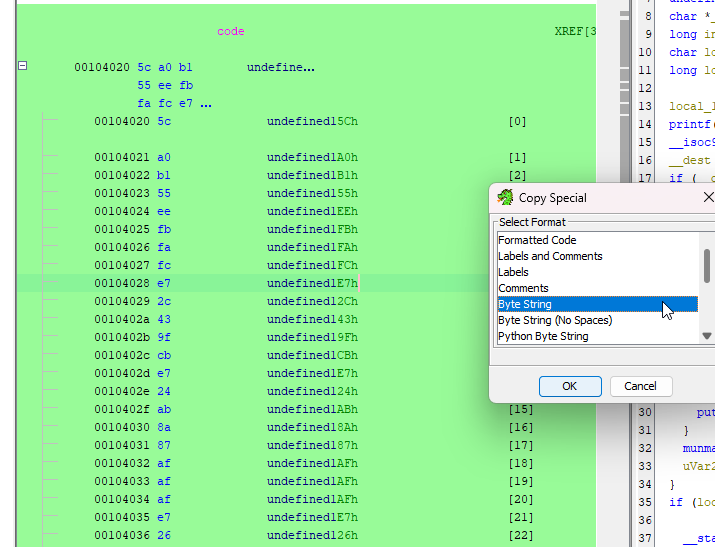
now double click on code and copy the values
select them, rightclick→copy special→bytestring
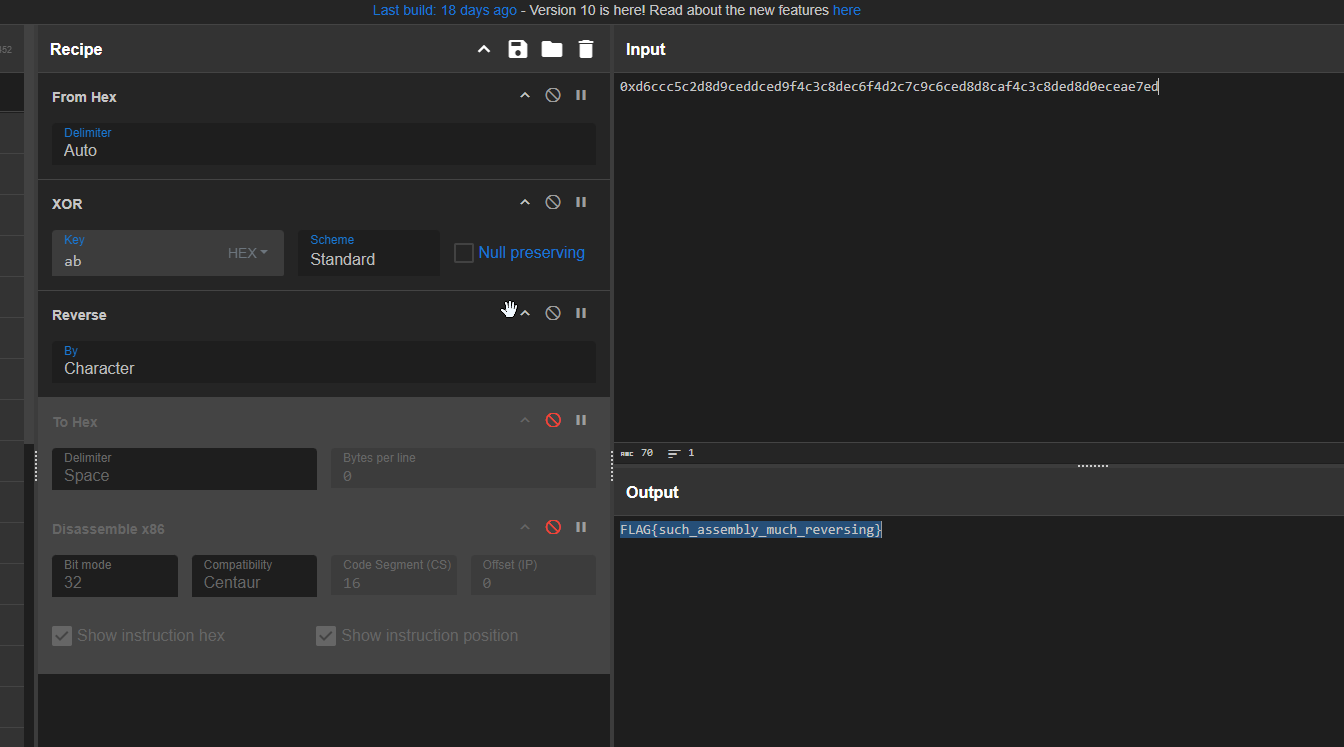
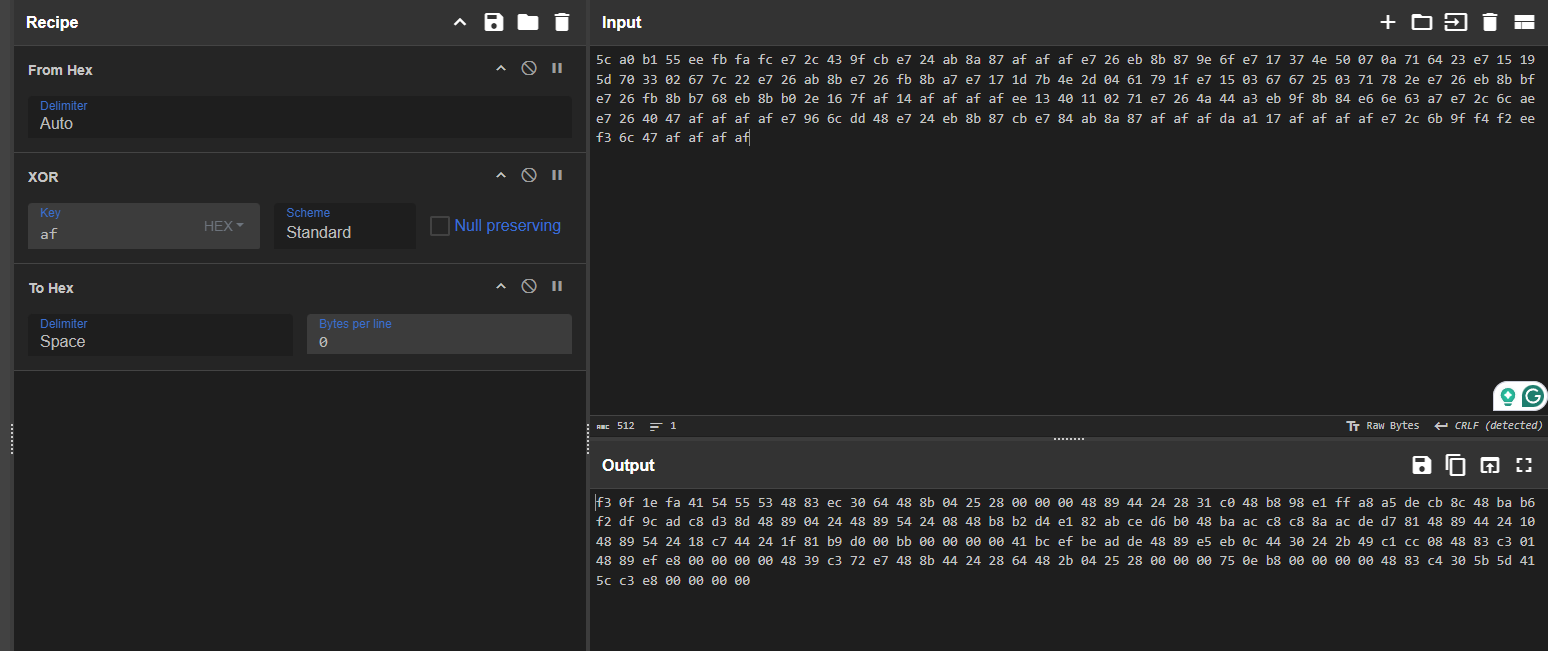
now lets use cyberchef to decode and xor it
as its was loading into memory and executed, this means this is a assembly code, to disassemble it we can use defuse.ca
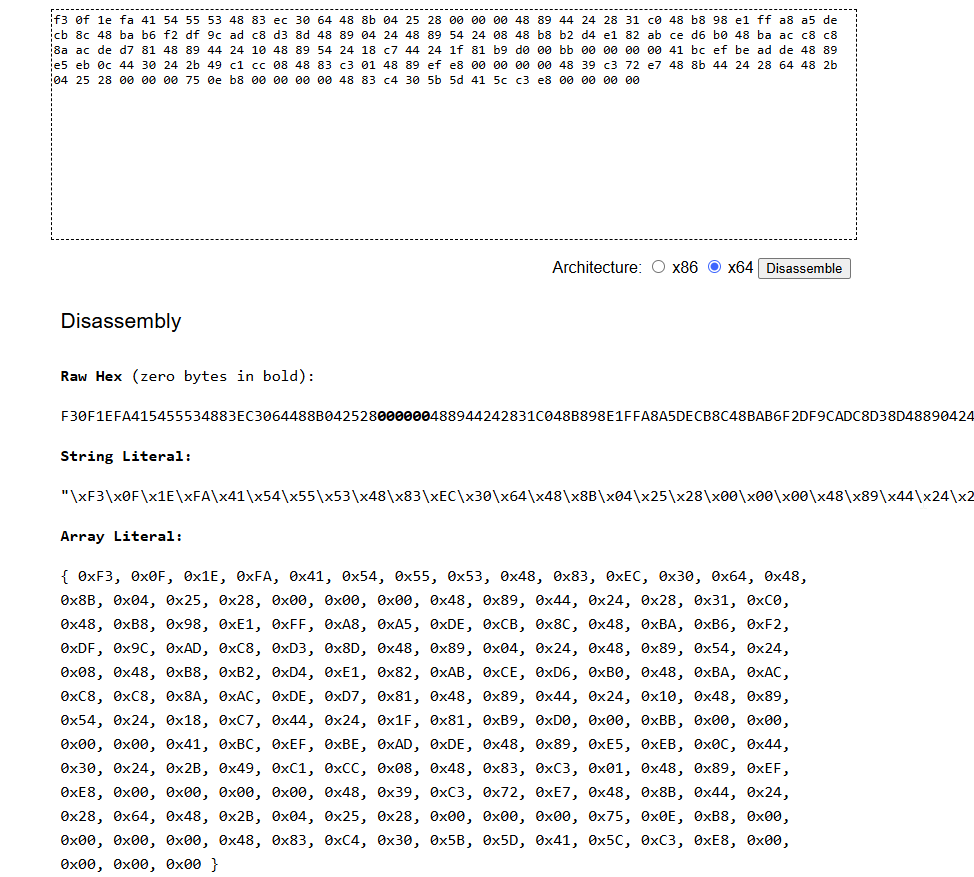
this is the disassembly we got
0: f3 0f 1e fa endbr64
4: 41 54 push r12
6: 55 push rbp
7: 53 push rbx
8: 48 83 ec 30 sub rsp,0x30
c: 64 48 8b 04 25 28 00 mov rax,QWORD PTR fs:0x28
13: 00 00
15: 48 89 44 24 28 mov QWORD PTR [rsp+0x28],rax
1a: 31 c0 xor eax,eax
1c: 48 b8 ed e7 ea ec d0 movabs rax,0xc8ded8d0eceae7ed
23: d8 de c8
26: 48 ba c3 f4 ca d8 d8 movabs rdx,0xc9c6ced8d8caf4c3
2d: ce c6 c9
30: 48 89 04 24 mov QWORD PTR [rsp],rax
34: 48 89 54 24 08 mov QWORD PTR [rsp+0x8],rdx
39: 48 b8 c7 d2 f4 c6 de movabs rax,0xf4c3c8dec6f4d2c7
40: c8 c3 f4
43: 48 ba d9 ce dd ce d9 movabs rdx,0xc5c2d8d9ceddced9
4a: d8 c2 c5
4d: 48 89 44 24 10 mov QWORD PTR [rsp+0x10],rax
52: 48 89 54 24 18 mov QWORD PTR [rsp+0x18],rdx
57: c7 44 24 1f c5 cc d6 mov DWORD PTR [rsp+0x1f],0xd6ccc5
5e: 00
5f: 48 89 e5 mov rbp,rsp
62: 48 89 eb mov rbx,rbp
65: 49 89 e4 mov r12,rsp
68: eb 07 jmp 0x71
6a: 80 70 ff ab xor BYTE PTR [rax-0x1],0xab
6e: 48 89 c3 mov rbx,rax
71: 4c 89 e7 mov rdi,r12
74: e8 00 00 00 00 call 0x79
79: 48 89 c2 mov rdx,rax
7c: 48 8d 43 01 lea rax,[rbx+0x1]
80: 48 29 eb sub rbx,rbp
83: 48 39 d3 cmp rbx,rdx
86: 72 e2 jb 0x6a
88: 48 8b 44 24 28 mov rax,QWORD PTR [rsp+0x28]
8d: 64 48 2b 04 25 28 00 sub rax,QWORD PTR fs:0x28
94: 00 00
96: 75 0e jne 0xa6
98: b8 00 00 00 00 mov eax,0x0
9d: 48 83 c4 30 add rsp,0x30
a1: 5b pop rbx
a2: 5d pop rbp
a3: 41 5c pop r12
a5: c3 ret
a6: e8 00 00 00 00 call 0xab
here we can see at line 1c to 57 some data is being moved on the stack
on line 6a the xored is being performed using the key ab
this the the recipe to get the flag